and s (i+k) differ <strong>in</strong> the ith bit position <strong>in</strong> the field M[c]. Lets (i, j) = (s (i) ) ( j) for 0 ≤ i, j ≤ m + k − 1. We use (u → v) todenote a path from node u to node v. If the length of a path(u → v) is 1 (through a s<strong>in</strong>gle edge), the path is denoted as(u : v), and the edge is denoted as (u,v).In a graph G = (V,E) where V is the set of all vertices(nodes) and E is the set of all edges <strong>in</strong> G, let P ′ = (v 0 →v h−1 ) = (v 0 : v 1 : ... : v h−1 ) be a path from node v 0 to nodev h−1 , where v i ∈ V for 0 ≤ i ≤ h−1 and edge (v j−1 ,v j ) ∈ Efor 1 ≤ j ≤ h − 1. We say P ′ is a hamiltonian path if (1) P ′conta<strong>in</strong>s every node <strong>in</strong> V and (2) nodes v i (0 ≤ i ≤ h−1) areall dist<strong>in</strong>ct. Let P = (v 0 → v h ) = (P ′ : v h ), where v h = v i , fori = 0,1,..., or h − 2. If v h = v 0 , then P becomes a hamiltoniancycle 1 ; otherwise, we call P an extended-hamiltonianpath. The length of a hamiltonian path <strong>in</strong> a k-cube is2 k − 1; the length of a hamiltonian cycle or an extendedhamiltonianpath is 2 k . Let a weak-hamiltonian path bea hamiltonian path, a hamiltonian cycle, or an extendedhamiltonianpath. It was shown <strong>in</strong> [8] that given any twonodes s and t <strong>in</strong> an n-cube, there exists a weak-hamiltonianpath from s to t.For each node u <strong>in</strong> the k-cube, let next(u) be the nodenext to u <strong>in</strong> the weak-hamiltonian path from c s to c t . Let thenode addresses of s and t be (c s ,M s [h−1],...,M s [1],M s [0])and (c t ,M t [h − 1],...,M t [1],M t [0]), respectively. For therout<strong>in</strong>g with<strong>in</strong> an m-cube of class c, we can follow the ascend<strong>in</strong>grout<strong>in</strong>g strategy, by which the least significant nonzerobit of (M s [c] ⊕ M t [c]) is chosen as the first dimensionfor rout<strong>in</strong>g, and so on. The rout<strong>in</strong>g algorithm <strong>in</strong> an MC(k,m)is given below. The Loop will term<strong>in</strong>ate when the breakis executed. Notice that the details of rout<strong>in</strong>g <strong>in</strong> the m-cubeis omitted <strong>in</strong> the algorithm.Algorithm 1 (One_To_One_<strong>Rout<strong>in</strong>g</strong>(m,k,s,t))beg<strong>in</strong> /* build a P = (s → t) <strong>in</strong> MC(k,m) */u = c s ; v = s; P = v;loop alwaysw = (u,M v [h − 1],...,M v [u + 1],M t [u],M v [u − 1],...,M v [0]);if (w ≠ v) P = (P → w);if (w == t) break;v = w;w = (next(u),M v [h − 1],...,M v [u + 1],M v [u],M v [u − 1],...,M v [0]);P = (P : w);u = next(u);endloopend.In the fault-<strong>tolerant</strong> rout<strong>in</strong>g we discuss late, we need directedhamiltonian cycles. Therefore, we <strong>in</strong>troduce a pa-1 A hamiltonian cycle is def<strong>in</strong>ed as a path through a graph which startsand ends at the same vertex and <strong>in</strong>cludes every other vertex exactly once.rameter, next(s), to assign the direction of a hamiltoniancycle. For