Architecture and Best Practices - Recommendations for PI ... - OSIsoft
Architecture and Best Practices - Recommendations for PI ... - OSIsoft
Architecture and Best Practices - Recommendations for PI ... - OSIsoft
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
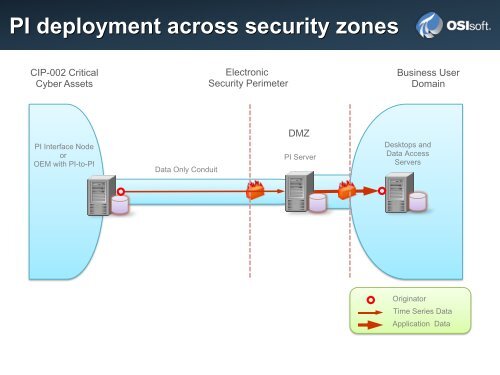
<strong>PI</strong> deployment across security zones<br />
CIP-002 Critical<br />
Cyber Assets<br />
<strong>PI</strong> Interface Node<br />
or<br />
OEM with <strong>PI</strong>-to-<strong>PI</strong><br />
Data Only Conduit<br />
Electronic<br />
Security Perimeter<br />
DMZ<br />
<strong>PI</strong> Server<br />
Business User<br />
Domain<br />
Desktops <strong>and</strong><br />
Data Access<br />
Servers<br />
Originator<br />
Time Series Data<br />
Application Data