D.3.3 ALGORITHMS FOR INCREMENTAL ... - SecureChange
D.3.3 ALGORITHMS FOR INCREMENTAL ... - SecureChange
D.3.3 ALGORITHMS FOR INCREMENTAL ... - SecureChange
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Tactical<br />
Monitor air<br />
R<br />
controller<br />
traffic<br />
Observe air<br />
situation display<br />
Surveillance<br />
Flight data<br />
data<br />
De<br />
Manage<br />
Surveillance<br />
surveillance<br />
data<br />
data<br />
+<br />
AND<br />
Availability of<br />
Manage radar Gather aircraft<br />
radar signal<br />
signal<br />
position<br />
Run fault<br />
De<br />
tolerant<br />
MRT<br />
RDPS crashes<br />
[possible]<br />
Failure in<br />
Unreliable<br />
Component<br />
provisioning<br />
RDPS<br />
failure<br />
of surveillance<br />
Failure of A/C data<br />
tracking [possible]<br />
[likely]<br />
Loss of radar<br />
signal in MRT<br />
Run fault<br />
tolerant MRT<br />
minor<br />
Availability of<br />
surveillance<br />
data<br />
De<br />
FDPS<br />
RDPS<br />
Radar<br />
Insufficient<br />
radar<br />
maintenance<br />
Radar<br />
(a)<br />
(b)<br />
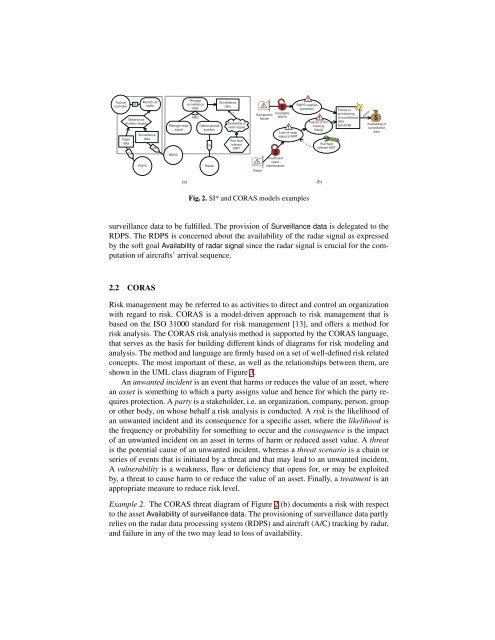
Fig. 2. SI* and CORAS models examples<br />
surveillance data to be fulfilled. The provision of Surveillance data is delegated to the<br />
RDPS. The RDPS is concerned about the availability of the radar signal as expressed<br />
by the soft goal Availability of radar signal since the radar signal is crucial for the computation<br />
of aircrafts’ arrival sequence.<br />
2.2 CORAS<br />
Risk management may be referred to as activities to direct and control an organization<br />
with regard to risk. CORAS is a model-driven approach to risk management that is<br />
based on the ISO 31000 standard for risk management [13], and offers a method for<br />
risk analysis. The CORAS risk analysis method is supported by the CORAS language,<br />
that serves as the basis for building different kinds of diagrams for risk modeling and<br />
analysis. The method and language are firmly based on a set of well-defined risk related<br />
concepts. The most important of these, as well as the relationships between them, are<br />
shown in the UML class diagram of Figure 3.<br />
An unwanted incident is an event that harms or reduces the value of an asset, where<br />
an asset is something to which a party assigns value and hence for which the party requires<br />
protection. A party is a stakeholder, i.e. an organization, company, person, group<br />
or other body, on whose behalf a risk analysis is conducted. A risk is the likelihood of<br />
an unwanted incident and its consequence for a specific asset, where the likelihood is<br />
the frequency or probability for something to occur and the consequence is the impact<br />
of an unwanted incident on an asset in terms of harm or reduced asset value. A threat<br />
is the potential cause of an unwanted incident, whereas a threat scenario is a chain or<br />
series of events that is initiated by a threat and that may lead to an unwanted incident.<br />
A vulnerability is a weakness, flaw or deficiency that opens for, or may be exploited<br />
by, a threat to cause harm to or reduce the value of an asset. Finally, a treatment is an<br />
appropriate measure to reduce risk level.<br />
Example 2. The CORAS threat diagram of Figure 2 (b) documents a risk with respect<br />
to the asset Availability of surveillance data. The provisioning of surveillance data partly<br />
relies on the radar data processing system (RDPS) and aircraft (A/C) tracking by radar,<br />
and failure in any of the two may lead to loss of availability.