Persistent Asynchronous and Fileless Backdoor
us-15-Graeber-Abusing-Windows-Management-Instrumentation-WMI-To-Build-A-Persistent Asynchronous-And-Fileless-Backdoor
us-15-Graeber-Abusing-Windows-Management-Instrumentation-WMI-To-Build-A-Persistent Asynchronous-And-Fileless-Backdoor
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
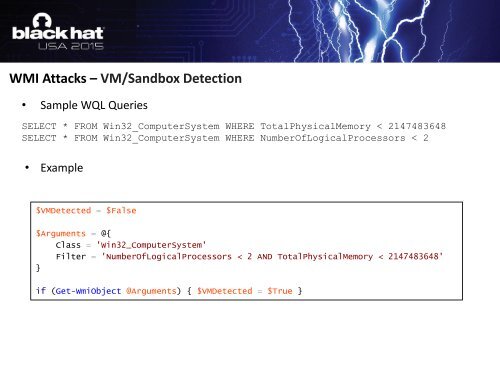
WMI Attacks – VM/S<strong>and</strong>box Detection• Sample WQL QueriesSELECT * FROM Win32_ComputerSystem WHERE TotalPhysicalMemory < 2147483648SELECT * FROM Win32_ComputerSystem WHERE NumberOfLogicalProcessors < 2• Example$VMDetected = $False$Arguments = @{Class = 'Win32_ComputerSystem'Filter = 'NumberOfLogicalProcessors < 2 AND TotalPhysicalMemory < 2147483648'}if (Get-WmiObject @Arguments) { $VMDetected = $True }