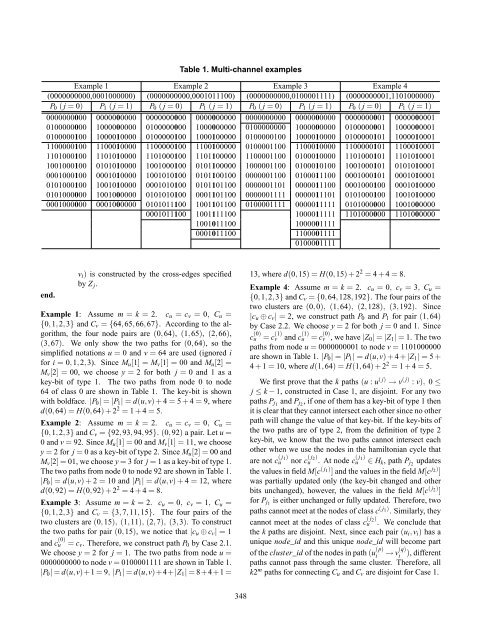
Table 1. Multi-channel examplesExample 1 Example 2 Example 3 Example 4(0000000000,0001000000) (0000000000,0001011100) (0000000000,0100001111) (0000000001,1101000000)P 0 ( j = 0) P 1 ( j = 1) P 0 ( j = 0) P 1 ( j = 1) P 0 ( j = 0) P 1 ( j = 1) P 0 ( j = 0) P 1 ( j = 1)0000000000 0000000000 0000000000 0000000000 0000000000 0000000000 0000000001 00000000010100000000 1000000000 0100000000 1000000000 0100000000 1000000000 0100000001 10000000010100000100 1000010000 0100000100 1000100000 0100000100 1000010000 0100000101 10000100011100000100 1100010000 1100000100 1100100000 0100001100 1100010000 1100000101 11000100011101000100 1101010000 1101000100 1101100000 1100001100 0100010000 1101000101 11010100011001000100 0101010000 1001000100 0101100000 1000001100 0100010100 1001000101 01010100010001000100 0001010000 1001010100 0101100100 0000001100 0100011100 0001000101 00010100010101000100 1001010000 0001010100 0101101100 0000001101 0000011100 0001000100 00010100000101000000 1001000000 0101010100 0001101100 0000001111 0000011101 0101000100 10010100000001000000 0001000000 0101011100 1001101100 0100001111 0000011111 0101000000 10010000000001011100 1001111100 1000011111 1101000000 11010000001001011100 10000011110001011100 11000011110100001111end.v i ) is constructed by the cross-edges specifiedby Z j .Example 1: Assume m = k = 2. c u = c v = 0, C u ={0,1,2,3} and C v = {64,65,66,67}. Accord<strong>in</strong>g to the algorithm,the four node pairs are (0,64), (1,65), (2,66),(3,67). We only show the two paths for (0,64), so thesimplified notations u = 0 and v = 64 are used (ignored ifor i = 0,1,2,3). S<strong>in</strong>ce M u [1] = M v [1] = 00 and M u [2] =M v [2] = 00, we choose y = 2 for both j = 0 and 1 as akey-bit of type 1. The two paths from node 0 to node64 of class 0 are shown <strong>in</strong> Table 1. The key-bit is shownwith boldface. |P 0 | = |P 1 | = d(u,v) + 4 = 5 + 4 = 9, whered(0,64) = H(0,64) + 2 2 = 1 + 4 = 5.Example 2: Assume m = k = 2. c u = c v = 0, C u ={0,1,2,3} and C v = {92,93,94,95}. (0,92) a pair. Let u =0 and v = 92. S<strong>in</strong>ce M u [1] = 00 and M v [1] = 11, we choosey = 2 for j = 0 as a key-bit of type 2. S<strong>in</strong>ce M u [2] = 00 andM v [2] = 01, we choose y = 3 for j = 1 as a key-bit of type 1.The two paths from node 0 to node 92 are shown <strong>in</strong> Table 1.|P 0 | = d(u,v) + 2 = 10 and |P 1 | = d(u,v) + 4 = 12, whered(0,92) = H(0,92) + 2 2 = 4 + 4 = 8.Example 3: Assume m = k = 2. c u = 0, c v = 1, C u ={0,1,2,3} and C v = {3,7,11,15}. The four pairs of thetwo clusters are (0,15), (1,11), (2,7), (3,3). To constructthe two paths for pair (0,15), we notice that |c u ⊕ c v | = 1and c (0)u = c v . Therefore, we construct path P 0 by Case 2.1.We choose y = 2 for j = 1. The two paths from node u =0000000000 to node v = 0100001111 are shown <strong>in</strong> Table 1.