dissection of a Cyber- Espionage attack
cct-w08_evolving-threats-dissection-of-a-cyber-espionage-attack
cct-w08_evolving-threats-dissection-of-a-cyber-espionage-attack
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
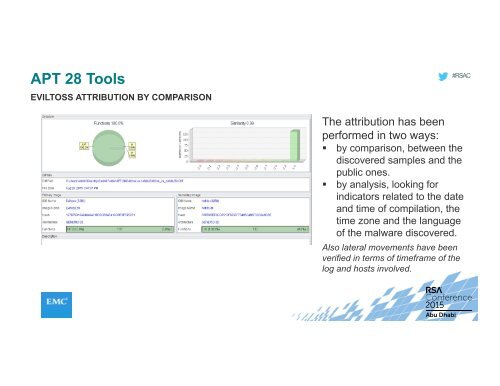
APT 28 Tools<br />
EVILTOSS ATTRIBUTION BY COMPARISON<br />
#RSAC<br />
The attribution has been<br />
performed in two ways:<br />
• by comparison, between the<br />
discovered samples and the<br />
public ones.<br />
• by analysis, looking for<br />
indicators related to the date<br />
and time <strong>of</strong> compilation, the<br />
time zone and the language<br />
<strong>of</strong> the malware discovered.<br />
Also lateral movements have been<br />
verified in terms <strong>of</strong> timeframe <strong>of</strong> the<br />
log and hosts involved.