example, <strong>in</strong> Example 1, if we let next(s) = 10,then the hamiltonian cycle for (C s → C t ) <strong>in</strong> the high-level2-cube will be (00 : 10 : 11 : 01 : 00).Let H i (s,t), 0 ≤ i ≤ h − 1, be the Hamm<strong>in</strong>g distancebetween s and t <strong>in</strong> M[i], i.e. the number of bits with dist<strong>in</strong>ctvalues <strong>in</strong> M s [i] and M t [i]. From the algorithm, thelongest length of the rout<strong>in</strong>g path is 2 k + H h (s,t), whereH h (s,t) = ∑ h−1i=0 H i(s,t). This formula gives an upper boundto d(s,t), the distance between s and t <strong>in</strong> an MC(k,m). LetH(s,t) be the Hamm<strong>in</strong>g distance between s and t. Clearly,we have H(s,t) ≤ d(s,t) ≤ H h (s,t) + 2 k . Because H(s,t) =H h (s,t) + H k (s,t), where H k (s,t) is the Hamm<strong>in</strong>g distancebetween s and t <strong>in</strong> c field, we have H(s,t) ≤ d(s,t) ≤H(s,t) − H k (s,t) + 2 k . The longest path <strong>in</strong> an MC(k,m) isfrom s = 0···0 to t, where c t = 0···0 and M t [i] = 1···1 forall i, 0 ≤ i ≤ h − 1. The length of this path is 2 k (m + 1). Itis easy to see that this path is the shortest path for connect<strong>in</strong>gs and t. Therefore, it is the diameter of an MC(k,m).S<strong>in</strong>ce the average distance <strong>in</strong> each cluster is m/2, the averagedistance between any two nodes <strong>in</strong> an MC(k,m) isat most (m/2)2 k + 2 k = (n − k)/2 + 2 k , where n = m2 k + k(<strong>in</strong> the case of hamiltonian path, it is (n − k)/2 + 2 k − 1).Notice that it is possible to have a rout<strong>in</strong>g algorithm <strong>in</strong> anMC(k,m) which bypasses the class c if M s [c] = M t [c]. Insuch a case, the length of the rout<strong>in</strong>g path for some s and tmight be shorter than that produced by the algorithm above.4. Multi-channel cubeIn this section, we will describe a structure <strong>in</strong> themetacube, called multi-channel cube. This structure is usefulfor design<strong>in</strong>g algorithms <strong>in</strong> MC(k,m) based on hypercubealgorithms. We will use this structure for solv<strong>in</strong>g fault<strong>tolerant</strong>rout<strong>in</strong>g problem <strong>in</strong> the metacube.Let C u and C v be two dist<strong>in</strong>ct clusters <strong>in</strong> an MC(k,m),h = 2 k . A multi-channel cube is def<strong>in</strong>ed as C u ∪ C v ∪ E,where E is a set of k2 m disjo<strong>in</strong>t paths connect<strong>in</strong>g C u andC v , k paths for each node pair (u i ,v i ), u i ∈ C u , v i ∈ C v , fori = 0,1,...,2 m − 1. In the other word, E = ∪i, j(u i → v i ) j ,0 ≤ i ≤ 2 m −1 and 0 ≤ j ≤ k −1, and (u i1 → v i1 ) j1 ∩(u i2 →v i2 ) j2 = /0 if i 1 ≠ i 2 or j 1 ≠ j 2 .Figure 3 shows an example of a multi-channel cube. Thedotted l<strong>in</strong>e denotes a path, not an edge. In the case of atraditional n-cube, there is an edge (u,v) connect<strong>in</strong>g twonodes u and v for u ∈ 0-subcube and v ∈ 1-subcube. Insteadof an edge, the two nodes of a node pair <strong>in</strong> a multi-channelcube are connected by k disjo<strong>in</strong>t paths.The major problem <strong>in</strong> construct<strong>in</strong>g the k disjo<strong>in</strong>t paths isthat the path (u i → v i ) j , 0 ≤ i ≤ 2 m − 1 and 0 ≤ j ≤ k − 1,will just advance through cross-edges when M ui [l] = M vi [l]for some l, 0 ≤ l ≤ 2 k − 1. This will cause two paths346
