Wireless AMI Application and Security for Controlled Home Area ...
Wireless AMI Application and Security for Controlled Home Area ...
Wireless AMI Application and Security for Controlled Home Area ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
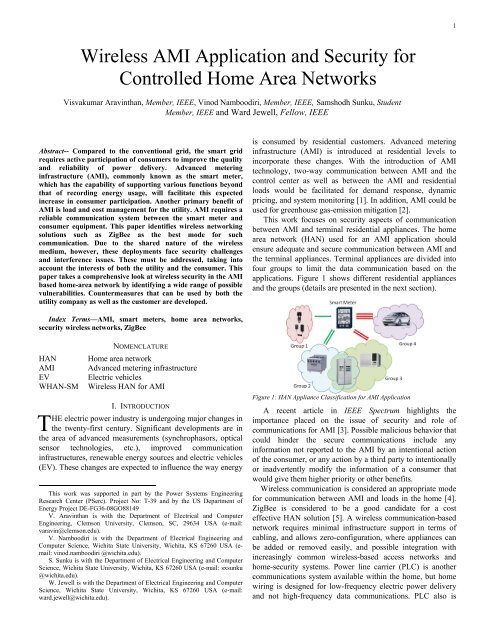
2unavailable when the home electric system is faulted or open.<strong>Wireless</strong> enables communication between <strong>AMI</strong> <strong>and</strong> the outlet,even with a fault in the electric connection between them.Comparatively, options like Ethernet cabling have extensiveinfrastructure costs with little flexibility to reconfigure thenetwork architecture.A wireless-based home area network <strong>for</strong> <strong>AMI</strong> (WHAN-SM)has more security challenges than possibly any other solutiondue to the shared wireless medium. There have been visionarydocuments on smart grids that call <strong>for</strong> improved security [6],[7]. There are researchers who have specifically focused onsecurity <strong>and</strong> <strong>AMI</strong> <strong>and</strong> called <strong>for</strong> more work to be done inensuring a secure framework, with some actually proposingsuch a framework or architecture [8] – [13] on which to buildsolutions. Based on a survey of the literature <strong>and</strong> discussionswith engineers <strong>and</strong> experts, what has been lacking, however, isa concrete, low-level approach that looks at various possibleattacks to such a WHAN-SM.This work takes a comprehensive look at wireless securityin WHAN-SM. Furthermore, countermeasures are developed<strong>for</strong> both the utility <strong>and</strong> the customer. A key aspect thatdifferentiates security in WHAN-SM from that inconventional HANs is that there are two different entitieswhose interests must be kept secure: (i) the utility company,who must be sure that no one, including the customer, cantamper with the measurement <strong>and</strong> control of appliances asagreed upon, <strong>and</strong> (ii) the customer, whose privacy must beguarded at all times when the <strong>AMI</strong> is collecting <strong>and</strong> relayingdata, <strong>and</strong> that personal appliance management preferences arehonored at all times. The traditional wireless local areanetwork security protocols are based on a single partyapplication. Very limited work has been done <strong>for</strong> wirelesslocal area network security solutions under the presence ofmore than one stakeholder. This work pays special attention topossible attacks <strong>and</strong> countermeasures needed with theexistence of these multiple parties.The paper is organized as follows. In Section II, a moredetailed description is given of the WHAN-SM scenario.Section III looks at relevant security objectives in WHAN-SM<strong>and</strong> discusses possible attacks. In Section IV, solutions to theidentified attacks are proposed. Concluding remarks withsome directions <strong>for</strong> future work are made in Section VI.II. HOME AREA NETWORK FOR <strong>AMI</strong>SThe <strong>AMI</strong> will enable energy meters installed in all customerpremises to communicate with the utility operated controlcenter <strong>and</strong> with appliances installed in the premises, <strong>and</strong> tocontrol the appliances’’ operation. The future <strong>AMI</strong> will havethe ability to control how many appliances could operate at agiven time <strong>and</strong> thus implement dem<strong>and</strong>-side management <strong>for</strong>the utility. In such an application the utility control centerlooks at aggregate loads from all its customers at a given time<strong>and</strong> then issues specific control instructions to the <strong>AMI</strong>s. It isenvisioned that in the future when a customer participates in<strong>AMI</strong>, the <strong>AMI</strong> would have control over some specific class ofappliances (typically the high-load appliances that thecustomer can operate with some tolerance in delay). It isexpected that with introduction of <strong>AMI</strong>s, time of the daytariffs will become more popular, allowing customers tobenefit from having appliances operate at times of lower tariff.If control is done manually consumers are less attentive tovarying tariffs <strong>and</strong> thus less likely to optimize the energy costby using appliances at off-peak times [14]. Any infrastructurethat allows reduced human intervention in energy costoptimization is of high interest.A. Role of Communication<strong>AMI</strong>s are expected to introduce two new categories ofcommunication. The first, already employed by many utilitiesin the U.S., is between the energy meter <strong>and</strong> the utility controlcenter. This facilitates observation of real-time powerconsumption <strong>and</strong> any abnormalities in the system, <strong>and</strong> allowsdem<strong>and</strong>-side management. If real-time pricing in introduced,this category of communication will enable the consumer totrack the current price. In addition to the ANSI C12.22st<strong>and</strong>ard [15], significant work has been done on ensuringsecure communication between the meter <strong>and</strong> the utility [16],[17]. Many utilities in the U.S. have implemented <strong>AMI</strong> thathave the capability of this level of communication [18]-[20].If the <strong>AMI</strong> is to allow load <strong>and</strong> cost management, a secondcategory of communication between the meter <strong>and</strong> the users’appliances is also necessary. One