IJIES-2008 VOLUME 1 ISSUE 4 - Index of
IJIES-2008 VOLUME 1 ISSUE 4 - Index of
IJIES-2008 VOLUME 1 ISSUE 4 - Index of
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
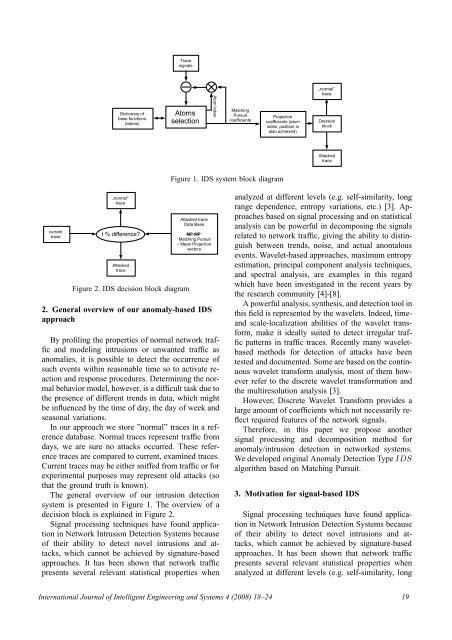
Figure 1. IDS system block diagramFigure 2. IDS decision block diagram2. General overview <strong>of</strong> our anomaly-based IDSapproachBy pr<strong>of</strong>iling the properties <strong>of</strong> normal network trafficand modeling intrusions or unwanted traffic asanomalies, it is possible to detect the occurrence <strong>of</strong>such events within reasonable time so to activate reactionand response procedures. Determining the normalbehavior model, however, is a difficult task due tothe presence <strong>of</strong> different trends in data, which mightbe influenced by the time <strong>of</strong> day, the day <strong>of</strong> week andseasonal variations.In our approach we store ”normal” traces in a referencedatabase. Normal traces represent traffic fromdays, we are sure no attacks occurred. These referencetraces are compared to current, examined traces.Current traces may be either sniffed from traffic or forexperimental purposes may represent old attacks (sothat the ground truth is known).The general overview <strong>of</strong> our intrusion detectionsystem is presented in Figure 1. The overview <strong>of</strong> adecision block is explained in Figure 2.Signal processing techniques have found applicationin Network Intrusion Detection Systems because<strong>of</strong> their ability to detect novel intrusions and attacks,which cannot be achieved by signature-basedapproaches. It has been shown that network trafficpresents several relevant statistical properties whenanalyzed at different levels (e.g. self-similarity, longrange dependence, entropy variations, etc.) [3]. Approachesbased on signal processing and on statisticalanalysis can be powerful in decomposing the signalsrelated to network traffic, giving the ability to distinguishbetween trends, noise, and actual anomalousevents. Wavelet-based approaches, maximum entropyestimation, principal component analysis techniques,and spectral analysis, are examples in this regardwhich have been investigated in the recent years bythe research community [4]-[8].A powerful analysis, synthesis, and detection tool inthis field is represented by the wavelets. Indeed, timeandscale-localization abilities <strong>of</strong> the wavelet transform,make it ideally suited to detect irregular trafficpatterns in traffic traces. Recently many waveletbasedmethods for detection <strong>of</strong> attacks have beentested and documented. Some are based on the continuouswavelet transform analysis, most <strong>of</strong> them howeverrefer to the discrete wavelet transformation andthe multiresolution analysis [3].However, Discrete Wavelet Transform provides alarge amount <strong>of</strong> coefficients which not necessarily reflectrequired features <strong>of</strong> the network signals.Therefore, in this paper we propose anothersignal processing and decomposition method foranomaly/intrusion detection in networked systems.We developed original Anomaly Detection Type IDSalgorithm based on Matching Pursuit.3. Motivation for signal-based IDSSignal processing techniques have found applicationin Network Intrusion Detection Systems because<strong>of</strong> their ability to detect novel intrusions and attacks,which cannot be achieved by signature-basedapproaches. It has been shown that network trafficpresents several relevant statistical properties whenanalyzed at different levels (e.g. self-similarity, longInternational Journal <strong>of</strong> Intelligent Engineering and Systems 4 (<strong>2008</strong>) 18–24 19