EXPANDED
us-16-Malone-Using-an-Expanded-Cyber-Kill-Chain-Model-to-Increase-Attack-Resiliency
us-16-Malone-Using-an-Expanded-Cyber-Kill-Chain-Model-to-Increase-Attack-Resiliency
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
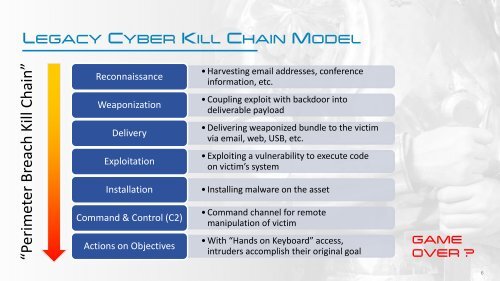
LEGACY CYBER KILL CHAIN MODEL<br />
“Perimeter Breach Kill Chain”<br />
Reconnaissance<br />
Weaponization<br />
Delivery<br />
Exploitation<br />
Installation<br />
Command & Control (C2)<br />
Actions on Objectives<br />
• Harvesting email addresses, conference<br />
information, etc.<br />
• Coupling exploit with backdoor into<br />
deliverable payload<br />
• Delivering weaponized bundle to the victim<br />
via email, web, USB, etc.<br />
• Exploiting a vulnerability to execute code<br />
on victim’s system<br />
• Installing malware on the asset<br />
• Command channel for remote<br />
manipulation of victim<br />
• With “Hands on Keyboard” access,<br />
intruders accomplish their original goal<br />
GAME<br />
OVER ?<br />
6