EXPANDED
us-16-Malone-Using-an-Expanded-Cyber-Kill-Chain-Model-to-Increase-Attack-Resiliency
us-16-Malone-Using-an-Expanded-Cyber-Kill-Chain-Model-to-Increase-Attack-Resiliency
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
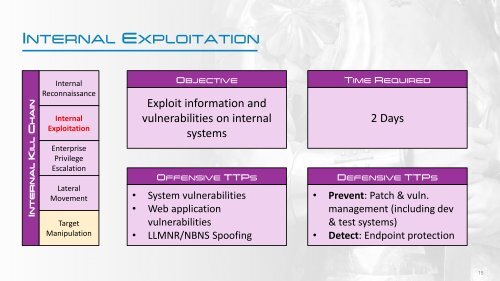
INTERNAL EXPLOITATION<br />
INTERNAL KILL CHAIN<br />
Internal<br />
Reconnaissance<br />
Internal<br />
Exploitation<br />
Enterprise<br />
Privilege<br />
Escalation<br />
Lateral<br />
Movement<br />
Target<br />
Manipulation<br />
OBJECTIVE<br />
Exploit information and<br />
vulnerabilities on internal<br />
systems<br />
OFFENSIVE TTPS<br />
• System vulnerabilities<br />
• Web application<br />
vulnerabilities<br />
• LLMNR/NBNS Spoofing<br />
TIME REQUIRED<br />
2 Days<br />
DEFENSIVE TTPS<br />
• Prevent: Patch & vuln.<br />
management (including dev<br />
& test systems)<br />
• Detect: Endpoint protection<br />
15