4.0
1IZ1TDd
1IZ1TDd
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
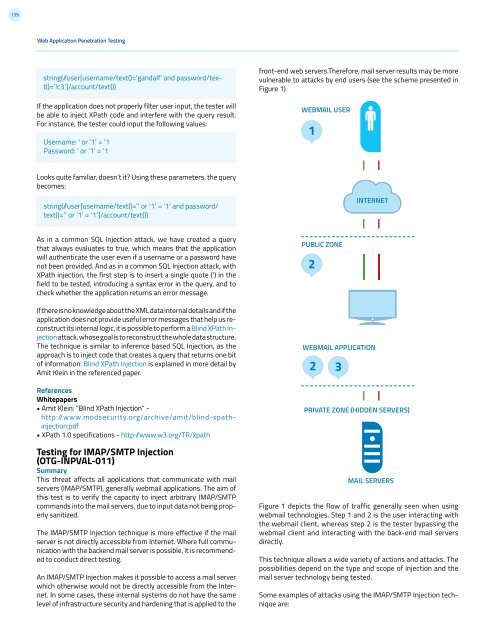
139Web Application Penetration Testingstring( /user[username/text()=’gandalf’ and password/text()=’!c3’]/account/text())If the application does not properly filter user input, the tester willbe able to inject XPath code and interfere with the query result.For instance, the tester could input the following values:Username: ‘ or ‘1’ = ‘1Password: ‘ or ‘1’ = ‘1front-end web servers.Therefore, mail server results may be morevulnerable to attacks by end users (see the scheme presented inFigure 1).WEBMAIL USER1Looks quite familiar, doesn’t it? Using these parameters, the querybecomes:string( /user[username/text()=’’ or ‘1’ = ‘1’ and password/text()=’’ or ‘1’ = ‘1’]/account/text())INTERNETAs in a common SQL Injection attack, we have created a querythat always evaluates to true, which means that the applicationwill authenticate the user even if a username or a password havenot been provided. And as in a common SQL Injection attack, withXPath injection, the first step is to insert a single quote (‘) in thefield to be tested, introducing a syntax error in the query, and tocheck whether the application returns an error message.If there is no knowledge about the XML data internal details and if theapplication does not provide useful error messages that help us reconstructits internal logic, it is possible to perform a Blind XPath Injectionattack, whose goal is to reconstruct the whole data structure.The technique is similar to inference based SQL Injection, as theapproach is to inject code that creates a query that returns one bitof information. Blind XPath Injection is explained in more detail byAmit Klein in the referenced paper.ReferencesWhitepapers• Amit Klein: “Blind XPath Injection” -http://www.modsecurity.org/archive/amit/blind-xpathinjection.pdf• XPath 1.0 specifications - http: /www.w3.org/TR/xpathTesting for IMAP/SMTP Injection(OTG-INPVAL-011)SummaryThis threat affects all applications that communicate with mailservers (IMAP/SMTP), generally webmail applications. The aim ofthis test is to verify the capacity to inject arbitrary IMAP/SMTPcommands into the mail servers, due to input data not being properlysanitized.The IMAP/SMTP Injection technique is more effective if the mailserver is not directly accessible from Internet. Where full communicationwith the backend mail server is possible, it is recommendedto conduct direct testing.An IMAP/SMTP Injection makes it possible to access a mail serverwhich otherwise would not be directly accessible from the Internet.In some cases, these internal systems do not have the samelevel of infrastructure security and hardening that is applied to thePUBLIC ZONE2WEBMAIL APPLICATION2 3PRIVATE ZONE (HIDDEN SERVERS)MAIL SERVERSFigure 1 depicts the flow of traffic generally seen when usingwebmail technologies. Step 1 and 2 is the user interacting withthe webmail client, whereas step 2 is the tester bypassing thewebmail client and interacting with the back-end mail serversdirectly.This technique allows a wide variety of actions and attacks. Thepossibilities depend on the type and scope of injection and themail server technology being tested.Some examples of attacks using the IMAP/SMTP Injection techniqueare: