PCI-DSS Compliance Checklist - WhatsUp Gold
PCI-DSS Compliance Checklist - WhatsUp Gold
PCI-DSS Compliance Checklist - WhatsUp Gold
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
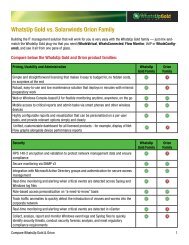
<strong>PCI</strong>-<strong>DSS</strong> <strong>Compliance</strong> <strong>Checklist</strong><br />
Meet Requirements with the <strong>WhatsUp</strong> <strong>Gold</strong><br />
Continuous <strong>Compliance</strong> Solution<br />
<strong>PCI</strong>-<strong>DSS</strong> Requirement<br />
1.1.1 A formal process for approving and testing<br />
all external network connections and changes to<br />
the firewall and router configurations<br />
1.1.6 Review firewall and router rule sets at<br />
least every six months<br />
<strong>WhatsUp</strong> <strong>Gold</strong> Solution<br />
<strong>WhatsUp</strong> <strong>Gold</strong> Layer 2/3 discovery and mapping identifies all<br />
network connections to servers holding cardholder data, for both<br />
wired and wireless.<br />
WhatsConfigured provides complete configuration management<br />
for your firewalls and routers, including:<br />
• Automatic tracking of all configuration changes<br />
• Real-time alerts of on any configuration changes,<br />
misconfigurations and failures to internal policies<br />
• Reports comparing archived authorized configurations with<br />
running configuration<br />
1.1.2 Current network diagram with all<br />
connections to cardholder data, including any<br />
wireless networks<br />
1.1.5 Documentation and business justification<br />
for use of all services, protocols, and ports<br />
allowed, including documentation of security<br />
features implemented for those protocols<br />
considered to be insecure<br />
1.3.3 Do not allow any direct routes inbound or<br />
outbound for traffic between the Internet and the<br />
cardholder data environment<br />
2.1 Always change vendor-supplied defaults<br />
before installing a system on the network (for<br />
example, include passwords, simple network<br />
management protocol (SNMP) community<br />
strings, and elimination of unnecessary accounts)<br />
2.2 Develop configuration standards for all<br />
system components. Assure that these standards<br />
address all known security vulnerabilities and<br />
are consistent with industry-accepted system<br />
hardening standards.<br />
<strong>WhatsUp</strong> <strong>Gold</strong> automatically generates a complete Layer 2/3<br />
topology map of your entire infrastructure to show all connections<br />
to cardholder data. Layer 2/3 maps include:<br />
• Physical port-to-port and IP connectivity<br />
• At-a-glance maps for your wireless network<br />
<strong>WhatsUp</strong> <strong>Gold</strong> automatically collects and documents<br />
comprehensive inventory information including:<br />
• Bridge and switch port configurations<br />
• A list of configured protocols on each network device<br />
<strong>WhatsUp</strong> <strong>Gold</strong> Layer 2/3 discovery and mapping validates that<br />
there is no direct connection between the Internet and any system<br />
in the cardholder data environment.<br />
Flow Monitor issues real-time alerts when a group of IP addresses<br />
in the cardholder data environment are in communication with the<br />
Internet.<br />
WhatsConfigured automatically schedules and executes password<br />
changes across one or more devices on your network.<br />
WhatsConfigured automates updating configuration changes<br />
across multiple devices when security vulnerabilities warrant it --<br />
through on-demand or scheduled management tasks.<br />
<strong>PCI</strong>-<strong>DSS</strong> <strong>Compliance</strong> <strong>Checklist</strong> 1
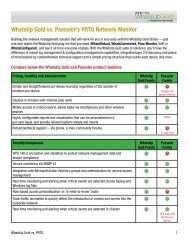
<strong>PCI</strong>-<strong>DSS</strong> Requirement<br />
5.1.1 Ensure that all antivirus programs are<br />
capable of detecting, removing, and protecting<br />
against all known types of malicious software<br />
5.2 Ensure that all antivirus mechanisms<br />
are current, actively running, and capable of<br />
generating audit logs<br />
6.1 Ensure that all system components and<br />
software have the latest vendor-supplied security<br />
patches installed. Install critical security patches<br />
within one month of release.<br />
8.5.1 Control addition, deletion, and modification<br />
of user IDs, credentials, and other identifier<br />
objects<br />
10.2 Implement automated audit trails for all<br />
system components to reconstruct the following<br />
events:<br />
• 10.2.1 All individual user accesses to<br />
cardholder data<br />
<strong>WhatsUp</strong> <strong>Gold</strong> Solution<br />
<strong>WhatsUp</strong> <strong>Gold</strong> Layer 2/3 discovery and inventory generates<br />
