ossim - AlienVault
ossim - AlienVault
ossim - AlienVault
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
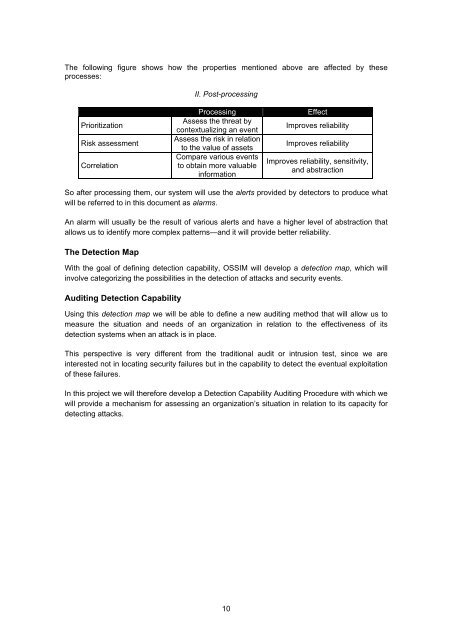
The following figure shows how the properties mentioned above are affected by these<br />
processes:<br />
II. Post-processing<br />
Prioritization<br />
Risk assessment<br />
Correlation<br />
Processing<br />
Assess the threat by<br />
contextualizing an event<br />
Assess the risk in relation<br />
to the value of assets<br />
Compare various events<br />
to obtain more valuable<br />
information<br />
Effect<br />
Improves reliability<br />
Improves reliability<br />
Improves reliability, sensitivity,<br />
and abstraction<br />
So after processing them, our system will use the alerts provided by detectors to produce what<br />
will be referred to in this document as alarms.<br />
An alarm will usually be the result of various alerts and have a higher level of abstraction that<br />
allows us to identify more complex patterns—and it will provide better reliability.<br />
The Detection Map<br />
With the goal of defining detection capability, OSSIM will develop a detection map, which will<br />
involve categorizing the possibilities in the detection of attacks and security events.<br />
Auditing Detection Capability<br />
Using this detection map we will be able to define a new auditing method that will allow us to<br />
measure the situation and needs of an organization in relation to the effectiveness of its<br />
detection systems when an attack is in place.<br />
This perspective is very different from the traditional audit or intrusion test, since we are<br />
interested not in locating security failures but in the capability to detect the eventual exploitation<br />
of these failures.<br />
In this project we will therefore develop a Detection Capability Auditing Procedure with which we<br />
will provide a mechanism for assessing an organization’s situation in relation to its capacity for<br />
detecting attacks.<br />
10