of the major concerns ofimplementing this category of communication is the questionof consumer privacy [3], [21]. Customers have concerns aboutthe utility knowing what electrical appliances they are using atany given time. There<strong>for</strong>e, a separate layer of communication,limited to the customer facility, is required. Using thiscommunication layer, the <strong>AMI</strong> will communicate with <strong>and</strong>control the customer’s appliances without sharing thisin<strong>for</strong>mation with any other stakeholders.It should be noted that if the second layer of control isachieved by enabling dem<strong>and</strong>-side management, thengreenhouse gas emissions can be also controlled as well.Utilities subject to existing <strong>and</strong> proposed state <strong>and</strong> federalemissions regulations could benefit greatly.Further, the introduction of electric vehicles (EV) is aserious concern <strong>for</strong> utilities. EV charging will be stochastic innature <strong>and</strong> a large increased load on the distributiontrans<strong>for</strong>mers. There<strong>for</strong>e, EVs require higher level bidirectionalhigher end communication; some of thein<strong>for</strong>mation about EV charging should be communicated tothe utility (e.g. time required <strong>for</strong> charging, availability, <strong>and</strong>charge level of the battery). There<strong>for</strong>e EVs should becategorized separately when the communication architecture isdeveloped. As this scenario is still only emerging, we do notaddress this appliance class in this work. This work focuses onthe network within the home <strong>and</strong> how <strong>AMI</strong> deals withappliance classified in groups 1, 2, <strong>and</strong> 3, as described inFigure 1.B. Communication Requirements in a WHAN-SMIt may not be economical to have equal communicationcapability <strong>for</strong> all components; <strong>for</strong> example, a light bulb needsonly minimal communication infrastructure whereas an airconditioner needs to communicate more in<strong>for</strong>mation.
3Communication needs are used to divide components into thefour categories of Figure 1.Controlling small loads such as light bulbs, phone chargers,<strong>and</strong> laptop computers will significantly increase theinstallation cost <strong>and</strong> data traffic. Since control of these loadswill not change the total load profile significantly, these Group1 loads need to in<strong>for</strong>m the control center only when they areconnected to <strong>and</strong> disconnected from the system. Group 2consists of large loads, such as stoves, that will not becontrolled because the consumer needs them to be available asneeded, not delayed to a later time. This type of applianceneeds minimal communication infrastructure, but will need tosend its power usage <strong>and</strong> expected duration of usage wheneverpossible.Group 3 loads are large loads, such as air conditioners <strong>and</strong>clothes washers <strong>and</strong> dryers, <strong>for</strong> which usage will be controlled.These loads will send a request through <strong>AMI</strong> <strong>and</strong> wait <strong>for</strong>acceptance be<strong>for</strong>e operating. They will need to send extensivein<strong>for</strong>mation such as expected load, expected duration of usage,<strong>and</strong> duration of availability. There<strong>for</strong>e, they may send moredata packets than the other two types of loads. Furthermore,the acknowledgement from the <strong>AMI</strong> is essential <strong>for</strong> this typeof load as they wait to begin operation. The decision tooperate a component will depend on dynamic pricing <strong>and</strong>duration of availability. Depending on the customer’sagreement with the utility, they will likely be able to overridea delay in operation by paying a higher energy price.Group 4 loads, EVs, are new to the power grid. Since theseare very large <strong>and</strong> stochastic in nature, it is vital <strong>for</strong> the <strong>AMI</strong>to communicate in advance the time of charging of EVs <strong>and</strong> toplan the charging. Due to the extensive need <strong>for</strong>communication, these are categorized as separate loads. It isessential to build a communication architecture that canmanage this new load through timely <strong>and</strong> adequate control.C. Communication <strong>and</strong> Control Model in a WHAN-SMThere are two options <strong>for</strong> communications betweenappliances <strong>and</strong> the <strong>AMI</strong>. The first option is to make appliancessmart, whereby they will have the capability to communicatewith the <strong>AMI</strong> <strong>and</strong> make the decisions (when to switch on,when to switch off, etc.). The main disadvantage of thismethod is the lack of communication/processing capability incurrently manufactured appliances. The second option is tomake the power outlets smarter by connecting a transceiverwith processing capability. The work in this paper is based onthis second option because it can be implemented withexisting appliances. Migrating to the first option in the futureas smart functions are added to appliances will not change thecommunications security concerns, <strong>and</strong> will allow thoseappliances to be designed to a st<strong>and</strong>ard developedimmediately. Figure 2 shows two different models <strong>for</strong> theoutlet communication model.The first model (Figure 2a) is <strong>for</strong> controlled