|P 0 | = d(u,v)+1 = 9, |P 1 | = d(u,v)+4+|Z 1 | = 8+4+1 =13, where d(0,15) = H(0,15) + 2 2 = 4 + 4 = 8.Example 4: Assume m = k = 2. c u = 0, c v = 3, C u ={0,1,2,3} and C v = {0,64,128,192}. The four pairs of thetwo clusters are (0,0), (1,64), (2,128), (3,192). S<strong>in</strong>ce|c u ⊕ c v | = 2, we construct path P 0 and P 1 for pair (1,64)by Case 2.2. We choose y = 2 for both j = 0 and 1. S<strong>in</strong>cec (0)u = c (1)v and c (1)u = c (0)v , we have |Z 0 | = |Z 1 | = 1. The twopaths from node u = 0000000001 to node v = 1101000000are shown <strong>in</strong> Table 1. |P 0 | = |P 1 | = d(u,v) + 4 + |Z 1 | = 5 +4 + 1 = 10, where d(1,64) = H(1,64) + 2 2 = 1 + 4 = 5.We first prove that the k paths (u : u ( j) → v ( j) : v), 0 ≤j ≤ k − 1, constructed <strong>in</strong> Case 1, are disjo<strong>in</strong>t. For any twopaths P j1 and P j2 , if one of them has a key-bit of type 1 thenit is clear that they cannot <strong>in</strong>tersect each other s<strong>in</strong>ce no otherpath will change the value of that key-bit. If the key-bits ofthe two paths are of type 2, from the def<strong>in</strong>ition of type 2key-bit, we know that the two paths cannot <strong>in</strong>tersect eachother when we use the nodes <strong>in</strong> the hamiltonian cycle that∈ H k , path P j2 updatesthe values <strong>in</strong> field M[c ( j1) ] and the values <strong>in</strong> the field M[c j2) ]was partially updated only (the key-bit changed and otherbits unchanged), however, the values <strong>in</strong> the field M[c ( j2) ]for P j1 is either unchanged or fully updated. Therefore, twopaths cannot meet at the nodes of class c ( j1) . Similarly, theyare not c ( j 1)u nor c ( j 2)u . At node c ( j 1)ucannot meet at the nodes of class c ( j 2)u . We conclude thatthe k paths are disjo<strong>in</strong>t. Next, s<strong>in</strong>ce each pair (u i ,v i ) has aunique node_id and this unique node_id will become partof the cluster_id of the nodes <strong>in</strong> path (u (p) → v (q) ), differentpaths cannot pass through the same cluster. Therefore, allk2 m paths for connect<strong>in</strong>g C u and C v are disjo<strong>in</strong>t for Case 1.ii348
To show the k paths for each node pair constructed<strong>in</strong> Case 2 are disjo<strong>in</strong>t, we divide each path <strong>in</strong>to to parts,→ w i, j ) and (w i, j → v i ). S<strong>in</strong>ce the first part of the path<strong>in</strong>cludes a signature (except P q <strong>in</strong> Case 2.1), they shouldbe disjo<strong>in</strong>t follow<strong>in</strong>g the same argument as <strong>in</strong> Case 1 (theargument is true even one of the paths does not carry signature).Moreover, it is also disjo<strong>in</strong>t with the second part(u ( j)iof other paths because of its unique signature. The secondparts of the paths P j , 0 ≤ j ≤ k − 1, conta<strong>in</strong> onlythe cross-edges that are identical to the disjo<strong>in</strong>t class pathsZ j , they are also disjo<strong>in</strong>t. Therefore, the k paths constructedby the algorithm are disjo<strong>in</strong>t. To prove that the hsets of paths (u i → v i ), 0 ≤ i ≤ 2 m − 1 are disjo<strong>in</strong>t also,we argue as follows: First for each u i , consider the paths(u i → u ( j)i→ w i → w ′ i ), where c w ≠ c v and c next(wi ) = c v ,c w ′i≠ c v and c prev(w ′i ) = c v . From the algorithm, we