white paper on industrial automation security in fieldbus and
white paper on industrial automation security in fieldbus and
white paper on industrial automation security in fieldbus and
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
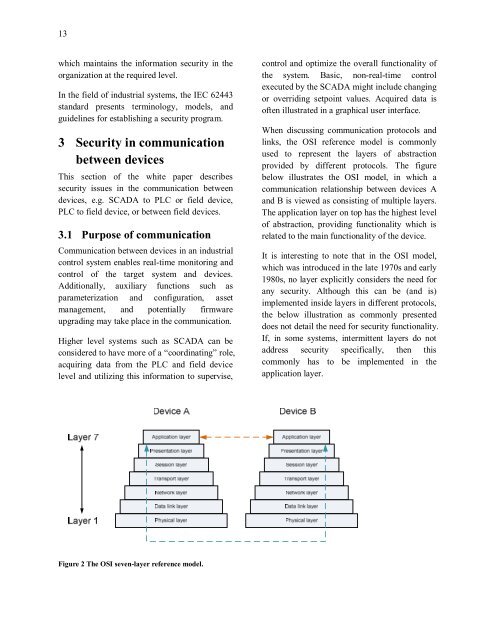
13which ma<strong>in</strong>ta<strong>in</strong>s the <strong>in</strong>formati<strong>on</strong> <strong>security</strong> <strong>in</strong> theorganizati<strong>on</strong> at the required level.In the field of <strong><strong>in</strong>dustrial</strong> systems, the IEC 62443st<strong>and</strong>ard presents term<strong>in</strong>ology, models, <strong>and</strong>guidel<strong>in</strong>es for establish<strong>in</strong>g a <strong>security</strong> program.3 Security <strong>in</strong> communicati<strong>on</strong>between devicesThis secti<strong>on</strong> of the <str<strong>on</strong>g>white</str<strong>on</strong>g> <str<strong>on</strong>g>paper</str<strong>on</strong>g> describes<strong>security</strong> issues <strong>in</strong> the communicati<strong>on</strong> betweendevices, e.g. SCADA to PLC or field device,PLC to field device, or between field devices.3.1 Purpose of communicati<strong>on</strong>Communicati<strong>on</strong> between devices <strong>in</strong> an <strong><strong>in</strong>dustrial</strong>c<strong>on</strong>trol system enables real-time m<strong>on</strong>itor<strong>in</strong>g <strong>and</strong>c<strong>on</strong>trol of the target system <strong>and</strong> devices.Additi<strong>on</strong>ally, auxiliary functi<strong>on</strong>s such asparameterizati<strong>on</strong> <strong>and</strong> c<strong>on</strong>figurati<strong>on</strong>, assetmanagement, <strong>and</strong> potentially firmwareupgrad<strong>in</strong>g may take place <strong>in</strong> the communicati<strong>on</strong>.Higher level systems such as SCADA can bec<strong>on</strong>sidered to have more of a “coord<strong>in</strong>at<strong>in</strong>g” role,acquir<strong>in</strong>g data from the PLC <strong>and</strong> field devicelevel <strong>and</strong> utiliz<strong>in</strong>g this <strong>in</strong>formati<strong>on</strong> to supervise,c<strong>on</strong>trol <strong>and</strong> optimize the overall functi<strong>on</strong>ality ofthe system. Basic, n<strong>on</strong>-real-time c<strong>on</strong>trolexecuted by the SCADA might <strong>in</strong>clude chang<strong>in</strong>gor overrid<strong>in</strong>g setpo<strong>in</strong>t values. Acquired data isoften illustrated <strong>in</strong> a graphical user <strong>in</strong>terface.When discuss<strong>in</strong>g communicati<strong>on</strong> protocols <strong>and</strong>l<strong>in</strong>ks, the OSI reference model is comm<strong>on</strong>lyused to represent the layers of abstracti<strong>on</strong>provided by different protocols. The figurebelow illustrates the OSI model, <strong>in</strong> which acommunicati<strong>on</strong> relati<strong>on</strong>ship between devices A<strong>and</strong> B is viewed as c<strong>on</strong>sist<strong>in</strong>g of multiple layers.The applicati<strong>on</strong> layer <strong>on</strong> top has the highest levelof abstracti<strong>on</strong>, provid<strong>in</strong>g functi<strong>on</strong>ality which isrelated to the ma<strong>in</strong> functi<strong>on</strong>ality of the device.It is <strong>in</strong>terest<strong>in</strong>g to note that <strong>in</strong> the OSI model,which was <strong>in</strong>troduced <strong>in</strong> the late 1970s <strong>and</strong> early1980s, no layer explicitly c<strong>on</strong>siders the need forany <strong>security</strong>. Although this can be (<strong>and</strong> is)implemented <strong>in</strong>side layers <strong>in</strong> different protocols,the below illustrati<strong>on</strong> as comm<strong>on</strong>ly presenteddoes not detail the need for <strong>security</strong> functi<strong>on</strong>ality.If, <strong>in</strong> some systems, <strong>in</strong>termittent layers do notaddress <strong>security</strong> specifically, then thiscomm<strong>on</strong>ly has to be implemented <strong>in</strong> theapplicati<strong>on</strong> layer.Figure 2 The OSI seven-layer reference model.