operation; thisis <strong>for</strong> appliances clustered in group 3, which need approvalfrom the <strong>AMI</strong> to operate. The consumer will connect theappliance to the power outlet <strong>and</strong> program the outlet with thefollowing in<strong>for</strong>mation: required operation, availability, <strong>and</strong>priority. This in<strong>for</strong>mation will be communicated to the <strong>AMI</strong>,<strong>and</strong>, based on the system loading profile <strong>and</strong> the in<strong>for</strong>mationprovided by the consumer, <strong>AMI</strong> will allocate the time ofoperation of the appliance <strong>and</strong> send that in<strong>for</strong>mation back tothe outlet transceiver. On the other h<strong>and</strong>, <strong>for</strong> the group 1 <strong>and</strong> 2appliances, which will not be controlled by the <strong>AMI</strong>, the onlyin<strong>for</strong>mation the <strong>AMI</strong> needs is the type of appliance (whichcould be identified by location of the outlet). Figure 2b showsuncontrolled operation; once the consumer switches on theappliance, the outlet will share this in<strong>for</strong>mation with the <strong>AMI</strong>.(a) <strong>Controlled</strong> Outlet(b) Uncontrolled OutletFigure 2: Communication <strong>and</strong> Control Enabled Power OutletsA downside to using wireless communication <strong>for</strong> theWHAN-SM scenario could be the data transfer rate, which canbe slower than wired solutions. However, a WHAN-SM isused more <strong>for</strong> control than as a high-speed access network,<strong>and</strong> thus, lower data rates are adequate. Current wirelesssolutions that are possible c<strong>and</strong>idates <strong>for</strong> WHAN-SM are Wi-Fi, ZigBee, <strong>and</strong> Bluetooth, <strong>and</strong> their comparison can be foundin [22]. The ZigBee technology based on the IEEE 802.15.4st<strong>and</strong>ard [23] is considered a good solution <strong>for</strong> the WHAN-SM scenario as it has a communication range varying from10-100m, allows large-scale network configurations, <strong>and</strong> usesa low-power radio. The data rate capability <strong>for</strong> this technologyis a modest 250kbps, but is more than adequate <strong>for</strong> theWHAN-SM application scenario. As a result, ZigBee seems tobe the front runner in the race to be the wireless solution ofchoice. Thus, this work makes periodic references to thesecurity architecture in place <strong>for</strong> ZigBee; however, <strong>for</strong> themost part, a general wireless network is assumed that couldbe based on any of the above solutions. The work in [24]presents an integration point <strong>for</strong> different types of wirelessnetworks <strong>for</strong> HAN through unified metrics that could beutilized to implement any of the proposed general solutions.III. POSSIBLE SECURITY ATTACKSPossible security attacks in a wireless local area networkwere investigated <strong>and</strong> the possible attacks <strong>for</strong> a smart meterapplication are identified <strong>and</strong> presented in this section. Each ofthe attacks is illustrated in terms of a WHAN-SM. The twopartydynamics that exist in the WHAN-SM scenario <strong>and</strong>related challenges are also discussed. The security objectivesof the network <strong>and</strong> possible attacks it could face are definedlater in this work.A. Two Party DynamicsIn traditional home area-based networks the customer is theonly entity responsible <strong>for</strong> the operation of the network <strong>and</strong>acquiring benefits from the deployed applications. For
4example, consider the case of a home surveillance system. It isin the interests of the customer that the network functionsproperly as intended. The customer must correct anyunintended behavior of the network.The WHAN-SM scenario has the additional dynamic ofthere being two parties with interests in the network. If theWHAN-SM does not function properly, it could preventcontrolled appliances from operating at request. Similarly, amisbehaving network could take away the ability to manageload based on the utility requirements.Further, the distributed control that exists between the twoconcerned parties could allow a third party to threaten thesecurity of the network by impersonating one or the otherparty, or both. It should be noted that capturing shared secretsis easier when more than one party is involved.B. <strong>Security</strong> ObjectivesOut of the typical security concerns in a wireless network[23], the following five main objectives were identified toensure a secure WHAN-SM:Confidentiality: The goal of confidentiality is to ensure thatany sensitive data is not disclosed to parties other than thoseinvolved in the communication process. In the WHAN-SMscenario this could mean that apart from the customer <strong>and</strong>utility, no other party gets access to the appliance usagebehavior of the customer. Further, the customer would preferthe utility to have only an aggregate view of power consumed.Integrity: This requirement is to ensure that a receivedmessage is not altered from the way it was transmitted by thesender. In the WHAN-SM scenario, this is important to allowtimely <strong>and</strong> accurate control. If an attacker manages to changethe source of the request, it could happen that the <strong>AMI</strong> ends upcommunicating <strong>and</strong> controlling the wrong appliance.Authentication: Authentication is used by one node toidentify another node or