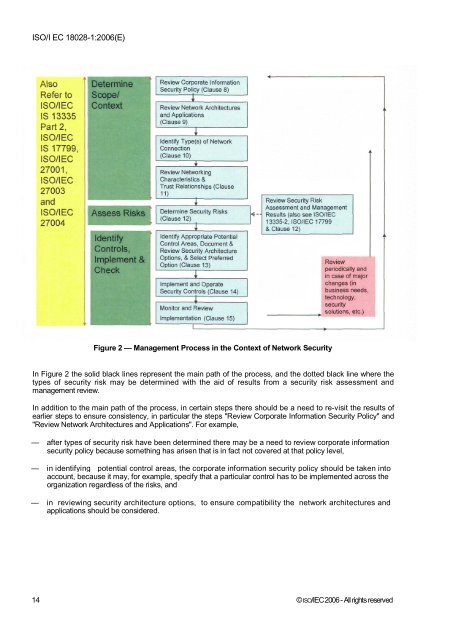
<strong>ISO</strong>/I EC <strong>18028</strong>-1:2006(E)Figure 2 — Management Process in the Context of Network SecurityIn Figure 2 the solid black lines represent the main path of the process, and the dotted black line where thetypes of security risk may be determined with the aid of results from a security risk assessment andmanagement review.In addition to the main path of the process, in certain steps there should be a need to re-visit the results ofearlier steps to ensure consistency, in particular the steps "Review Corporate Information Security Policy" and"Review Network Architectures and Applications". For example,— after types of security risk have been determined there may be a need to review corporate informationsecurity policy because something has arisen that is in fact not covered at that policy level,— in identifying potential control areas, the corporate information security policy should be taken intoaccount, because it may, for example, specify that a particular control has to be implemented across theorganization regardless of the risks, and— in reviewing security architecture options, to ensure compatibility the network architectures andapplications should be considered.14 © <strong>ISO</strong>/<strong>IEC</strong>2006 - All rights reserved
<strong>ISO</strong>/<strong>IEC</strong> FD1S <strong>18028</strong>-1:2006(E)8 Consider Corporate Information Security Policy RequirementsAn organization's corporate information security policy may include statements on the need for confidentiality,integrity, availability, non-repudiation, accountability, authenticity and reliability, as well as views on types ofthreat, and control requirements, that relate directly to network connections.For example, such a policy could state that:— availability of certain types of information or services is a major concern,— no connections via dial-up lines are permitted,— all connections to the Internet should be made through a security gateway,— a particular type of security gateway should be used, and— no payment instruction is valid without a digital signature.Such statements, views and requirements, being applicable organization or community-wide, should beaccounted for in the determination of the types of security risk (see Clause 12 below) and the identification ofpotential control areas for network connections (see Clause 13 below). If there are any such securityrequirements then these should be documented in the draft list of potential control areas, and as necessaryreflected in security architecture options. Guidance on the positioning of a corporate information securitypolicy document within an organization's approach to information security, and on its content and relationshipswith other security documentation, is provided in <strong>ISO</strong>/<strong>IEC</strong> 13335-1 and <strong>ISO</strong>/<strong>IEC</strong> 17799. Guidance will also beprovided in <strong>ISO</strong>/<strong>IEC</strong> 13335-2, when published.9 Review Network Architectures and Applications9.1 BackgroundAs referred to earlier in this standard, the steps to achieve confirmation of the potential controls required for anetwork are:— identification of the type(s) of network connection to be used,— identification of the networking characteristics and associated trust relationships involved,— determination of the security risks,— development of the list of required control areas e \ and the related designs.Following these steps should always be accomplished in the context of the network architecture andapplications that already exist or are planned.Thus detail should be obtained of the relevant network architecture and applications, and this should bereviewed to provide the necessary understanding and context for the process steps that follow.By clarifying these aspects at the earliest possible stage, the process of identifying the relevant securityrequirement identification criteria, identifying control areas, and reviewing the technical security architectureoptions and deciding which one should be adopted, should become more efficient and eventually result in amore workable security solution.The consideration of network and application architectural aspects at an early stage should allow time forthose architectures to be reviewed and possibly revised if an acceptable security solution cannot berealistically achieved within the current architecture.6) Including those control areas associated with the use of cryptography for such as confidentiality, integrity andauthentication.© <strong>ISO</strong>/<strong>IEC</strong> 2006 - All rights reserved 15