Exterminator- A ... with High Probability.pdf - DSpace at CUSAT ...
Exterminator- A ... with High Probability.pdf - DSpace at CUSAT ...
Exterminator- A ... with High Probability.pdf - DSpace at CUSAT ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Extermin<strong>at</strong>or</strong><br />
canaries into the dangled object triggers a cascade of errors th<strong>at</strong> corrupt large segments of<br />
the heap. In these cases, the corruption destroys the inform<strong>at</strong>ion <strong>Extermin<strong>at</strong>or</strong> requires to<br />
isol<strong>at</strong>e the error.<br />
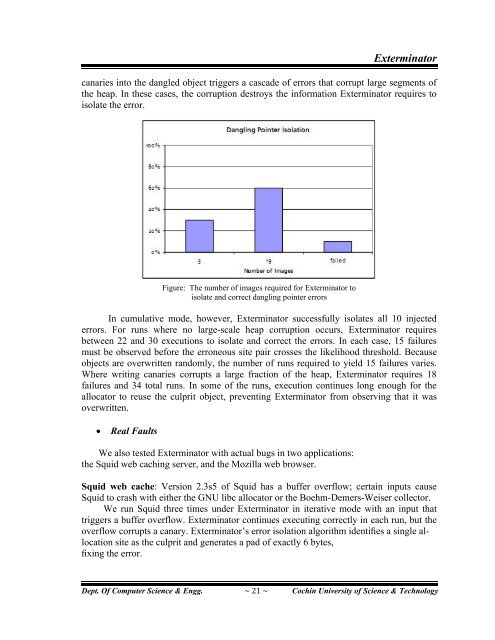
Figure: The number of images required for <strong>Extermin<strong>at</strong>or</strong> to<br />
isol<strong>at</strong>e and correct dangling pointer errors<br />
In cumul<strong>at</strong>ive mode, however, <strong>Extermin<strong>at</strong>or</strong> successfully isol<strong>at</strong>es all 10 injected<br />
errors. For runs where no large-scale heap corruption occurs, <strong>Extermin<strong>at</strong>or</strong> requires<br />
between 22 and 30 executions to isol<strong>at</strong>e and correct the errors. In each case, 15 failures<br />
must be observed before the erroneous site pair crosses the likelihood threshold. Because<br />
objects are overwritten randomly, the number of runs required to yield 15 failures varies.<br />
Where writing canaries corrupts a large fraction of the heap, <strong>Extermin<strong>at</strong>or</strong> requires 18<br />
failures and 34 total runs. In some of the runs, execution continues long enough for the<br />
alloc<strong>at</strong>or to reuse the culprit object, preventing <strong>Extermin<strong>at</strong>or</strong> from observing th<strong>at</strong> it was<br />
overwritten.<br />
Real Faults<br />
We also tested <strong>Extermin<strong>at</strong>or</strong> <strong>with</strong> actual bugs in two applic<strong>at</strong>ions:<br />
the Squid web caching server, and the Mozilla web browser.<br />
Squid web cache: Version 2.3s5 of Squid has a buffer overflow; certain inputs cause<br />
Squid to crash <strong>with</strong> either the GNU libc alloc<strong>at</strong>or or the Boehm-Demers-Weiser collector.<br />
We run Squid three times under <strong>Extermin<strong>at</strong>or</strong> in iter<strong>at</strong>ive mode <strong>with</strong> an input th<strong>at</strong><br />
triggers a buffer overflow. <strong>Extermin<strong>at</strong>or</strong> continues executing correctly in each run, but the<br />
overflow corrupts a canary. <strong>Extermin<strong>at</strong>or</strong>’s error isol<strong>at</strong>ion algorithm identifies a single alloc<strong>at</strong>ion<br />
site as the culprit and gener<strong>at</strong>es a pad of exactly 6 bytes,<br />
fixing the error.<br />
Dept. Of Computer Science & Engg. ~ 21 ~ Cochin University of Science & Technology