verify the source of origin of data inthe network. Authentication is important <strong>for</strong> administrativetasks like association, beaconing, <strong>and</strong> identifier collision. Thisis critical in the WHAN-SM scenario to ensure that a customeris sure of the authenticity of an <strong>AMI</strong> with which its applianceis communicating, <strong>and</strong> <strong>for</strong> the <strong>AMI</strong> to ensure that it iscommunicating only with the assigned customer’s appliance.Availability: This property is to ensure that network servicesare available <strong>and</strong> will survive possible attacks or failures thatcould occur. In the WHAN-SM scenario, resource depletion istypically not a concern when it comes to a resource likeenergy which both the <strong>AMI</strong> <strong>and</strong> appliances are assumed tohave access to through power outlets. But computationcapabilities <strong>and</strong> memory constraints could be exploited bykeeping these resources fully loaded, affecting the ability ofthe network to function as desired. Equipment failures mayalso be more common, especially with the low cost ofWHAN-SM radios.Time Sensitivity: Any message delayed over a specifictolerable time frame may be of no use. A network must ensurerelevance of communication by en<strong>for</strong>cing latency constraints.In the WHAN-SM scenario, a customer request <strong>for</strong> applianceoperation must reach <strong>AMI</strong> in a timely manner; similarly,control comm<strong>and</strong>s from <strong>AMI</strong> to appliances must be timely toensure scheduling practices of the utility.<strong>Security</strong> objectives such as fairness, which are common tomore general wireless networks, are not applicable in WHAN-SM scenario, as all appliances that compete <strong>for</strong> access to themedium belong to the same customer. Further, the WHAN-SM network is expected to be used mainly as a controlnetwork <strong>and</strong> is not expected to be highly loaded in terms ofb<strong>and</strong>width, thus providing no incentives <strong>for</strong> selfish behaviorby nodes.C. Attacks <strong>and</strong> Misbehavior Scenarios <strong>for</strong> WHAN-SMFigure 3 shows possible attacks on a WHAN-SM. Theseattacks are classified as local or remote attacks. The scope ofthis work is limited to local attacks within the HAN where allappliances communicate to their <strong>AMI</strong>s using a one-hopnetwork from their power outlets. Remote attacks, whichtypically exploit weaknesses in the routing mechanisms <strong>and</strong>multi-hop nature of networks, will not occur in the WHAN-SM scenario.Figure 3: List of attacks on <strong>Wireless</strong> HAN scenario.Various attack scenarios are considered with the followingassumptions:(i) The customer is provided with a password by the utility<strong>for</strong> authentication. A common authentication procedure,outlined in Section IV, is assumed <strong>for</strong> appliances to jointhe network <strong>and</strong> prevent unauthorized access.(ii) The available encryption level is strong. This is a st<strong>and</strong>ardassumption, <strong>and</strong> could be based on a stronger encryptionsuite present in technologies like ZigBee.As a result of these precautions <strong>and</strong> assumptions anyauthentication <strong>and</strong> snooping type of attacks from Figure 3 canbe ruled out. Local denial-of-services are typically based onde-authentication attacks that <strong>for</strong>ce appliances to repeatedlyre-authenticate instead of using the network <strong>for</strong> usefulpurposes. Instead of considering such denial-of-serviceattacks, this work focuses on the stronger attack of jamminglater in this section.Physical device tampering with the <strong>AMI</strong>, appliance, orpower outlet are not considered in this work. The <strong>AMI</strong> couldbe made tamper proof by periodic communication with the
5control center that allows adequate monitoring of itsoperations. The case of customer appliance <strong>and</strong> power outlettampering would be h<strong>and</strong>led in the attack category of “deviceimpersonation,” discussed later in this section.The rest of this section describes the attacks which arerelevant to WHAN_SM in Figure 3 in more detail. Theseattacks are a representative set of attacks possible in theWHAN-SM scenario.1) Jamming Attacks: In these attacks, an adversary disruptscommunications in a wireless network by sendingdeliberate signals on the shared medium. In a wirelessnetwork, packet communication is successful only if areceiver is able to successfully decode the sender’spacket. If the medium is jammed by an adversary, thesender cannot begin communicating (if it senses themedium to be busy be<strong>for</strong>eh<strong>and</strong>) or its transmitted packetwill be corrupted by the adversary’s signal when received.Jamming can be carried out by sending a continuous orintermittent busy tone on the channel used <strong>for</strong>communication. A simpler <strong>for</strong>m of jamming is <strong>for</strong> anadversary to send a continuous stream of packets usingthe same wireless technology, but at a much higher datarate, possibly after tampering with the medium accesscontrol protocol to gain an unfair advantage [25]. Basedon the investigation carried out <strong>for</strong> a six node scenariousing the NS-2 simulator [26] it was found that a jammercould reduce each node’s packet delivery ratio from 80-90% to about 40% by just using a data rate 10 times thatof an