Architecture and Best Practices - Recommendations for PI ... - OSIsoft
Architecture and Best Practices - Recommendations for PI ... - OSIsoft
Architecture and Best Practices - Recommendations for PI ... - OSIsoft
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
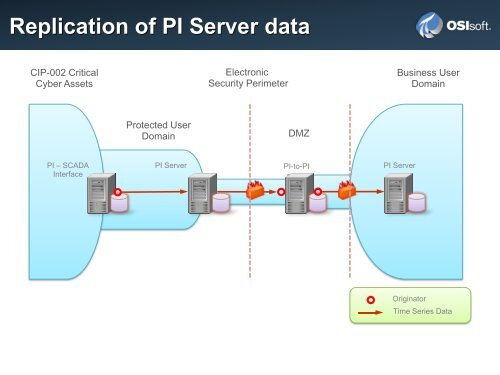
Replication of <strong>PI</strong> Server data<br />
CIP-002 Critical<br />
Cyber Assets<br />
<strong>PI</strong> – SCADA<br />
Interface<br />
Protected User<br />
Domain<br />
<strong>PI</strong> Server<br />
Electronic<br />
Security Perimeter<br />
DMZ<br />
<strong>PI</strong>-to-<strong>PI</strong><br />
Business User<br />
Domain<br />
<strong>PI</strong> Server<br />
Originator<br />
Time Series Data