EXPANDED
us-16-Malone-Using-an-Expanded-Cyber-Kill-Chain-Model-to-Increase-Attack-Resiliency
us-16-Malone-Using-an-Expanded-Cyber-Kill-Chain-Model-to-Increase-Attack-Resiliency
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
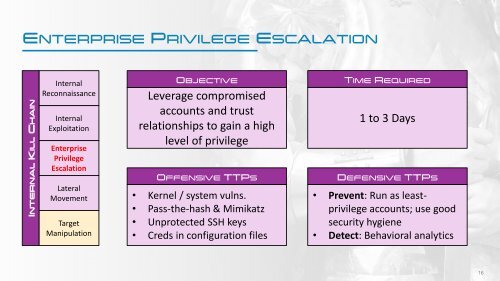
ENTERPRISE PRIVILEGE ESCALATION<br />
INTERNAL KILL CHAIN<br />
Internal<br />
Reconnaissance<br />
Internal<br />
Exploitation<br />
Enterprise<br />
Privilege<br />
Escalation<br />
Lateral<br />
Movement<br />
Target<br />
Manipulation<br />
OBJECTIVE<br />
Leverage compromised<br />
accounts and trust<br />
relationships to gain a high<br />
level of privilege<br />
OFFENSIVE TTPS<br />
• Kernel / system vulns.<br />
• Pass-the-hash & Mimikatz<br />
• Unprotected SSH keys<br />
• Creds in configuration files<br />
TIME REQUIRED<br />
1 to 3 Days<br />
DEFENSIVE TTPS<br />
• Prevent: Run as leastprivilege<br />
accounts; use good<br />
security hygiene<br />
• Detect: Behavioral analytics<br />
16