average node with a data rate of 100 kbps on a 2Mbps channel.It is fairly simple <strong>for</strong> an adversary to use a signal analyzeror similar device based on common off the shelfcomponents to determine the channel used in a network.Such attacks are the most difficult to defend against <strong>and</strong>could cripple a HAN based on a wireless architecture.2) Appliance Impersonation: Based on the customer-utilityagreement, the customer agrees to let the utility control agroup of their appliances. However, there could beinstances where the customer would want to renege onthis agreement <strong>and</strong> not relinquish control. This couldoccur, <strong>for</strong> example, when a customer tries to control theair conditioning <strong>for</strong> better com<strong>for</strong>t.Under the customer-utility agreement, the utility controlsappliances from only a certain subset of classes, typicallythose that consume a lot of power. The customer couldthere<strong>for</strong>e exploit this fact <strong>and</strong> have a high powerconsuming appliance impersonate an appliance fromanother non-controlled class. For the utility, an inability tocontrol the appliance could result in dem<strong>and</strong> exceedingsupply, possibly resulting in a blackout in parts of thegrid.The details of the attack are shown in Figure 4 where acustomer masquerades their air-conditioner as atelevision. This attack is one example of vulnerabilitiesarising out of the two party dynamic where one partymight try to cheat the other.3) Replay Attack: A neighbor could capture an appliancerequest made at some other time by a customer <strong>and</strong> replayit another time when no actual request was made. Theneighbor does not gain any benefit, but it can hurt thecustomer, <strong>and</strong> could even be a safety hazard. Such fakerequests could overload the <strong>AMI</strong> <strong>and</strong> have repercussionson the whole grid due to overloading if not h<strong>and</strong>ledproperly.4) Non-repudiation: Non-repudiation is a concept wherebyno party can refute some aspect of their participation inthe communication process. Specific to the WHAN-SMscenario, the customer cannot later refute having receivedcertain control messages from the <strong>AMI</strong> to operate theirappliance. Alternately, an <strong>AMI</strong> cannot later deny how ittried to control a customer appliance.Figure 4: Example of an Appliance Impersonation AttackIV. SECURITY SOLUTIONSTo ensure a reliable WHAN-SM, security attacks must beprevented. This work focuses on developing solutions to thesesecurity attacks based on the operating conditions of theelectric power system at the residential level, <strong>and</strong> conventionalwireless local area network applications.Solutions developed by the authors to overcome each of theattacks identified in the previous section are presented in thissection. An authentication procedure that will <strong>for</strong>m the basisof the solution to all attacks is presented first.A. Authentication ProcedureTo ensure strong authentication the following key distributionalgorithm is assumed:1. The <strong>AMI</strong> is installed by the utility at the customerpremises. The customer is given a password to bemanually supplied to the power outlet through which anyappliance is supplied. This password can be used togenerate a public-private key pair <strong>for</strong> encryptionpurposes.2. The power outlet <strong>for</strong> any appliance that connects to thenetwork <strong>for</strong> the first time is challenged by the <strong>AMI</strong> <strong>for</strong> thepassword. A correct response authenticates the applianceto the <strong>AMI</strong> <strong>and</strong> sets up the required bi-directional controlbetween the <strong>AMI</strong> <strong>and</strong> the power outlet. The
6communication in this step can use a public keycryptographic technique.3. The <strong>AMI</strong> <strong>and</strong> the authenticated power outlet with thenewly joined appliance now decide on whether to use theestablished encryption keys or to generate new ones on aper-session basis.When an appliance tries to authenticate <strong>and</strong> join thenetwork, it uses the pre-defined authentication channel. Onceauthenticated it moves to a different data channel used by the<strong>AMI</strong>. The <strong>AMI</strong> is assumed to have two interfaces, one <strong>for</strong>receiving authentication requests, <strong>and</strong> another <strong>for</strong>communication with authenticated devices. Any attacks aimedat preventing authentication can be h<strong>and</strong>led manually as theseare rare <strong>and</strong> customer involvement can be expected at a timewhen appliances are added. As mentioned in Section III, itwould be safe to assume that a customer can be trusted to keepthe utility assigned password safe.B. JammingJamming is one of the most difficult denial of serviceattacks to defend against. The best defense against intentionaljamming is the use of multiple alternate frequency channels ifthe current channel has significant interference that results inpacket losses above a certain threshold. The <strong>AMI</strong> <strong>and</strong> anynodes deployed can be hard-coded to move through a predefined<strong>and</strong> common r<strong>and</strong>om sequence of channels, ifcommunication on the default channel is unsuccessful <strong>for</strong> aspecified period.The nature of the WHAN-SM scenario is different fromtypical wireless sensor network research problems. Batteryenergy