Computers in Education - AS Level ICT WGS
Computers in Education - AS Level ICT WGS
Computers in Education - AS Level ICT WGS
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
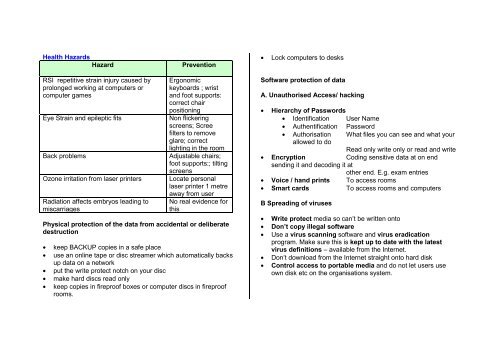
Health Hazards<br />
Hazard<br />
Prevention<br />
• Lock computers to desks<br />
RSI repetitive stra<strong>in</strong> <strong>in</strong>jury caused by<br />
prolonged work<strong>in</strong>g at computers or<br />
computer games<br />
Eye Stra<strong>in</strong> and epileptic fits<br />
Back problems<br />
Ozone irritation from laser pr<strong>in</strong>ters<br />
Radiation affects embryos lead<strong>in</strong>g to<br />
miscarriages<br />
Ergonomic<br />
keyboards ; wrist<br />
and foot supports:<br />
correct chair<br />
position<strong>in</strong>g<br />
Non flicker<strong>in</strong>g<br />
screens; Scree<br />
filters to remove<br />
glare; correct<br />
light<strong>in</strong>g <strong>in</strong> the room<br />
Adjustable chairs;<br />
foot supports:; tilt<strong>in</strong>g<br />
screens<br />
Locate personal<br />
laser pr<strong>in</strong>ter 1 metre<br />
away from user<br />
No real evidence for<br />
this<br />
Physical protection of the data from accidental or deliberate<br />
destruction<br />
• keep BACKUP copies <strong>in</strong> a safe place<br />
• use an onl<strong>in</strong>e tape or disc streamer which automatically backs<br />
up data on a network<br />
• put the write protect notch on your disc<br />
• make hard discs read only<br />
• keep copies <strong>in</strong> fireproof boxes or computer discs <strong>in</strong> fireproof<br />
rooms.<br />
Software protection of data<br />
A. Unauthorised Access/ hack<strong>in</strong>g<br />
• Hierarchy of Passwords<br />
• Identification User Name<br />
• Authentification Password<br />
• Authorisation What files you can see and what your<br />
allowed to do<br />
Read only write only or read and write<br />
• Encryption Cod<strong>in</strong>g sensitive data at on end<br />
send<strong>in</strong>g it and decod<strong>in</strong>g it at<br />
other end. E.g. exam entries<br />
• Voice / hand pr<strong>in</strong>ts To access rooms<br />
• Smart cards To access rooms and computers<br />
B Spread<strong>in</strong>g of viruses<br />
• Write protect media so can’t be written onto<br />
• Don’t copy illegal software<br />
• Use a virus scann<strong>in</strong>g software and virus eradication<br />
program. Make sure this is kept up to date with the latest<br />
virus def<strong>in</strong>itions – available from the Internet.<br />
• Don’t download from the Internet straight onto hard disk<br />
• Control access to portable media and do not let users use<br />
own disk etc on the organisations system.