Pegasus for Android
eatsvTG
eatsvTG
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Communication Methods<br />
Similar to the iOS version of <strong>Pegasus</strong>, its <strong>Android</strong> equivalent is capable of communicating to<br />
attacker-controlled infrastructure via a number of different mechanisms and protocols. This<br />
includes via SMS, over HTTP, and through the Message Queue Telemetry Transport (MQTT)<br />
protocol. The following sections detail how the <strong>Android</strong> version of <strong>Pegasus</strong> utilizes each of these<br />
mechanisms and protocols.<br />
HTTP Communication<br />
The application beacons out to a web server at a configurable time interval. The IP address and<br />
port of the server can be set through:<br />
1. A command included in the initial configuration.<br />
2. A command sent via SMS.<br />
3. A command sent in an HTTP response from an existing C2 server.<br />
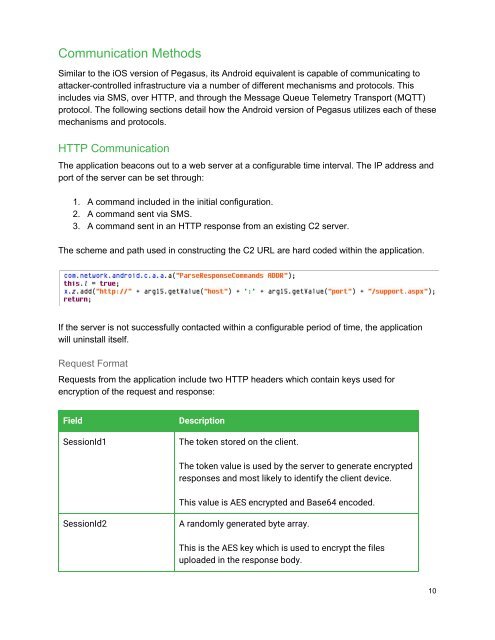
The scheme and path used in constructing the C2 URL are hard coded within the application.<br />
If the server is not successfully contacted within a configurable period of time, the application<br />
will uninstall itself.<br />
Request Format<br />
Requests from the application include two HTTP headers which contain keys used <strong>for</strong><br />
encryption of the request and response:<br />
Field<br />
SessionId1<br />
Description<br />
The token stored on the client.<br />
The token value is used by the server to generate encrypted<br />
responses and most likely to identify the client device.<br />
This value is AES encrypted and Base64 encoded.<br />
SessionId2<br />
A randomly generated byte array.<br />
This is the AES key which is used to encrypt the files<br />
uploaded in the response body.<br />
10