BATTLE OF SKM AND IUM
blackhat2015
blackhat2015
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
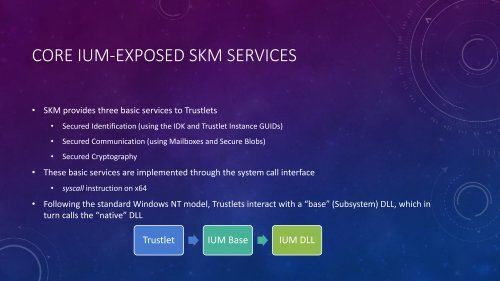
CORE <strong>IUM</strong>-EXPOSED <strong>SKM</strong> SERVICES<br />
• <strong>SKM</strong> provides three basic services to Trustlets<br />
• Secured Identification (using the IDK and Trustlet Instance GUIDs)<br />
• Secured Communication (using Mailboxes and Secure Blobs)<br />
• Secured Cryptography<br />
• These basic services are implemented through the system call interface<br />
• syscall instruction on x64<br />
• Following the standard Windows NT model, Trustlets interact with a “base” (Subsystem) DLL, which in<br />
turn calls the “native” DLL<br />
Trustlet <strong>IUM</strong> Base <strong>IUM</strong> DLL