Proactive Security Management - Large Enterprise Business - HP
Proactive Security Management - Large Enterprise Business - HP
Proactive Security Management - Large Enterprise Business - HP
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
program identifies and prioritizes critical patches. It conducts system audits to ensure compliance and<br />
calculates business risks associated with newly identified vulnerabilities. <strong>HP</strong> can provide the right level<br />
of solution for any business requirement.<br />
Active Countermeasures<br />
Organizations need to be prepared to deal with unpreventable, fast-spreading attacks. Known<br />
problems, whether fast or slow, can be prevented. Organizations experiencing slow, unknown<br />
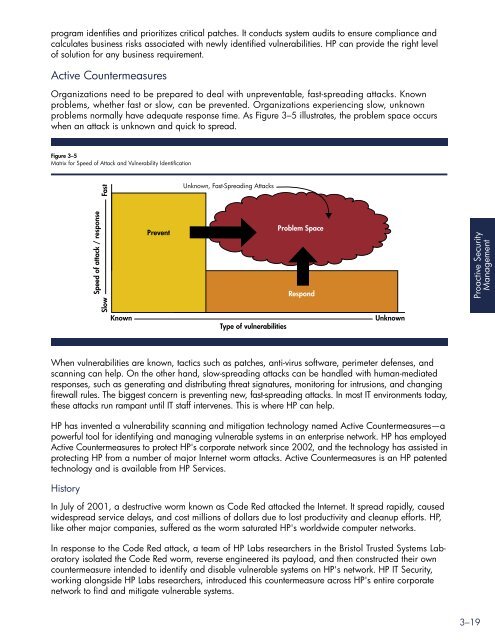
problems normally have adequate response time. As Figure 3–5 illustrates, the problem space occurs<br />
when an attack is unknown and quick to spread.<br />
Figure 3–5<br />
Matrix for Speed of Attack and Vulnerability Identification<br />
When vulnerabilities are known, tactics such as patches, anti-virus software, perimeter defenses, and<br />
scanning can help. On the other hand, slow-spreading attacks can be handled with human-mediated<br />
responses, such as generating and distributing threat signatures, monitoring for intrusions, and changing<br />
firewall rules. The biggest concern is preventing new, fast-spreading attacks. In most IT environments today,<br />
these attacks run rampant until IT staff intervenes. This is where <strong>HP</strong> can help.<br />
<strong>HP</strong> has invented a vulnerability scanning and mitigation technology named Active Countermeasures—a<br />
powerful tool for identifying and managing vulnerable systems in an enterprise network. <strong>HP</strong> has employed<br />
Active Countermeasures to protect <strong>HP</strong>'s corporate network since 2002, and the technology has assisted in<br />
protecting <strong>HP</strong> from a number of major Internet worm attacks. Active Countermeasures is an <strong>HP</strong> patented<br />
technology and is available from <strong>HP</strong> Services.<br />
History<br />
In July of 2001, a destructive worm known as Code Red attacked the Internet. It spread rapidly, caused<br />
widespread service delays, and cost millions of dollars due to lost productivity and cleanup efforts. <strong>HP</strong>,<br />
like other major companies, suffered as the worm saturated <strong>HP</strong>'s worldwide computer networks.<br />
In response to the Code Red attack, a team of <strong>HP</strong> Labs researchers in the Bristol Trusted Systems Laboratory<br />
isolated the Code Red worm, reverse engineered its payload, and then constructed their own<br />
countermeasure intended to identify and disable vulnerable systems on <strong>HP</strong>'s network. <strong>HP</strong> IT <strong>Security</strong>,<br />
working alongside <strong>HP</strong> Labs researchers, introduced this countermeasure across <strong>HP</strong>'s entire corporate<br />
network to find and mitigate vulnerable systems.<br />
<strong>Proactive</strong> <strong>Security</strong><br />
<strong>Management</strong><br />
3–19