3GPP LTE MAC Layer - EventHelix.com
3GPP LTE MAC Layer - EventHelix.com
3GPP LTE MAC Layer - EventHelix.com
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systems<strong>LTE</strong> SecurityEncryption and Integrity Protection in<strong>LTE</strong>© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 1
<strong>LTE</strong> Security: Key Concepts<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsAuthentication• The <strong>LTE</strong> Network verifiesthe UE’s identity bychallenging the UT usethe keys and report aresult.• The network checks theresult against theexpected resultIntegrity• Signaling messagereceiver verifies that thereceived message isexactly the message thatthe transmitter sent• This is done using anintegrity checksum• Guards against “man inthe middle” attackswhere the sendersmessages andintercepted by a hackerand a modified messageis relayed to the receiverEncryption• The sender encrypts thedata with a secret keythat is only known to thereceiver• Only the receiver is ableto decode the message• Guards against hackerslistening in on the data© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 2
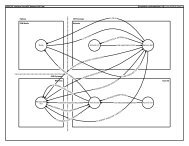
<strong>LTE</strong> Security Key Hierarchy<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsUSIM and AuCKUE and HSSCK, IKUE and MMEK ASMEUE and MMEK NASint K NASenc K eNBUE and eNodeBK UPenc K RRCint K RRCenc© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 3
Encryption and IntegrityProtection in the <strong>LTE</strong> Control Plan<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsMMENAS• K NASint• K NASenceNodeBRRC• K RRCint• K RRCencUENAS• K NASint• K NASencRRC• K RRCint• K RRCenc• <strong>LTE</strong> supports two levels onsecurity on the controlplane– The NAS traffic between theMME and the UE is protectedwith NAS level keys– The RRC connection trafficbetween the MME and theUE is protected with RRC levelkeys• This means that the NAStraffic is being protectedwith NAS as well as RRClevel security© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 4
Encryption and IntegrityProtection in the <strong>LTE</strong> UsereNodeBPlaneUE<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systems• User plane data isencrypted with theK UPenc keyUserPlaneUserPlane• K UPenc• K UPenc© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 5
<strong>LTE</strong> NAS Key Derivation atthe MME and UEK NASint : Integrity protection keyfor NAS signaling messages<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsK NASenc : Encryption key for NASsignaling messagesKKCK, IKCK, IKK ASMEK NASintK ASMEK NASenc© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 6
<strong>LTE</strong> RRC Key Derivation atthe eNodeB and UE<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsK RRCint : Integrity protection key for K RRCenc : Encryption key for RRCRRC signaling messagessignaling messagesKKCK, IKCK, IKK ASMEK eNBK RRCintK ASMEK eNBK RRCenc© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 7
<strong>LTE</strong> User Plane KeyDerivation at the eNodeBKCK, IKand UE<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systems• K UPenc : User planeencryption keyK ASMEK eNBK UPenc© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 8
Key Stream Computation<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsCipheringIntegrity ProtectionBearerMessageCountDirectionCountBearerKeyKeyStreamLengthKeyKeyStreamDirection© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 9
<strong>3GPP</strong> SecuritySpecifications<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systems<strong>LTE</strong> Security• 33.401: System ArchitectureEvolution (SAE); Security architecture• 33.402: System ArchitectureEvolution (SAE); Security aspects ofnon-<strong>3GPP</strong>Lawful Interception• 33.106: Lawful interceptionrequirements• 33.107: Lawful interceptionarchitecture and functions• 33.108: Handover interface forLawful InterceptionKey Derivation Function• 33.220: GAA: Generic BootstrappingArchitecture (GBA)Backhaul Security• 33.310: Network Domain Security(NDS); Authentication Framework(AF)Relay Node Security• 33.816: Feasibility study on <strong>LTE</strong> relaynode security (also 33.401)Home (e) Node B Security• 33.320: Home (evolved) Node BSecurity© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 10
Thank You<strong>EventHelix</strong>.<strong>com</strong>• tele<strong>com</strong>munication design• systems engineering• real-time and embedded systemsThank you for visiting <strong>EventHelix</strong>.<strong>com</strong>. The following links provide more informationabout tele<strong>com</strong> design tools and techniques:LinksEventStudio System DesignerVisualEther Protocol AnalyzerTele<strong>com</strong> Call FlowsTCP/IP Sequence DiagramsTele<strong>com</strong> • Networking • SoftwareDescriptionSequence diagram based systems engineeringtool.Wireshark based visual protocol analysis andsystem design reverse engineering tool.GSM, SIP, H.323, ISUP, <strong>LTE</strong> and IMS call flows.TCP/IP explained with sequence diagrams.Real-time and embedded systems, call flows andobject oriented design articles.© 2012 <strong>EventHelix</strong>.<strong>com</strong> Inc. 11