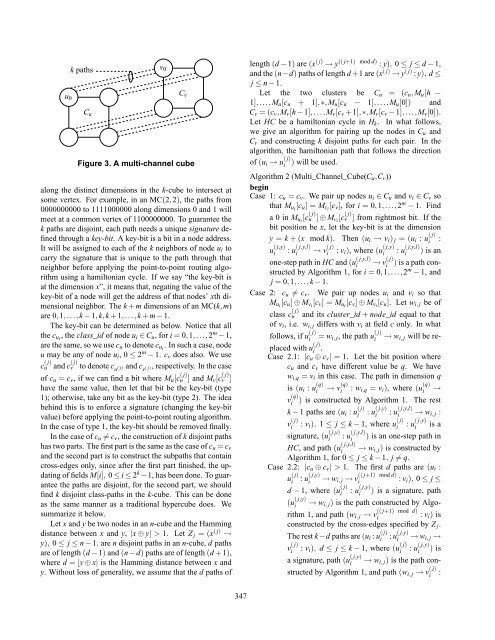
k pathsu0v 0C uC vFigure 3. A multi-channel cubealong the dist<strong>in</strong>ct dimensions <strong>in</strong> the k-cube to <strong>in</strong>tersect atsome vertex. For example, <strong>in</strong> an MC(2,2), the paths from0000000000 to 1111000000 along dimensions 0 and 1 willmeet at a common vertex of 1100000000. To guarantee thek paths are disjo<strong>in</strong>t, each path needs a unique signature def<strong>in</strong>edthrough a key-bit. A key-bit is a bit <strong>in</strong> a node address.It will be assigned to each of the k neighbors of node u i tocarry the signature that is unique to the path through thatneighbor before apply<strong>in</strong>g the po<strong>in</strong>t-to-po<strong>in</strong>t rout<strong>in</strong>g algorithmus<strong>in</strong>g a hamiltonian cycle. If we say “the key-bit isat the dimension x”, it means that, negat<strong>in</strong>g the value of thekey-bit of a node will get the address of that nodes’ xth dimensionalneighbor. The k + m dimensions of an MC(k,m)are 0,1,...,k − 1,k,k + 1,...,k + m − 1.The key-bit can be determ<strong>in</strong>ed as below. Notice that allthe c ui , the class_id of node u i ∈ C u , for i = 0,1,...,2 m −1,are the same, so we use c u to denote c ui . In such a case, nodeu may be any of node u i , 0 ≤ 2 m − 1. c v does also. We usec ( u j) and c ( vj) to denote c u ( j) and c v ( j), respectively. In the caseof c u = c v , if we can f<strong>in</strong>d a bit where M u [c ( u j) ] and M v [c ( v j) ]have the same value, then let that bit be the key-bit (type1); otherwise, take any bit as the key-bit (type 2). The ideabeh<strong>in</strong>d this is to enforce a signature (chang<strong>in</strong>g the key-bitvalue) before apply<strong>in</strong>g the po<strong>in</strong>t-to-po<strong>in</strong>t rout<strong>in</strong>g algorithm.In the case of type 1, the key-bit should be removed f<strong>in</strong>ally.In the case of c u ≠ c v , the construction of k disjo<strong>in</strong>t pathshas two parts. The first part is the same as the case of c u = c vand the second part is to construct the subpaths that conta<strong>in</strong>cross-edges only, s<strong>in</strong>ce after the first part f<strong>in</strong>ished, the updat<strong>in</strong>gof fields M[i], 0 ≤ i ≤ 2 k −1, has been done. To guaranteethe paths are disjo<strong>in</strong>t, for the second part, we shouldf<strong>in</strong>d k disjo<strong>in</strong>t class-paths <strong>in</strong> the k-cube. This can be doneas the same manner as a traditional hypercube does. Wesummarize it below.Let x and y be two nodes <strong>in</strong> an n-cube and the Hamm<strong>in</strong>gdistance