Download - Cloud Security Alliance
Download - Cloud Security Alliance
Download - Cloud Security Alliance
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
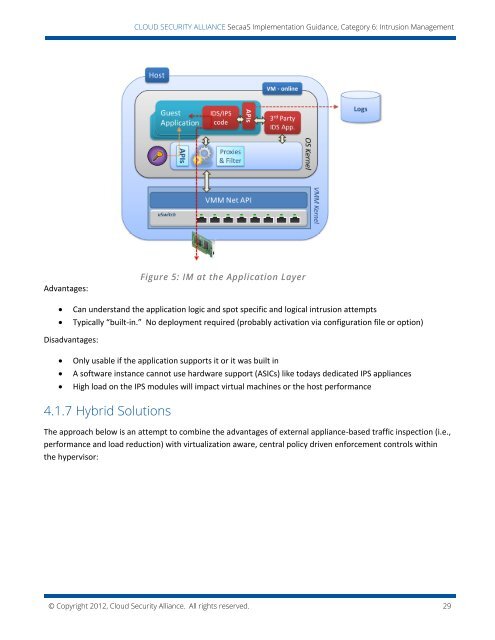
CLOUD SECURITY ALLIANCE SecaaS Implementation Guidance, Category 6: Intrusion ManagementAdvantages:Figure 5: IM at the Application LayerCan understand the application logic and spot specific and logical intrusion attemptsTypically “built-in.” No deployment required (probably activation via configuration file or option)Disadvantages:Only usable if the application supports it or it was built inA software instance cannot use hardware support (ASICs) like todays dedicated IPS appliancesHigh load on the IPS modules will impact virtual machines or the host performance4.1.7 Hybrid SolutionsThe approach below is an attempt to combine the advantages of external appliance-based traffic inspection (i.e.,performance and load reduction) with virtualization aware, central policy driven enforcement controls withinthe hypervisor:© Copyright 2012, <strong>Cloud</strong> <strong>Security</strong> <strong>Alliance</strong>. All rights reserved. 29