is not a constraint due to access to power outlets <strong>for</strong>charging. Hence, each packet could possibly be re-transmittedmultiple times <strong>and</strong> on multiple channels until it succeeds.The <strong>AMI</strong>, being a high functionality node compared totypical customer nodes, could be equipped with more spreadspectrum capabilities that could reject interference to a greaterdegree, <strong>and</strong> possibly help monitor the network <strong>and</strong> call <strong>for</strong>manual intervention. Directional reception taking into accountappliance locations in the residence <strong>and</strong> appropriate <strong>AMI</strong>placement can further mitigate the impact of jamming.The approach shown in Figure 5 is proposed to move theentire network through a sequence of predefined channels,which could mitigate the impact of a jammer.Each <strong>AMI</strong> on deployment will have a pre-defined sequenceof channels through which it moves as a function of time.When a new node authenticates to the network on the controlchannel, the <strong>AMI</strong> sends the encrypted channel sequence to thenode using the customer’s public key. Each node can thendecrypt using the customer’s private key <strong>and</strong> adopt thesequence, beginning with the current data channel being used.Methods <strong>for</strong> generating <strong>and</strong> exchanging pseudo-r<strong>and</strong>omsequences using public key encryption are well known [27],with the U.S. National Institute <strong>for</strong> St<strong>and</strong>ards <strong>and</strong> Technology(NIST) offering several st<strong>and</strong>ards from which to pick [28]. Ifsuch pseudo-r<strong>and</strong>om sequences are used, the jammer can atbest make a guess on what channel will be used, with priorhistory of channels used being of no help.Depending on tolerable complexity <strong>and</strong> cost factors,additional protections like directional reception capabilitiescould be used at the <strong>AMI</strong> <strong>and</strong> possibly the nodes at the poweroutlet. It is important to note that in technologies like ZigBee,the physical layer is based on Direct Sequence SpreadSpectrum (DSSS) [23] which provides some protection againstnoise on a channel.The proposed channel switching algorithm complementsthis by moving across channels as well to avoid attacks basedon overloading a specific channel with data 1 . This approach isdifferent than the one in [29] which assumes that somecommunication is possible between the <strong>AMI</strong> or networkcoordinator <strong>and</strong> nodes to move to a different channel uponinterference. The proposed scheme assumes the worst casethat communication may not be possible under a strongjamming scenario, <strong>and</strong> thus is more resilient.C. Load profiling algorithm to prevent impersonationDevice impersonation, as mentioned in the previous section,could be done by a customer to bypass stringent control onsome appliance on an as-needed basis. This prevents the utilityfrom having dem<strong>and</strong> side management control. A loadprofiling scheme is proposed whereby the <strong>AMI</strong> compares the adevice’s load profile to the type of device it is announced tobe. This is based on the premise that different appliances ordevices have unique signatures that can be exploited toidentify them. A simple experiment collecting power values ofcommon household appliances with a power meter supportsthis premise as shown in Figure 6.Figure 6: Appliance Loading PatternsFigure 5: Channel Switching Algorithm1 This makes the proposed scheme mimic the behavior of Frequency HoppingSpread Spectrum (FHSS) which is not possible under ZigBee’s underlying802.15.4 st<strong>and</strong>ard specifications. ZigBee defines a Frequency Agilitycapability, <strong>and</strong> this algorithm can be used to implement this capability.
7Figure 7: Load profiling algorithm to counter the possibility of device impersonation.Figure 7 shows the sequence of steps that will be taken bythe appliance, the power outlet, <strong>and</strong> the <strong>AMI</strong>. On receiving anappliance operation request, the power outlet seeks permissionfrom the <strong>AMI</strong>. Based on the advertised class of device thatneeds to be operated, the <strong>AMI</strong> either allows operation (<strong>for</strong>class 1 <strong>and</strong> 2), or schedules operation based on current load itis h<strong>and</strong>ling (<strong>for</strong> class 3 <strong>and</strong> 4). For all cases, the <strong>AMI</strong> sends apreviously <strong>for</strong>med load profile of the advertised device to thepower outlet <strong>for</strong> verification.If the peak load of the currently operating device (L current ) ishigher than the known peak of the advertised device L byfactor δ, or if the loading pattern does not match the knownprofile, the power outlet does not allow device operation.Each device’s profile can be pre-stored based onmanufacturer’s data, or verified against prior device operationhistory.D. Replay AttackReplay attacks, where a neighbor requests operation of acustomer’s device, can be prevented using timestamps, packetsequence numbers, or session keys. If the network is timesynchronized,each packet can include the time at which it wassent. If the <strong>AMI</strong> sees a packet that differs significantly fromthe current time, it can ignore it. Similarly, if packets fromeach appliance’s power outlet have sequence numbers, the<strong>AMI</strong> can filter packets significantly