knowthat the h sets of paths (u i → w i ) are disjo<strong>in</strong>t s<strong>in</strong>ce the valueM ui [c u ] is different for every u i ∈ C u and M ui [c u ] is part ofthe cluster_id of every node <strong>in</strong> path (u ( j)i→ w ′ i ). In path(w i → w ′ i ), the value M u i[c v ] is changed to M vi [c v ]. S<strong>in</strong>ceM ui [c u ]⊕M vi [c v ] = M ui [c v ]⊕M vi [c u ], M vi [c v ] takes differentvalues for every u i . That is, node w ′ i is <strong>in</strong> dist<strong>in</strong>ct clustersfor every u i . S<strong>in</strong>ce M vi [c v ] is part of the cluster_id of everynode <strong>in</strong> path (w ′ i → v i), the h sets of paths (w ′ i → v i)are also disjo<strong>in</strong>t. Therefore, we conclude that all paths forconnect<strong>in</strong>g the clusters C u and C v are disjo<strong>in</strong>t for Case 2.From the path construction <strong>in</strong> Case 1, the length of thelongest path (u i → v i ) is |(u i → v i )| = d(u i ,v i ) + 4, whered(u i ,v i ) = H(u i ,v i )+2 k , H(u i ,v i ) is Hamm<strong>in</strong>g distance betweenu i and v i . From the path construction <strong>in</strong> Case 2,the longest length of the paths (u i → v i ) is |(u i → v i )| =d(u i ,v i ) + 4 + max 0≤ j≤k−1 {|Z j |} ≤ d(u i ,v i ) + m + 5. Wesummarize the results <strong>in</strong> the follow<strong>in</strong>g theorem.Theorem 1. Given any two clusters C u and C v <strong>in</strong> MC(k,m),we can f<strong>in</strong>d a multi-channel cube C u ∪C v ∪ E, where E isa set of k2 m disjo<strong>in</strong>t paths connect<strong>in</strong>g C u and C v , k pathsfor each node pair (u i ,v i ), u i ∈ C u , v i ∈ C v , and the lengthof the paths <strong>in</strong> E is at most max(d(u i ,v i )) + m + 5, for i =0,1,...,2 m − 1.5. <strong>Fault</strong>-<strong>tolerant</strong> rout<strong>in</strong>gWith the multi-channel cube structure, the fault-<strong>tolerant</strong>rout<strong>in</strong>g problem can be solved efficiently <strong>in</strong> an MC(k,m) assum<strong>in</strong>gthat there are up to k+m−1 faulty nodes. The fault<strong>tolerant</strong>rout<strong>in</strong>g from source s to dest<strong>in</strong>ation t <strong>in</strong> hypercubehas been solved <strong>in</strong> [4]. The hypercube algorithm is summarizedbelow. First, we partition the n-cube <strong>in</strong>to two (n − 1)-dimensional subcubes along a dimension k such that s andt are <strong>in</strong> the dist<strong>in</strong>ct subcubes. If the subcube conta<strong>in</strong><strong>in</strong>g thas less faulty nodes then we route s to the subcube conta<strong>in</strong><strong>in</strong>gt by a fault-free path of length at most 2: (s → s (k) )or (s → s ( j,k) ) for some j, 0 ≤ j ≤ n − 1, j ≠ k. Then theproblem is reduced to the sub-problem <strong>in</strong> the subcube conta<strong>in</strong><strong>in</strong>gt. Repeat this process at most logn times until thesubcube conta<strong>in</strong>s no faulty node. The path (s → s ( j,k) ) is abad candidate if the jth bit of s is the same as that of t (abad candidate will <strong>in</strong>crease the length of the