CYBER SECURITY INCIDENT MANAGEMENT GUIDE
Cyber-Security-Incident-Management-Guide-2015
Cyber-Security-Incident-Management-Guide-2015
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
01 PREPARING FOR A <strong>CYBER</strong> <strong>SECURITY</strong> <strong>INCIDENT</strong> 17<br />
THE IMPACT OF THE <strong>INCIDENT</strong> WILL DETERMINE THE<br />
COMMUNICATION OBJECTIVES<br />
In order to know what to communicate to whom, an organisation should assess the<br />
(potential) impact of the cyber security incident: e.g. are only internal or also external<br />
stakeholders concerned? Is there a data leak? Depending on this impact, your cyber<br />
security incident communication will have different objectives, for example:<br />
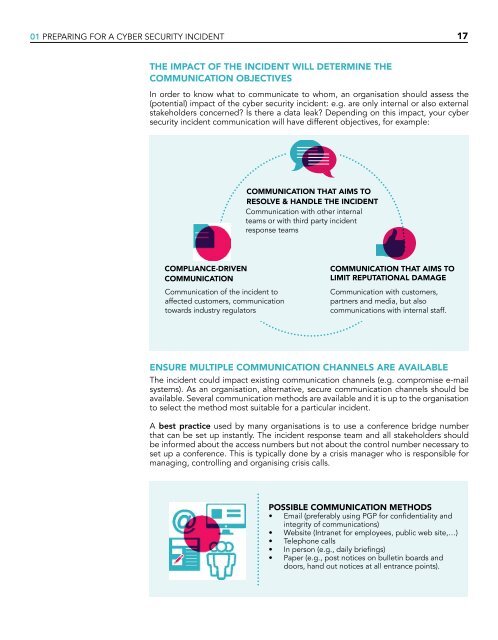
COMMUNICATION THAT AIMS TO<br />
RESOLVE & HANDLE THE <strong>INCIDENT</strong><br />
Communication with other internal<br />
teams or with third party incident<br />
response teams<br />
COMPLIANCE-DRIVEN<br />
COMMUNICATION<br />
Communication of the incident to<br />
affected customers, communication<br />
towards industry regulators<br />
COMMUNICATION THAT AIMS TO<br />
LIMIT REPUTATIONAL DAMAGE<br />
Communication with customers,<br />
partners and media, but also<br />
communications with internal staff.<br />
ENSURE MULTIPLE COMMUNICATION CHANNELS ARE AVAILABLE<br />
The incident could impact existing communication channels (e.g. compromise e-mail<br />
systems). As an organisation, alternative, secure communication channels should be<br />
available. Several communication methods are available and it is up to the organisation<br />
to select the method most suitable for a particular incident.<br />
A best practice used by many organisations is to use a conference bridge number<br />
that can be set up instantly. The incident response team and all stakeholders should<br />
be informed about the access numbers but not about the control number necessary to<br />
set up a conference. This is typically done by a crisis manager who is responsible for<br />
managing, controlling and organising crisis calls.<br />
POSSIBLE COMMUNICATION METHODS<br />
• Email (preferably using PGP for confidentiality and<br />
integrity of communications)<br />
• Website (Intranet for employees, public web site,…)<br />
• Telephone calls<br />
• In person (e.g., daily briefings)<br />
• Paper (e.g., post notices on bulletin boards and<br />
doors, hand out notices at all entrance points).