a detailed report of all installed software and patch levels on<br />
network and server devices.<br />
<strong>WhatsUp</strong> <strong>Gold</strong> validates that anti-virus software is running, and<br />
generates a report comparing system uptime vs. anti-virus uptime<br />
to identify any periods of exposure.<br />
<strong>WhatsUp</strong> <strong>Gold</strong> automatically discovers all network devices,<br />
servers and applications across your network.<br />
<strong>WhatsUp</strong> <strong>Gold</strong> generates comprehensive inventory reports of all<br />
IT assets deployed including vendor, model number, OS, patch<br />
level, modules, etc.<br />
The Log Management Suite continuously monitors Active<br />
Directory Windows events in real-time and alerts when changes<br />
occur.<br />
The Log Management Suite automatically collects, archives and<br />
securely stores complete audit trails of all log data across your<br />
systems including key events such as logon failures and object<br />
access attempts.<br />
• 10.2.2 All actions taken by any individual with<br />
root or administrative privileges<br />
• 10.2.3 Access to all audit trails<br />
• 10.2.4 Invalid logical access attempts<br />
• 10.2.5 Use of identification and authentication<br />
mechanisms<br />
• 10.2.6 Initialization of the audit logs<br />
• 10.2.7 Creation and deletion of system-level<br />
objects<br />
10.3 Record at least the following audit trail<br />
entries for all system components for each<br />
event:<br />
The Log Management Suite displays all log entries with type of<br />
event, date and timestamp, and more.<br />
• 10.3.1 User identification<br />
• 10.3.2 Type of event<br />
• 10.3.3 Date and time<br />
• 10.3.4 Success or failure indication<br />
• 10.3.5 Origination of event<br />
• 10.3.6 Identity or name of affected data,<br />
system component, or resource<br />
<strong>PCI</strong>-<strong>DSS</strong> <strong>Compliance</strong> <strong>Checklist</strong> 2
<strong>PCI</strong>-<strong>DSS</strong> Requirement<br />
10.5.2 Protect audit trail files from unauthorized<br />
modifications.<br />
10.5.3 Promptly back up audit trail files to a<br />
centralized log server or media that is difficult to<br />
alter.<br />
<strong>WhatsUp</strong> <strong>Gold</strong> Solution<br />
The Log Management Suite employs cryptographic hashing<br />
to protect the integrity of your archived log data by preventing<br />
tampering and modification.<br />
10.5.5 Use file-integrity monitoring and change<br />
detection software on logs to ensure that existing<br />
log data cannot be changed without generating<br />
alerts.<br />
11.5 Deploy file-integrity monitoring software<br />
to alert personnel to unauthorized modification<br />
of critical system files, configuration files, or<br />
content files, and configure the software to<br />
perform critical file comparisons at least weekly.<br />
10.6 Review logs for all system components<br />
at least daily. Log reviews must include<br />
those servers that perform security functions<br />
like intrusion detection system (IDS) and<br />
authentication, authorization, and accounting<br />
protocol (AAA) servers (for example, RADIUS).<br />
10.7 Retain audit trail history for at least<br />
one year, with a minimum of three months<br />
immediately available for analysis (for example,<br />
online, archived, or restorable from back-up).<br />
The Log Management Suite provides real-time monitoring,<br />
reporting and alerting on Object Deletions, Object Access<br />
Attempts, etc.<br />
The Log Management Suite automatically alerts on file, folder<br />
and object access or permission changes.<br />
WhatsConfigured automatically generates alerts on configuration<br />
file changes.<br />
The Log Management Suite provides views and allows mining<br />
log data across all servers and workstations from one console—<br />
without needing to spot-check log files for security events,<br />
since LMS pairs common security event identifiers with friendly<br />
descriptions.<br />
The Log Management Suite provides multi-year log storage/<br />
archiving keeping your log data for as long as the IT compliance<br />
regulation dictates.<br />
For more information on <strong>WhatsUp</strong> <strong>Gold</strong>, please visit:<br />
http://www.whatsupgold.com/products/whatsup-gold-core/<br />
Try it free today for 30 days:<br />
http://www.whatsupgold.com/products/download/<br />
www.whatsupgold.com<br />
Copyright © 2012, Ipswitch, Inc. All rights reserved. <strong>WhatsUp</strong> is a registered trademark and Ipswitch is<br />
a trademark of Ipswitch, Inc. Other products or company names are or may be trademarks or registered<br />
trademarks and are the property of their respective holders.