Cyber Defense eMagazine October Edition for 2021
Cyber Defense eMagazine October Edition for 2021 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, US Editor-in-Chief, Pieruligi Paganini, International Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES #CYBERSECURITYAWARENESSMONTH
Cyber Defense eMagazine October Edition for 2021 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, US Editor-in-Chief, Pieruligi Paganini, International Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES #CYBERSECURITYAWARENESSMONTH
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
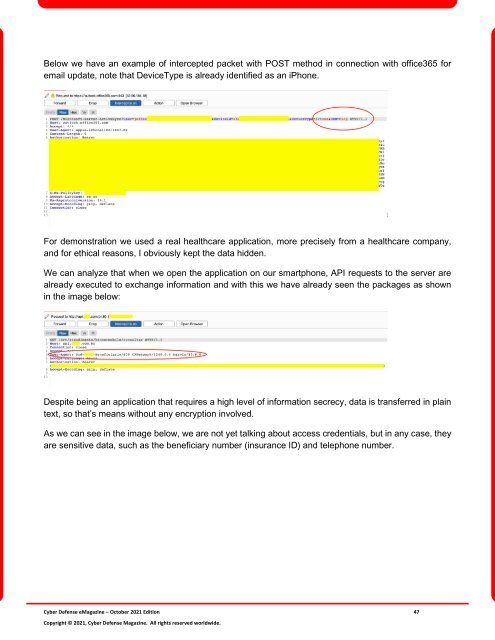
Below we have an example of intercepted packet with POST method in connection with office365 <strong>for</strong><br />
email update, note that DeviceType is already identified as an iPhone.<br />
For demonstration we used a real healthcare application, more precisely from a healthcare company,<br />
and <strong>for</strong> ethical reasons, I obviously kept the data hidden.<br />
We can analyze that when we open the application on our smartphone, API requests to the server are<br />
already executed to exchange in<strong>for</strong>mation and with this we have already seen the packages as shown<br />
in the image below:<br />
Despite being an application that requires a high level of in<strong>for</strong>mation secrecy, data is transferred in plain<br />
text, so that’s means without any encryption involved.<br />
As we can see in the image below, we are not yet talking about access credentials, but in any case, they<br />
are sensitive data, such as the beneficiary number (insurance ID) and telephone number.<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>October</strong> <strong>2021</strong> <strong>Edition</strong> 47<br />
Copyright © <strong>2021</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.