Process Control Network Security
Process Control Network Security - Vurore
Process Control Network Security - Vurore
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
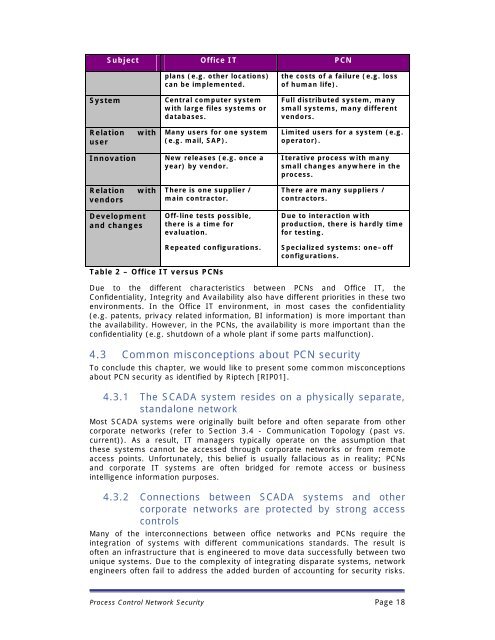
Subject Office IT PCNplans (e.g. other locations)can be implemented.the costs of a failure (e.g. lossof human life).SystemCentral computer systemwith large files systems ordatabases.Full distributed system, manysmall systems, many differentvendors.RelationuserwithMany users for one system(e.g. mail, SAP).Limited users for a system (e.g.operator).InnovationNew releases (e.g. once ayear) by vendor.Iterative process with manysmall changes anywhere in theprocess.RelationvendorswithThere is one supplier /main contractor.There are many suppliers /contractors.Developmentand changesOff-line tests possible,there is a time forevaluation.Repeated configurations.Due to interaction withproduction, there is hardly timefor testing.Specialized systems: one–offconfigurations.Table 2 – Office IT versus PCNsDue to the different characteristics between PCNs and Office IT, theConfidentiality, Integrity and Availability also have different priorities in these twoenvironments. In the Office IT environment, in most cases the confidentiality(e.g. patents, privacy related information, BI information) is more important thanthe availability. However, in the PCNs, the availability is more important than theconfidentiality (e.g. shutdown of a whole plant if some parts malfunction).4.3 Common misconceptions about PCN securityTo conclude this chapter, we would like to present some common misconceptionsabout PCN security as identified by Riptech [RIP01].4.3.1 The SCADA system resides on a physically separate,standalone networkMost SCADA systems were originally built before and often separate from othercorporate networks (refer to Section 3.4 - Communication Topology (past vs.current)). As a result, IT managers typically operate on the assumption thatthese systems cannot be accessed through corporate networks or from remoteaccess points. Unfortunately, this belief is usually fallacious as in reality; PCNsand corporate IT systems are often bridged for remote access or businessintelligence information purposes.4.3.2 Connections between SCADA systems and othercorporate networks are protected by strong accesscontrolsMany of the interconnections between office networks and PCNs require theintegration of systems with different communications standards. The result isoften an infrastructure that is engineered to move data successfully between twounique systems. Due to the complexity of integrating disparate systems, networkengineers often fail to address the added burden of accounting for security risks.<strong>Process</strong> <strong>Control</strong> <strong>Network</strong> <strong>Security</strong> Page 18