CCSDS File Delivery Protocol (CFDP)âPart 1: Introduction and ...
CCSDS File Delivery Protocol (CFDP)âPart 1: Introduction and ...
CCSDS File Delivery Protocol (CFDP)âPart 1: Introduction and ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>CCSDS</strong> REPORT CONCERNING THE <strong>CCSDS</strong> FILE DELIVERY PROTOCOL (<strong>CFDP</strong>)<br />
Proximity-1<br />
Proximity-1<br />
<strong>CCSDS</strong> AOS<br />
VCDU Service<br />
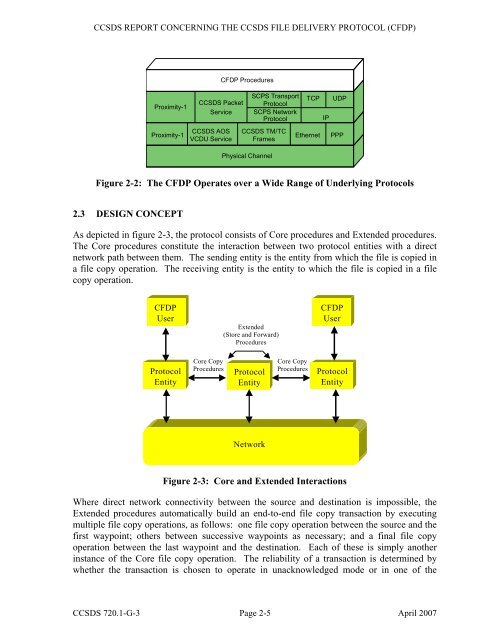
<strong>CFDP</strong> Procedures<br />
<strong>CCSDS</strong> Packet<br />
Service<br />
<strong>CCSDS</strong> TM/TC<br />
Frames<br />
Physical Channel<br />
SCPS Transport<br />
<strong>Protocol</strong><br />
SCPS Network<br />
<strong>Protocol</strong><br />
TCP<br />
Ethernet<br />
IP<br />
UDP<br />
PPP<br />
Figure 2-2: The <strong>CFDP</strong> Operates over a Wide Range of Underlying <strong>Protocol</strong>s<br />
2.3 DESIGN CONCEPT<br />
As depicted in figure 2-3, the protocol consists of Core procedures <strong>and</strong> Extended procedures.<br />
The Core procedures constitute the interaction between two protocol entities with a direct<br />
network path between them. The sending entity is the entity from which the file is copied in<br />
a file copy operation. The receiving entity is the entity to which the file is copied in a file<br />
copy operation.<br />
<strong>CFDP</strong><br />
User<br />
Extended<br />
(Store <strong>and</strong> Forward)<br />
Procedures<br />
<strong>CFDP</strong><br />
User<br />
<strong>Protocol</strong><br />
Entity<br />
Core Copy<br />
Procedures<br />
<strong>Protocol</strong><br />
Entity<br />
Core Copy<br />
Procedures<br />
<strong>Protocol</strong><br />
Entity<br />
Network<br />
Figure 2-3: Core <strong>and</strong> Extended Interactions<br />
Where direct network connectivity between the source <strong>and</strong> destination is impossible, the<br />
Extended procedures automatically build an end-to-end file copy transaction by executing<br />
multiple file copy operations, as follows: one file copy operation between the source <strong>and</strong> the<br />
first waypoint; others between successive waypoints as necessary; <strong>and</strong> a final file copy<br />
operation between the last waypoint <strong>and</strong> the destination. Each of these is simply another<br />
instance of the Core file copy operation. The reliability of a transaction is determined by<br />
whether the transaction is chosen to operate in unacknowledged mode or in one of the<br />
<strong>CCSDS</strong> 720.1-G-3 Page 2-5 April 2007