between x and y, |x ⊕ y| > 1. Let Z j = (x ( j) →y), 0 ≤ j ≤ n − 1, are n disjo<strong>in</strong>t paths <strong>in</strong> an n-cube, d pathsare of length (d −1) and (n−d) paths are of length (d +1),where d = |y ⊕ x| is the Hamm<strong>in</strong>g distance between x andy. Without loss of generality, we assume that the d paths oflength (d − 1) are (x ( j) → y (( j+1) mod d) : y), 0 ≤ j ≤ d − 1,and the (n−d) paths of length d +1 are (x ( j) → y ( j) : y), d ≤j ≤ n − 1.Let the two clusters be C u = (c u ,M u [h −1],...,M u [c u + 1],∗,M u [c u − 1],...,M u [0]) andC v = (c v ,M v [h−1],...,M v [c v +1],∗,M v [c v −1],...,M v [0]).Let HC be a hamiltonian cycle <strong>in</strong> H k . In what follows,we give an algorithm for pair<strong>in</strong>g up the nodes <strong>in</strong> C u andC v and construct<strong>in</strong>g k disjo<strong>in</strong>t paths for each pair. In thealgorithm, the hamiltonian path that follows the directionof (u i → u ( j)i) will be used.Algorithm 2 (Multi_Channel_Cube(C u ,C v ))beg<strong>in</strong>Case 1: c u = c v . We pair up nodes u i ∈ C u and v i ∈ C v sothat M ui [c u ] = M vi [c v ], for i = 0,1,...,2 m − 1. F<strong>in</strong>da 0 <strong>in</strong> M ui [c ( u j) ] ⊕ M vi [c ( vj) ] from rightmost bit. If thebit position be x, let the key-bit is at the dimensiony = k + (x mod k). Then (u i → v i ) j = (u i : u ( j)u ( j,y)i: u ( j,y,l)i→ v ( j)i: v i ), where (u ( j,y)ione-step path <strong>in</strong> HC and (u ( j,y,l)i→ v ( j)ii:: u ( j,y,l)i) is an) is a path constructedby Algorithm 1, for i = 0,1,...,2 m − 1, andj = 0,1,...,k − 1.Case 2: c u ≠ c v . We pair up nodes u i and v i so thatM ui [c u ] ⊕ M vi [c v ] = M ui [c v ] ⊕ M vi [c u ]. Let w i, j be ofclass c ( uj) and its cluster_id + node_id equal to thatof v i , i.e. w i, j differs with v i at field c only. In whatfollows, if u ( j)i= w i, j , the path u ( j)i→ w i, j will be replacedwith u ( j)i.Case 2.1: |c u ⊕ c v | = 1. Let the bit position wherec u and c v have different value be q. We havew i,q = v i <strong>in</strong> this case. The path <strong>in</strong> dimension qis (u i : u (q)iv (q)i→ v (q)i: w i,q = v i ), where (u (q)i→) is constructed by Algorithm 1. The restk − 1 paths are (u i : u ( j)i: u ( j,y)i: u ( j,y,l)i→ w i, j :: u ( j,y)iis a) is an one-step path <strong>in</strong>v ( j)i: v i ), 1 ≤ j ≤ k − 1, where u ( j)i: u ( j,y,l)isignature, (u ( j,y)iHC, and path (u ( j,y,l)(u ( j,y)i(( j+1) mod d)i→ w i, j ) is constructed byAlgorithm 1, for 0 ≤ j ≤ k − 1, j ≠ q.Case 2.2: |c u ⊕ c v | > 1. The first d paths are (u i :u ( j)i: u ( j,y)(( j+1) mod d)i→ w i, j → vi: v i ), 0 ≤ j ≤d − 1, where (u ( j)i: u ( j,y)i) is a signature, path→ w i, j ) is the path constructed by Algorithm1, and path (w i, j → vi: v i ) isconstructed by the cross-edges specified by Z j .The rest k−d paths are (u i : u ( j)i: u ( j,y)i→ w i, j →v ( j)i: v i ), d ≤ j ≤ k − 1, where (u ( j)ia signature, path (u ( j,y)i: u ( j,y)i) is→ w i, j ) is the path constructedby Algorithm 1, and path (w i, j → v ( j)i:347