Automated vulnerability scanning and exploitation
Automated vulnerability scanning and exploitation - Index of
Automated vulnerability scanning and exploitation - Index of
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
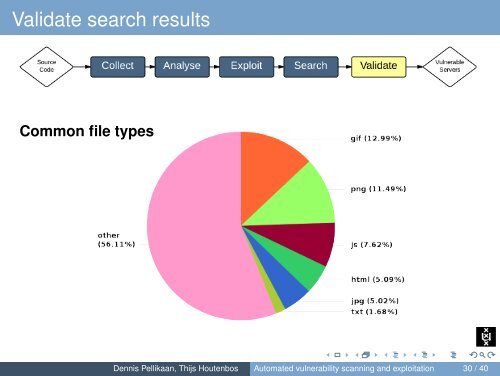
Validate search resultsCommon file typesDennis Pellikaan, Thijs Houtenbos <strong>Automated</strong> <strong>vulnerability</strong> <strong>scanning</strong> <strong>and</strong> <strong>exploitation</strong> 30 / 40