Slides do Módulo de Criptografia - Si.lopesgazzani.com.br
Slides do Módulo de Criptografia - Si.lopesgazzani.com.br
Slides do Módulo de Criptografia - Si.lopesgazzani.com.br
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
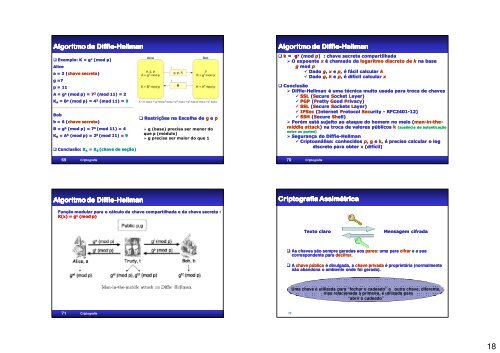
Algoritmo Algoritmo <strong>de</strong> <strong>de</strong> Diffie Diffie-Hellman<<strong>br</strong> />
Diffie Hellman<<strong>br</strong> />
Hellman<<strong>br</strong> />
Exemplo: K = gx (mod mod p)<<strong>br</strong> />
Alice<<strong>br</strong> />
a = 3 ( (chave chave secreta secreta)<<strong>br</strong> />
g =7<<strong>br</strong> />
p = 11<<strong>br</strong> />
A = ga (mod mod p) = 7 3 (mod mod 11) = 2<<strong>br</strong> />
KA = Ba (mod mod p) = 4 3 (mod mod 11) = 9<<strong>br</strong> />
Bob<<strong>br</strong> />
b = 6 ( (chave chave secreta secreta)<<strong>br</strong> />
B = gb (mod mod p) = 7 6 (mod mod 11) = 4<<strong>br</strong> />
KB = A Ab (mod mod p) = 2 6 (mod mod 11) = 9<<strong>br</strong> />
Conclusão: KA = K B (chave <strong>de</strong> seção)<<strong>br</strong> />
69 <strong>Criptografia</strong><<strong>br</strong> />
Algoritmo Algoritmo <strong>de</strong> <strong>de</strong> Diffie Diffie-Hellman<<strong>br</strong> />
Diffie Hellman<<strong>br</strong> />
Hellman<<strong>br</strong> />
71 <strong>Criptografia</strong><<strong>br</strong> />
Restrições na Escolha <strong>de</strong> g e p<<strong>br</strong> />
g (base) precisa ser menor <strong>do</strong><<strong>br</strong> />
que p (módulo)<<strong>br</strong> />
g precisa ser maior <strong>do</strong> que 1<<strong>br</strong> />
Função modular para o cálculo da chave <strong>com</strong>partilhada e da chave secreta :<<strong>br</strong> />
K(x) = gx (mod mod p)<<strong>br</strong> />
Algoritmo Algoritmo Algoritmo Algoritmo <strong>de</strong> <strong>de</strong> Diffie Diffie-Hellman<<strong>br</strong> />
Diffie Hellman<<strong>br</strong> />
Hellman<<strong>br</strong> />
k = gx (mod (mod p) ) : chave secreta <strong>com</strong>partilhada<<strong>br</strong> />
O expoente x é chama<strong>do</strong> <strong>de</strong> logaritmo discreto <strong>de</strong> k na base<<strong>br</strong> />
g mod p<<strong>br</strong> />
Da<strong>do</strong> g, , x e p, , é fácil calcular k<<strong>br</strong> />
Da<strong>do</strong> g, , k e p, , é difícil calcular x<<strong>br</strong> />
Conclusão<<strong>br</strong> />
Diffie Diffie-Hellman Hellman é uma técnica muito usada para troca <strong>de</strong> chaves<<strong>br</strong> />
SSL (Secure ecure Socket ocket Layer) ayer)<<strong>br</strong> />
PGP (Pretty retty Good ood Privacy rivacy)<<strong>br</strong> />
SSL (Secure ecure Sockets ockets Layer ayer)<<strong>br</strong> />
IPSec (Internet nternet Protocol rotocol Sec Security urity - RFC2401-12<<strong>br</strong> />
RFC2401 12)<<strong>br</strong> />
SSH (Secure ecure Shell)<<strong>br</strong> />
Porém está sujeito ao ataque <strong>do</strong> homem no meio (man man-in in-the the-<<strong>br</strong> />
middle attack attack) ) na troca <strong>de</strong> valores públicos k (ausência ausência <strong>de</strong> autenticação<<strong>br</strong> />
entre as partes) partes<<strong>br</strong> />
Segurança <strong>do</strong> Diffie-Hellman<<strong>br</strong> />
Diffie Hellman<<strong>br</strong> />
Criptoanálise<<strong>br</strong> />
Criptoanálise: : conheci<strong>do</strong>s p, , g e k, , é preciso calcular o log<<strong>br</strong> />
discreto para obter x (difícil difícil)<<strong>br</strong> />
70 <strong>Criptografia</strong><<strong>br</strong> />
<strong>Criptografia</strong> <strong>Criptografia</strong> Assimétrica<<strong>br</strong> />
Assimétrica<<strong>br</strong> />
72<<strong>br</strong> />
Texto claro Mensagem cifrada<<strong>br</strong> />
As chaves são sempre geradas aos pares pares: : uma para cifrar e a sua<<strong>br</strong> />
correspon<strong>de</strong>nte para <strong>de</strong>cifrar <strong>de</strong>cifrar.<<strong>br</strong> />
A chave pública é divulgada, a chave privada é proprietária (normalmente<<strong>br</strong> />
não aban<strong>do</strong>na o ambiente on<strong>de</strong> foi gerada).<<strong>br</strong> />
Uma chave é utilizada para “fechar o ca<strong>de</strong>a<strong>do</strong>” e outra chave, diferente,<<strong>br</strong> />
mas relacionada à primeira, é utilizada para<<strong>br</strong> />
“a<strong>br</strong>ir o ca<strong>de</strong>a<strong>do</strong>”<<strong>br</strong> />
18