out of sequence. The useof session-based keys can also catch replayed packets, but thisis more complex than the timestamp or sequence numbermethods. If the overall security framework uses session basedkeys, then additional mechanisms will not be needed toprevent replay attacks.Figure 8 shows an example scenario where the <strong>AMI</strong> coulddetect the presence of a replay attack by monitoring sequencenumbers of packets sent from the power outlet of an appliance.Timestamp based approaches would work similarly.Figure 8: The sequence number technique to detect packet reply attacksE. Non-RepudiationIn the proposed approach, non-repudiation can be achievedby ensuring that customers <strong>and</strong> the <strong>AMI</strong> use unique keys <strong>for</strong>encryption, possibly after initial authentication using preassignedpublic-private key pairs. Further, the <strong>AMI</strong> would berequired to keep a log of all communication <strong>for</strong> a specifiednumber of days. If either party files a complaint, the logs canbe used to trace back events. Regulations will need to been<strong>for</strong>ced to ensure that the utility does not tamper with theselogs <strong>and</strong> are available <strong>for</strong> third party investigations.V. CONCLUSIONS AND FUTURE WORKThis work presents a secure framework <strong>for</strong> smart meteringin a wireless home area network scenario. Such a frameworkwas designed by first examining the communicationrequirements <strong>for</strong> <strong>AMI</strong> in the WHAN-SM scenario <strong>and</strong> thenstudying the security challenges that had to be addressed.First the security objectives to be met were identified, <strong>and</strong>then possible attacks <strong>and</strong> vulnerabilities were outlined. Basedon the two stakeholder objective, residential electric usage <strong>and</strong>conventional wireless local area network security protocols,
8solutions to these attacks were developed. Though morethreats are possible as this application scenario matures, thefoundation laid by this framework can be used to add newsolutions to emerging threats.Due to space limitations the overall framework ofimplementation could not be presented in this manuscript. Acommon security framework against the indentified attacksusing the proposed solutions will be presented in futurepapers.Future work in the area involves looking at the wirelesscommunication path between <strong>AMI</strong> of individual residences<strong>and</strong> the utility’s control center. This will involve studying adifferent class of attacks that are remote in nature <strong>and</strong> involveexploiting vulnerabilities at the network layer. Such researchwill be complementary to the work presented here, which waslocal in nature to the WHAN-SM. Additional work also needsto be done by st<strong>and</strong>ardization bodies to provide capabilities toappliances <strong>and</strong> other equipment that are expected to be part offuture WHAN-SMsVI. ACKNOWLEDGMENTThe authors gratefully acknowledge the support of thePower Systems Engineering Research Center (PSERC) <strong>and</strong>the contributions from the industrial <strong>and</strong> academic members ofPSERC Project T-39, “Communication Requirements <strong>and</strong>Integration Options <strong>for</strong> Smart Grid Deployment,” <strong>and</strong> from theUS Department of Energy Project DE-FG36-08GO88149,“Sustainable Energy Solutions.”VII. REFERENCES[1] US Department of Energy, “What the Smart Grid Means to Americans,”Tech. Rep., Available: http://www.oe.energy.gov/Documents<strong>and</strong>Media/ConsumerAdvocates.pdf.[2] F. Derbel, “Trends in Smart Metering,” in 6th International Multi-Conference on Systems, Signals <strong>and</strong> Devices (SSD), 23-26 2009.[3] W. Sweet, “The Smart Meter Avalanche”, IEEE Spectrum, October2009.[4] “Going Green with <strong>AMI</strong> <strong>and</strong> ZigBee Smart Energy,” Daintree NetworksWhite Paper, 2008. Available: http://www.daintree.net /downloads/whitepapers/ ami-smart-energy.pdf[5] C. Bennett <strong>and</strong> D. Highfill, “Networking <strong>AMI</strong> Smart Meters,” IEEEEnergy 2030 Conference 2008. Atlanta, GA 17-18 Nov 2008[6] F. Cohen, “The Smarter Grid,” IEEE <strong>Security</strong> <strong>and</strong> Privacy, vol. 8, 2010.[7] “Securing the Smart Grid,” Cisco Systems White Paper, 2009. Available:www.cisco.com/web/strategy/docs/energy/SmartGrid<strong>Security</strong>_wp.pdf[8] R. Shein, “<strong>Security</strong> Measures <strong>for</strong> Advanced Metering InfrastructureComponents,” in Asia-Pacific Power <strong>and</strong> Energy EngineeringConference (APPEEC), 28-31 2010, pp. 1–3.[9] C. Bennett <strong>and</strong> S. Wicker, “Decreased Time Delay <strong>and</strong> <strong>Security</strong>Enhancement Recommendations <strong>for</strong> <strong>AMI</strong> Smart Meter Networks,” inInnovative Smart Grid Technologies (ISGT), 19-21 2010.[10] L. AlAbdulkarim <strong>and</strong> Z. Lukszo, “Integrating In<strong>for</strong>mation <strong>Security</strong>Requirements in Critical Infrastructures: Smart Metering Case,”International Journal of Critical Infrastructures, vol. 6, no. 2, 2010.[11] F. Clevel<strong>and</strong>, “Cyber <strong>Security</strong> Issues <strong>for</strong> Advanced MeteringInfrastructure (<strong>AMI</strong>),” in Power <strong>and</strong> Energy Society General Meeting –Conversion <strong>and</strong> Delivery of Electrical Energy in the 21st Century, 2008IEEE, 20-24 2008.