System Watcher - Kaspersky Lab
System Watcher - Kaspersky Lab
System Watcher - Kaspersky Lab
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Kaspersky</strong> Anti-Virus 2012<br />
heuristic analysis. If suspicious activity is detected, <strong>System</strong> <strong>Watcher</strong> prompts the user for action<br />
regardless of the operation mode.<br />
Upon detection of a new virus or new modification of already known malware the application does<br />
not update the entire <strong>System</strong> <strong>Watcher</strong> component, but simply adds a new template to the<br />
database of heuristics and updates it together with the <strong>Kaspersky</strong> <strong>Lab</strong> databases.<br />
To select the action that the component should perform if an application's activity matches a<br />
pattern of dangerous activity, perform the following actions:<br />
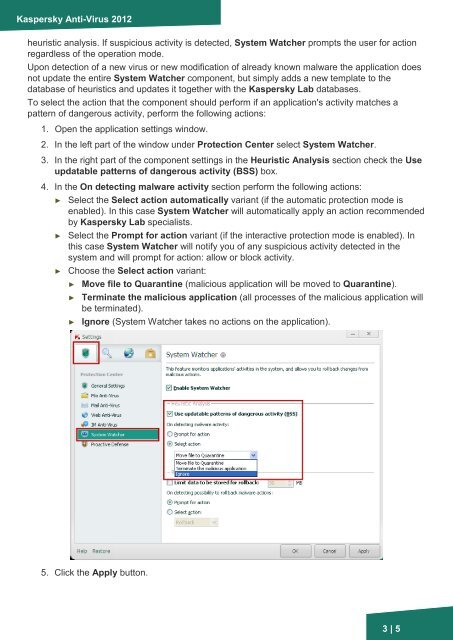
1. Open the application settings window.<br />
2. In the left part of the window under Protection Center select <strong>System</strong> <strong>Watcher</strong>.<br />
3. In the right part of the component settings in the Heuristic Analysis section check the Use<br />
updatable patterns of dangerous activity (BSS) box.<br />
4. In the On detecting malware activity section perform the following actions:<br />
► Select the Select action automatically variant (if the automatic protection mode is<br />
enabled). In this case <strong>System</strong> <strong>Watcher</strong> will automatically apply an action recommended<br />
by <strong>Kaspersky</strong> <strong>Lab</strong> specialists.<br />
► Select the Prompt for action variant (if the interactive protection mode is enabled). In<br />
this case <strong>System</strong> <strong>Watcher</strong> will notify you of any suspicious activity detected in the<br />
system and will prompt for action: allow or block activity.<br />
► Choose the Select action variant:<br />
► Move file to Quarantine (malicious application will be moved to Quarantine).<br />
► Terminate the malicious application (all processes of the malicious application will<br />
be terminated).<br />
► Ignore (<strong>System</strong> <strong>Watcher</strong> takes no actions on the application).<br />
5. Click the Apply button.<br />
3 | 5