download issue 24 here - Help Net Security
download issue 24 here - Help Net Security
download issue 24 here - Help Net Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
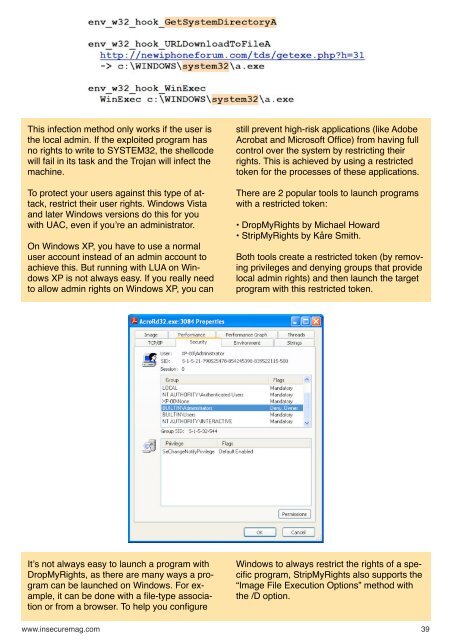
This infection method only works if the user is<br />
the local admin. If the exploited program has<br />
no rights to write to SYSTEM32, the shellcode<br />
will fail in its task and the Trojan will infect the<br />
machine.<br />
To protect your users against this type of attack,<br />
restrict their user rights. Windows Vista<br />
and later Windows versions do this for you<br />
with UAC, even if youʼre an administrator.<br />
On Windows XP, you have to use a normal<br />
user account instead of an admin account to<br />
achieve this. But running with LUA on Windows<br />
XP is not always easy. If you really need<br />
to allow admin rights on Windows XP, you can<br />
Itʼs not always easy to launch a program with<br />
DropMyRights, as t<strong>here</strong> are many ways a program<br />
can be launched on Windows. For example,<br />
it can be done with a file-type association<br />
or from a browser. To help you configure<br />
still prevent high-risk applications (like Adobe<br />
Acrobat and Microsoft Office) from having full<br />
control over the system by restricting their<br />
rights. This is achieved by using a restricted<br />
token for the processes of these applications.<br />
T<strong>here</strong> are 2 popular tools to launch programs<br />
with a restricted token:<br />
• DropMyRights by Michael Howard<br />
• StripMyRights by Kåre Smith.<br />
Both tools create a restricted token (by removing<br />
privileges and denying groups that provide<br />
local admin rights) and then launch the target<br />
program with this restricted token.<br />
Windows to always restrict the rights of a specific<br />
program, StripMyRights also supports the<br />
“Image File Execution Options” method with<br />
the /D option.<br />
www.insecuremag.com 39