Inspecting DNS Flow Traffic for Purposes of Botnet Detection
Inspecting DNS Flow Traffic for Purposes of Botnet Detection
Inspecting DNS Flow Traffic for Purposes of Botnet Detection
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
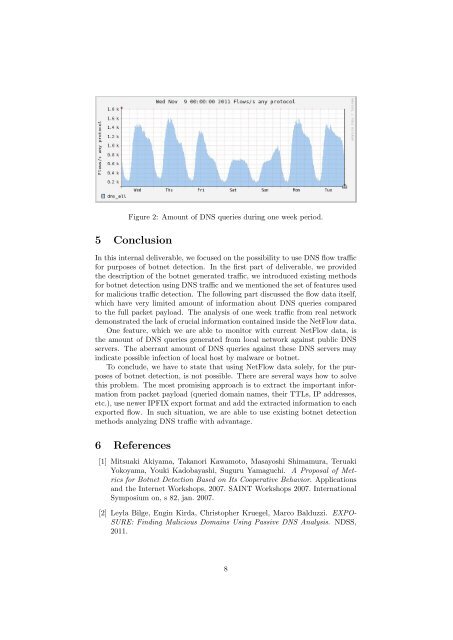
Figure 2: Amount <strong>of</strong> <strong>DNS</strong> queries during one week period.5 ConclusionIn this internal deliverable, we focused on the possibility to use <strong>DNS</strong> flow traffic<strong>for</strong> purposes <strong>of</strong> botnet detection. In the first part <strong>of</strong> deliverable, we providedthe description <strong>of</strong> the botnet generated traffic, we introduced existing methods<strong>for</strong> botnet detection using <strong>DNS</strong> traffic and we mentioned the set <strong>of</strong> features used<strong>for</strong> malicious traffic detection. The following part discussed the flow data itself,which have very limited amount <strong>of</strong> in<strong>for</strong>mation about <strong>DNS</strong> queries comparedto the full packet payload. The analysis <strong>of</strong> one week traffic from real networkdemonstrated the lack <strong>of</strong> crucial in<strong>for</strong>mation contained inside the Net<strong>Flow</strong> data.One feature, which we are able to monitor with current Net<strong>Flow</strong> data, isthe amount <strong>of</strong> <strong>DNS</strong> queries generated from local network against public <strong>DNS</strong>servers. The aberrant amount <strong>of</strong> <strong>DNS</strong> queries against these <strong>DNS</strong> servers mayindicate possible infection <strong>of</strong> local host by malware or botnet.To conclude, we have to state that using Net<strong>Flow</strong> data solely, <strong>for</strong> the purposes<strong>of</strong> botnet detection, is not possible. There are several ways how to solvethis problem. The most promising approach is to extract the important in<strong>for</strong>mationfrom packet payload (queried domain names, their TTLs, IP addresses,etc.), use newer IPFIX export <strong>for</strong>mat and add the extracted in<strong>for</strong>mation to eachexported flow. In such situation, we are able to use existing botnet detectionmethods analyzing <strong>DNS</strong> traffic with advantage.6 References[1] Mitsuaki Akiyama, Takanori Kawamoto, Masayoshi Shimamura, TeruakiYokoyama, Youki Kadobayashi, Suguru Yamaguchi. A Proposal <strong>of</strong> Metrics<strong>for</strong> <strong>Botnet</strong> <strong>Detection</strong> Based on Its Cooperative Behavior. Applicationsand the Internet Workshops, 2007. SAINT Workshops 2007. InternationalSymposium on, s 82, jan. 2007.[2] Leyla Bilge, Engin Kirda, Christopher Kruegel, Marco Balduzzi. EXPO-SURE: Finding Malicious Domains Using Passive <strong>DNS</strong> Analysis. NDSS,2011.8