Slides do Módulo de Criptografia - Si.lopesgazzani.com.br
Slides do Módulo de Criptografia - Si.lopesgazzani.com.br
Slides do Módulo de Criptografia - Si.lopesgazzani.com.br
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
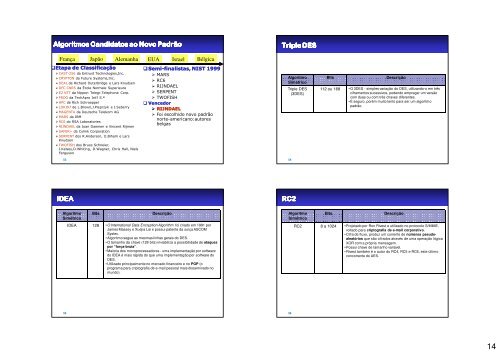
Algoritmos Algoritmos Candidatos Candidatos Candidatos Candidatos ao ao Novo Novo Novo Novo Novo Padrão<<strong>br</strong> />
Padrão<<strong>br</strong> />
França Japão Alemanha EUA Israel Bélgica<<strong>br</strong> />
Etapa Etapa <strong>de</strong> Classificação<<strong>br</strong> />
CAST-256 da Entrust Technologies,Inc.<<strong>br</strong> />
CRYPTON da Future Systems,Inc.<<strong>br</strong> />
DEAL <strong>de</strong> Richard Outer<strong>br</strong>idge e Lars Knudsen<<strong>br</strong> />
DFC CNRS da Ècole Normale Superieure<<strong>br</strong> />
E2 NTT da Nippon Telegr.Telephone Corp.<<strong>br</strong> />
FROG da TechApro Int’l S.ª<<strong>br</strong> />
HPC <strong>de</strong> Rich Schroeppel<<strong>br</strong> />
LOKI97 <strong>de</strong> L.Brown,J.Pieprzyk e J.Seberry<<strong>br</strong> />
MAGENTA da Deutsche Telekom AG<<strong>br</strong> />
MARS da IBM<<strong>br</strong> />
RC6 <strong>do</strong> RSA Laboratories<<strong>br</strong> />
RIJNDAEL da Joan Daemen e Vincent Rijmen<<strong>br</strong> />
SAFER+ da Cylink Corporation<<strong>br</strong> />
SERPENT <strong>do</strong>s R.An<strong>de</strong>rson, E.Biham e Lars<<strong>br</strong> />
Knudsen<<strong>br</strong> />
TWOFISH <strong>do</strong>s Bruce Schneier,<<strong>br</strong> />
J.Kelsey,D.Whiting, D.Wagner, Chris Hall, Niels<<strong>br</strong> />
Ferguson<<strong>br</strong> />
53<<strong>br</strong> />
IDEA<<strong>br</strong> />
IDEA<<strong>br</strong> />
Algoritmo<<strong>br</strong> />
<strong>Si</strong>métrico<<strong>br</strong> />
55<<strong>br</strong> />
Bits Descrição<<strong>br</strong> />
Semi Semi-finalistas, finalistas, NIST 1999<<strong>br</strong> />
MARS<<strong>br</strong> />
RC6<<strong>br</strong> />
RIJNDAEL<<strong>br</strong> />
SERPENT<<strong>br</strong> />
TWOFISH<<strong>br</strong> />
Vence<strong>do</strong>r<<strong>br</strong> />
RIJNDAEL<<strong>br</strong> />
Foi escolhi<strong>do</strong> novo padrão<<strong>br</strong> />
norte-americano:autores<<strong>br</strong> />
belgas<<strong>br</strong> />
IDEA 128 •O International Data Encryption Algorithm foi cria<strong>do</strong> em 1991 por<<strong>br</strong> />
James Massey e Xuejia Lai e possui patente da suíça ASCOM<<strong>br</strong> />
Systec.<<strong>br</strong> />
•Algoritmo segue as mesmas linhas gerais <strong>do</strong> DES.<<strong>br</strong> />
•O tamanho da chave (128 bits) inviabiliza a possibilida<strong>de</strong> <strong>de</strong> ataques<<strong>br</strong> />
por “força-<strong>br</strong>uta”.<<strong>br</strong> />
•Maioria <strong>do</strong>s microprocessa<strong>do</strong>res - uma implementação por software<<strong>br</strong> />
<strong>do</strong> IDEA é mais rápida <strong>do</strong> que uma implementação por software <strong>do</strong><<strong>br</strong> />
DES.<<strong>br</strong> />
•Utiliza<strong>do</strong> principalmente no merca<strong>do</strong> financeiro e no PGP (o<<strong>br</strong> />
programa para criptografia <strong>de</strong> e-mail pessoal mais dissemina<strong>do</strong> no<<strong>br</strong> />
mun<strong>do</strong>).<<strong>br</strong> />
Triple Triple Triple Triple Triple DES<<strong>br</strong> />
DES<<strong>br</strong> />
Algoritmo<<strong>br</strong> />
<strong>Si</strong>métrico<<strong>br</strong> />
Triple DES<<strong>br</strong> />
(3DES)<<strong>br</strong> />
54<<strong>br</strong> />
RC2<<strong>br</strong> />
RC2 RC2 RC2<<strong>br</strong> />
Algoritmo<<strong>br</strong> />
<strong>Si</strong>métrico<<strong>br</strong> />
56<<strong>br</strong> />
Bits Descrição<<strong>br</strong> />
112 ou 168<<strong>br</strong> />
•O 3DES - simples variação <strong>do</strong> DES, utilizan<strong>do</strong>-o em três<<strong>br</strong> />
ciframentos sucessivos, po<strong>de</strong>n<strong>do</strong> empregar um versão<<strong>br</strong> />
<strong>com</strong> duas ou <strong>com</strong> três chaves diferentes.<<strong>br</strong> />
•É seguro, porém muito lento para ser um algoritmo<<strong>br</strong> />
padrão.<<strong>br</strong> />
Bits Descrição<<strong>br</strong> />
RC2 8 a 1024 •Projeta<strong>do</strong> por Ron Rivest e utiliza<strong>do</strong> no protocolo S/MIME,<<strong>br</strong> />
volta<strong>do</strong> para criptografia <strong>de</strong> e-mail corporativo.<<strong>br</strong> />
•Cifra <strong>de</strong> fluxo, produz um corrente <strong>de</strong> números pseu<strong>do</strong>aleatórios<<strong>br</strong> />
que são cifra<strong>do</strong>s através <strong>de</strong> uma operação lógica<<strong>br</strong> />
XOR <strong>com</strong> a própria mensagem.<<strong>br</strong> />
•Possui chave <strong>de</strong> tamanho variável.<<strong>br</strong> />
•Rivest também é o autor <strong>do</strong> RC4, RC5 e RC6, este último<<strong>br</strong> />
concorrente <strong>do</strong> AES.<<strong>br</strong> />
14