rout<strong>in</strong>g path).The algorithm guarantees that the bad candidate is used byat most one partition. It was shown <strong>in</strong> [4] that given twononfaulty nodes s and t, and up to n − 1 faulty nodes <strong>in</strong>an n-cube, we can f<strong>in</strong>d a fault-free path of length at mostd(s,t) + 2 <strong>in</strong> O(n) time.Under the conditions k ≤ m and the number of faultynodes <strong>in</strong> C s ∪C t is at most m, we show that an efficient algorithmfor fault-<strong>tolerant</strong> rout<strong>in</strong>g from s to t <strong>in</strong> MC(k,m)can be found. For most of the <strong>in</strong>terest<strong>in</strong>g MC(k,m), we havek ≤ m as <strong>in</strong>dicated <strong>in</strong> the previous sections. Statistically, thecondition that there are at most m faculty nodes <strong>in</strong> the twoclusters is held with very high probability. Assum<strong>in</strong>g uniformdistribution, the probability of at most m fault nodes <strong>in</strong>) (/2 m2 k +kC s ∪C t is m ∑( m+k−1ii=0)( 2 m2 k +k −(m+k−1)2 m+1 −i2 m+1 )≈ 1. For example,the probability is 3186303/3186304 = 0.99999969<strong>in</strong> the case of k = m = 2. An algorithm for fault-<strong>tolerant</strong>rout<strong>in</strong>g under the conditions above <strong>in</strong> an MC(k,m) is givenbelow.Algorithm 3 (<strong>Fault</strong>_Tolerant_<strong>Rout<strong>in</strong>g</strong>(k,m,s,t))beg<strong>in</strong>Case 1: C s = C t . If C s conta<strong>in</strong>s at most m − 1 faulty nodesthen we apply the hypercube algorithm. Otherwise,at least m faulty nodes are <strong>in</strong> C s . We f<strong>in</strong>d k disjo<strong>in</strong>tpaths (s → t) outside the cluster C s as follows: P j =(s : s ( j) : s ( j,k) : s ( j,k, j) → t ( j,k, j) : t ( j,k) : t ( j) : t), 0 ≤j ≤ k − 1, where s ( j,k, j) and t ( j,k, j) are <strong>in</strong> the samecluster ≠ C s . S<strong>in</strong>ce there at most k − 1 faulty nodesoutside the cluster C s , there exists a fault-free path P j .Case 2: C s ≠ C t . We create a multi-channel cube with C sand C t as described <strong>in</strong> the previous subsection. S<strong>in</strong>cethere are at most m fault nodes <strong>in</strong> C s ∪C t , we can f<strong>in</strong>da fault-free path of length at most d(s,t) + 2 <strong>in</strong> O(m)time <strong>in</strong> the (m + 1)-cube formed by C s ∪C t . If the kpaths (u → v) of the multi-channel cube, which correspondto a s<strong>in</strong>gle (m + 1)th dimensional cube-edge,are all faulty, then we mark v as a faulty node. Ifthe number of faulty nodes <strong>in</strong> C s ∪ C t is m, then nomarked faulty node will be created. Otherwise, s<strong>in</strong>cea marked faulty node consumes k faulty nodes outsideclusters C s and C t , the total number of faulty andmarked faulty nodes will be at most m + 1 − 1 = m.Therefore, we can apply the hypercube algorithm,and f<strong>in</strong>d a fault-free path <strong>in</strong> the (m + 1)-cube formedby C s ∪C t . Replac<strong>in</strong>g the (m+1)th dimensional cubeedge(u,v) <strong>in</strong> the fault-free path (s → t) by a fault-free349