Usability and Security
Usability and Security - Vurore
Usability and Security - Vurore
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
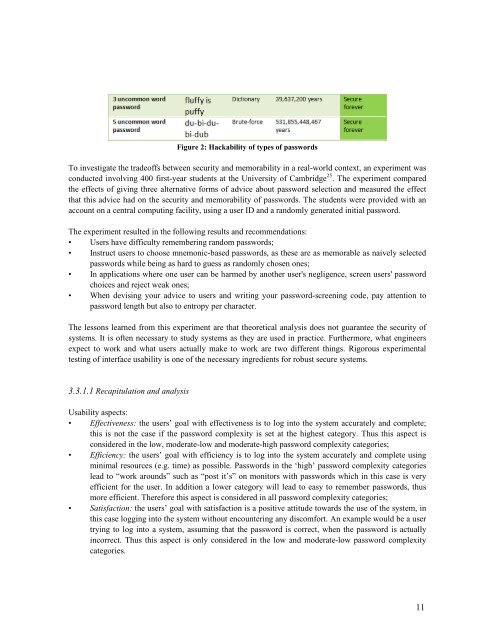
Figure 2: Hackability of types of passwordsTo investigate the tradeoffs between security <strong>and</strong> memorability in a real-world context, an experiment wasconducted involving 400 first-year students at the University of Cambridge 25 . The experiment comparedthe effects of giving three alternative forms of advice about password selection <strong>and</strong> measured the effectthat this advice had on the security <strong>and</strong> memorability of passwords. The students were provided with anaccount on a central computing facility, using a user ID <strong>and</strong> a r<strong>and</strong>omly generated initial password.The experiment resulted in the following results <strong>and</strong> recommendations:• Users have difficulty remembering r<strong>and</strong>om passwords;• Instruct users to choose mnemonic-based passwords, as these are as memorable as naively selectedpasswords while being as hard to guess as r<strong>and</strong>omly chosen ones;• In applications where one user can be harmed by another user's negligence, screen users' passwordchoices <strong>and</strong> reject weak ones;• When devising your advice to users <strong>and</strong> writing your password-screening code, pay attention topassword length but also to entropy per character.The lessons learned from this experiment are that theoretical analysis does not guarantee the security ofsystems. It is often necessary to study systems as they are used in practice. Furthermore, what engineersexpect to work <strong>and</strong> what users actually make to work are two different things. Rigorous experimentaltesting of interface usability is one of the necessary ingredients for robust secure systems.3.3.1.1 Recapitulation <strong>and</strong> analysis<strong>Usability</strong> aspects:• Effectiveness: the users’ goal with effectiveness is to log into the system accurately <strong>and</strong> complete;this is not the case if the password complexity is set at the highest category. Thus this aspect isconsidered in the low, moderate-low <strong>and</strong> moderate-high password complexity categories;• Efficiency: the users’ goal with efficiency is to log into the system accurately <strong>and</strong> complete usingminimal resources (e.g. time) as possible. Passwords in the ‘high’ password complexity categorieslead to “work arounds” such as “post it’s” on monitors with passwords which in this case is veryefficient for the user. In addition a lower category will lead to easy to remember passwords, thusmore efficient. Therefore this aspect is considered in all password complexity categories;• Satisfaction: the users’ goal with satisfaction is a positive attitude towards the use of the system, inthis case logging into the system without encountering any discomfort. An example would be a usertrying to log into a system, assuming that the password is correct, when the password is actuallyincorrect. Thus this aspect is only considered in the low <strong>and</strong> moderate-low password complexitycategories.11