dissection of a Cyber- Espionage attack
cct-w08_evolving-threats-dissection-of-a-cyber-espionage-attack
cct-w08_evolving-threats-dissection-of-a-cyber-espionage-attack
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
The <strong>attack</strong> strategy<br />
More patients to care about…<br />
To escalate the infection the <strong>attack</strong>er have used the OWA access <strong>of</strong> the stolen<br />
accounts to enumerate other potential victims for a new wave <strong>of</strong> targeted emails.<br />
#RSAC<br />
Also, one <strong>of</strong> the <strong>of</strong>ficers has access to internal Sharepoint service and participates<br />
to boards were specific internal meetings and projects are discussed.<br />
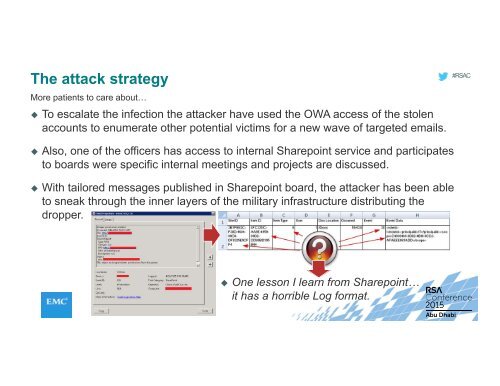
With tailored messages published in Sharepoint board, the <strong>attack</strong>er has been able<br />
to sneak through the inner layers <strong>of</strong> the military infrastructure distributing the<br />
dropper.<br />
One lesson I learn from Sharepoint…<br />
it has a horrible Log format.