Cyber Defense eMagazine October Edition for 2021
Cyber Defense eMagazine October Edition for 2021 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, US Editor-in-Chief, Pieruligi Paganini, International Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES #CYBERSECURITYAWARENESSMONTH
Cyber Defense eMagazine October Edition for 2021 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, US Editor-in-Chief, Pieruligi Paganini, International Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES #CYBERSECURITYAWARENESSMONTH
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Part 1 - Using a Proxy Server – BURP<br />
When we mention the use of a proxy server, we are basically referring to intercepting and analyzing<br />
requests related to the HTTP (Hypertext Transfer Protocol), whether the one with the TLS (Transport<br />
Layer Security) security layer or not.<br />
Some of the applications we have on our smartphones still only use the HTTP protocol, which means<br />
that data travels in plain text <strong>for</strong>m, that is, without any encryption, making sensitive in<strong>for</strong>mation fully<br />
exposed to any attacker who adopts techniques man in the middle.<br />
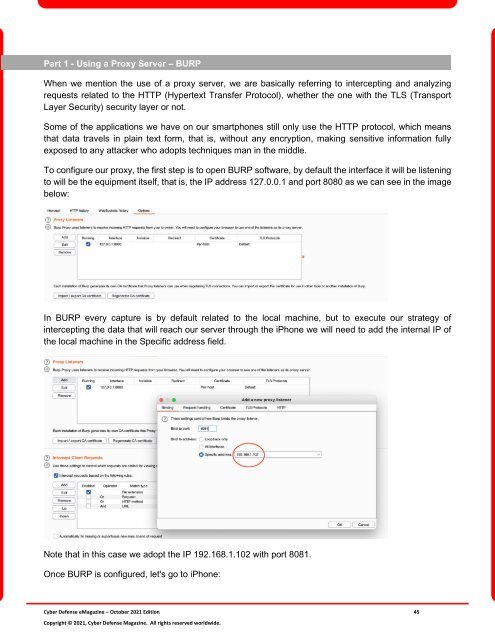
To configure our proxy, the first step is to open BURP software, by default the interface it will be listening<br />
to will be the equipment itself, that is, the IP address 127.0.0.1 and port 8080 as we can see in the image<br />
below:<br />
In BURP every capture is by default related to the local machine, but to execute our strategy of<br />
intercepting the data that will reach our server through the iPhone we will need to add the internal IP of<br />
the local machine in the Specific address field.<br />
Note that in this case we adopt the IP 192.168.1.102 with port 8081.<br />
Once BURP is configured, let's go to iPhone:<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>October</strong> <strong>2021</strong> <strong>Edition</strong> 45<br />
Copyright © <strong>2021</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.