Xcon2005_Profiling_Malware_and_Rootkits_from_Ke..
Xcon2005_Profiling_Malware_and_Rootkits_from_Ke..
Xcon2005_Profiling_Malware_and_Rootkits_from_Ke..
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
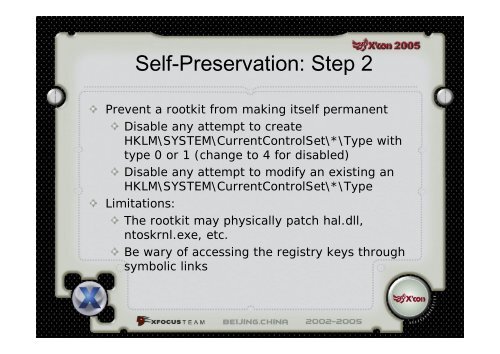
Self-Preservation: Step 2Prevent a rootkit <strong>from</strong> making itself permanentDisable any attempt to createHKLM\SYSTEM\CurrentControlSet\*\Type withtype 0 or 1 (change to 4 for disabled)Disable any attempt to modify an existing anHKLM\SYSTEM\CurrentControlSet\*\TypeLimitations:The rootkit may physically patch hal.dll,ntoskrnl.exe, etc.Be wary of accessing the registry keys throughsymbolic links