Download - Cloud Security Alliance
Download - Cloud Security Alliance
Download - Cloud Security Alliance
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
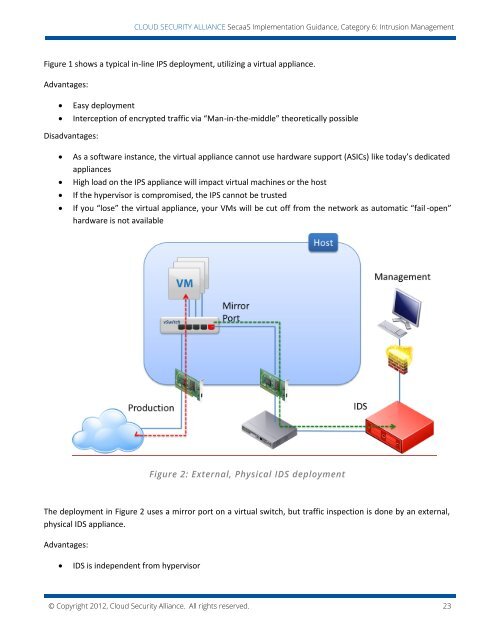
CLOUD SECURITY ALLIANCE SecaaS Implementation Guidance, Category 6: Intrusion ManagementFigure 1 shows a typical in-line IPS deployment, utilizing a virtual appliance.Advantages:Easy deploymentInterception of encrypted traffic via “Man-in-the-middle” theoretically possibleDisadvantages:As a software instance, the virtual appliance cannot use hardware support (ASICs) like today’s dedicatedappliancesHigh load on the IPS appliance will impact virtual machines or the hostIf the hypervisor is compromised, the IPS cannot be trustedIf you “lose” the virtual appliance, your VMs will be cut off from the network as automatic “fail -open”hardware is not availableFigure 2: External, Physical IDS deploymentThe deployment in Figure 2 uses a mirror port on a virtual switch, but traffic inspection is done by an external,physical IDS appliance.Advantages:IDS is independent from hypervisor© Copyright 2012, <strong>Cloud</strong> <strong>Security</strong> <strong>Alliance</strong>. All rights reserved. 23