download issue 24 here - Help Net Security
download issue 24 here - Help Net Security
download issue 24 here - Help Net Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
The single tool trap<br />
Scanning tools are an essential part of every<br />
AppSec strategy, and so is choosing the right<br />
one. Fortunately, ASVS provides enough<br />
guidance on what vulnerabilities a tool should<br />
be able to look for.<br />
No one tool can do everything well. According<br />
to an evaluation on application security scanning<br />
tools, carried out by the US NSA Center<br />
for Assured Software, the best coverage one<br />
can get with a single tool is detection of<br />
60.3% of the vulnerabilities of an application.<br />
Other studies show similar or lower rates.<br />
While tools are very useful and necessary for<br />
attaining good efficiency levels in application<br />
security testing, trying to create a strategy<br />
around one particular tool may be a mistake.<br />
The application security testing strategy<br />
should leverage the right tools, at the right<br />
place and time.<br />
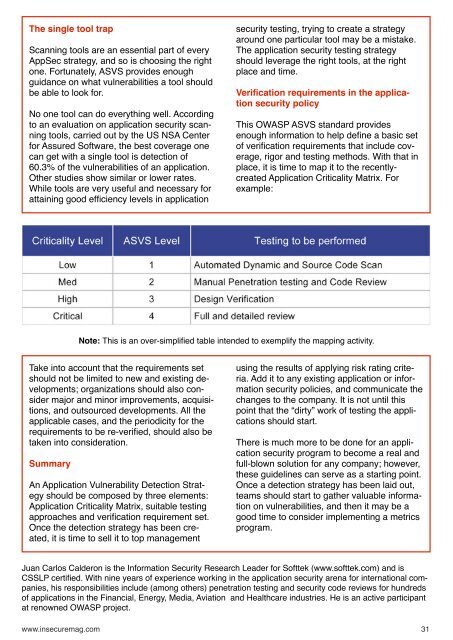
Verification requirements in the application<br />
security policy<br />
This OWASP ASVS standard provides<br />
enough information to help define a basic set<br />
of verification requirements that include coverage,<br />
rigor and testing methods. With that in<br />
place, it is time to map it to the recentlycreated<br />
Application Criticality Matrix. For<br />
example:<br />
Note: This is an over-simplified table intended to exemplify the mapping activity.<br />
Take into account that the requirements set<br />
should not be limited to new and existing developments;<br />
organizations should also consider<br />
major and minor improvements, acquisitions,<br />
and outsourced developments. All the<br />
applicable cases, and the periodicity for the<br />
requirements to be re-verified, should also be<br />
taken into consideration.<br />
Summary<br />
An Application Vulnerability Detection Strategy<br />
should be composed by three elements:<br />
Application Criticality Matrix, suitable testing<br />
approaches and verification requirement set.<br />
Once the detection strategy has been created,<br />
it is time to sell it to top management<br />
using the results of applying risk rating criteria.<br />
Add it to any existing application or information<br />
security policies, and communicate the<br />
changes to the company. It is not until this<br />
point that the “dirty” work of testing the applications<br />
should start.<br />
T<strong>here</strong> is much more to be done for an application<br />
security program to become a real and<br />
full-blown solution for any company; however,<br />
these guidelines can serve as a starting point.<br />
Once a detection strategy has been laid out,<br />
teams should start to gather valuable information<br />
on vulnerabilities, and then it may be a<br />
good time to consider implementing a metrics<br />
program.<br />
Juan Carlos Calderon is the Information <strong>Security</strong> Research Leader for Softtek (www.softtek.com) and is<br />
CSSLP certified. With nine years of experience working in the application security arena for international companies,<br />
his responsibilities include (among others) penetration testing and security code reviews for hundreds<br />
of applications in the Financial, Energy, Media, Aviation and Healthcare industries. He is an active participant<br />
at renowned OWASP project.<br />
www.insecuremag.com 31