[12] A. Metke <strong>and</strong> R. Ekl, “<strong>Security</strong> Technology <strong>for</strong> Smart Grid Networks,”Smart Grid, IEEE Transactions on, vol. 1, no. 1, pp. 99 –107, jun. 2010.[13] C. Bennett, B. Brown, B. Singletary, D. Highfill, D. Houseman, F.Clevel<strong>and</strong>, H. Lipson, J. Ivers, J. Gooding, J. McDonald, N. Greenfield,<strong>and</strong> S. Li, <strong>AMI</strong> System <strong>Security</strong> Requirements, Utility CommunicationArchitecture International User Group (UCAIUG), December 2008.[14] Behr, “Do smart meters mean smart electricity use?” Tech. Rep.,Available: http://www.scientificamerican.com/article.cfm?id=dosmartmeters-mean-smart-electricity-use.[15] A. Synder <strong>and</strong> M. Stuber, “The ANSI C 12 Protocol Suite – Updated<strong>and</strong> Now with New Network Capabilities” Power Systems Conference:Advanced Metering, Protection, Control, Communication, <strong>and</strong>Distributed Resources, 2007.[16] H. Sui, H. Wang, M.-S. Lu, <strong>and</strong> W.-J. Lee, “An <strong>AMI</strong> System <strong>for</strong> theDeregulated Electricity Markets,” Industry <strong>Application</strong>s, IEEETransactions on, vol. 45, no. 6, pp. 2104 –2108, nov. 2009.[17] Pacific Gas <strong>and</strong> Electric News Release, “PG&E Leads the Nation inSmart Meter Deployment,” Available: http://www.pge.com/about/news/mediarelations/newsreleases/q2 2009/090414.shtml.[18] Southern Company News Release, “Southern Company ReachesMilestone in Smart Meter Program with 1 Million Installations,” Availablehttp://southerncompany.mediaroom.com/index.php?s=43&item=1870.[19] Georgia Power News Release, “Your Meter is About to Get Smarter,”Available: http://www.georgiapower.com/residential/smartmeter.asp,[20] J.-M. Bohli, C. Sorge, <strong>and</strong> O. Ugus, “A Privacy Model <strong>for</strong> SmartMetering,” IEEE 2010 International Conference on Communications,May. 2010[21] J.-S. Lee, Y.-W. Su, <strong>and</strong> C.-C. Shen, “A Comparative Study of <strong>Wireless</strong>Protocols: Bluetooth, UWB, ZigBee, <strong>and</strong> Wi-Fi,” in 33rd AnnualConference of the IEEE Industrial Electronics Society, 2007, November2007, pp. 46–51.[22] Russell Dean Vines, “<strong>Wireless</strong> <strong>Security</strong> Essentials: Defending MobileSystems from Data Piracy”, 1st Edition, John Wiley & Sons, Inc, NewYork, USA, 2002[23] IEEE802.15.4, IEEE St<strong>and</strong>ard 802, part 15.4: <strong>Wireless</strong> Medium AccessControl (MAC) <strong>and</strong> PHY) Specifications <strong>for</strong> Low Rate <strong>Wireless</strong> Personal<strong>Area</strong> Networks (WPANs), 2003.[24] T. Godfrey <strong>and</strong> C. Rodine, “Unified Metrics <strong>for</strong> Management of SmartGrid <strong>Home</strong> <strong>Area</strong> Networks,” IEEE 2010 International Conference onCommunications, May. 2010[25] V. Navda, A. Bohra, <strong>and</strong> S. Ganguly, “Using Channel Hopping toIncrease 802.11 Resilience to Jamming Attacks,” in In Proc. IEEEInfocom Minisymposium, 2007.[26] “The Network Simulator NS-2,” User In<strong>for</strong>mation, Available:http://www.isi.edu/nsnam/ns/.[27] A. Shamir, “On the Generation of Cryptographically StrongPseudor<strong>and</strong>om Sequences,” ACM Trans. Comput. Syst., vol. 1, 1983.[28] National Institute of St<strong>and</strong>ards <strong>and</strong> Technology (NIST), “CryptographicToolkit,” Available: http://csrc.nist.gov/groups/ST/toolkit/index.html.[29] P. Yi, A. Iwayemi, <strong>and</strong> C. Zhou, “Frequency Agility in a ZigBeeNetwork <strong>for</strong> Smart Grid <strong>Application</strong>,” Innovative Smart GridTechnologies 2010, Gaithesburg, MD Jan. 2010.VIII. BIOGRAPHIESVisvakumar Aravinthan (S’04, M’10) received his BS degree in ElectricalEngineering from University of Moratuwa, Sri Lanka in 2002 <strong>and</strong> received hisMS <strong>and</strong> Ph.D. in electrical engineering from Wichita State University in 2006<strong>and</strong> 2010 respectively. Currently, he is a visiting lecturer at ClemsonUniversity teaching power system courses. His research interests includedistribution automation, smart grid applications, electric vehicles <strong>and</strong> controls.Vinod Namboodiri teaches communications <strong>and</strong> networking courses as anAssistant Professor of Electrical Engineering <strong>and</strong> Computer Science atWichita State University. He per<strong>for</strong>ms research in energy related aspects ofwireless networking that includes optimizing energy consumption of portablewireless networking devices <strong>and</strong> the application of wireless technologies <strong>for</strong>the Smart Grid.Samshodh Sunku received his BE degree in Electronics <strong>and</strong> CommunicationEngineering from Visvesvaraya Technological University in 2007 <strong>and</strong>presently pursuing MS in Electrical Engineering at Wichita State Universityper<strong>for</strong>ming duties as a Graduate Research Assistant. His research interests arein <strong>Wireless</strong> networking technologies <strong>and</strong> Smart Grid.Ward Jewell teaches electric power systems <strong>and</strong> electric machinery as aProfessor of Electrical Engineering at Wichita State University. Dr. Jewell isSite Director <strong>for</strong> the Power Systems Engineering Research Center (PSerc). Heis a Fellow of the IEEE. He per<strong>for</strong>ms research in electric power systems <strong>and</strong>advanced energy technologies. He has been with Wichita State since 1987.