DEFENSE SWITCHED NETWORK INFORMATION ASSURANCE ...
DEFENSE SWITCHED NETWORK INFORMATION ASSURANCE ...
DEFENSE SWITCHED NETWORK INFORMATION ASSURANCE ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
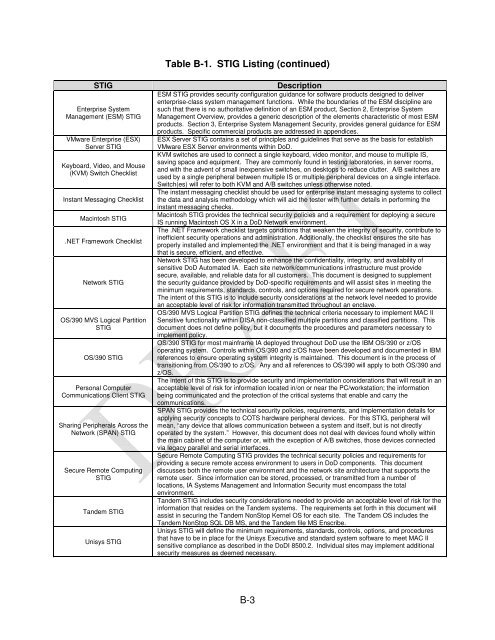
Table B-1. STIG Listing (continued)<br />
STIG Description<br />
Enterprise System<br />
Management (ESM) STIG<br />
VMware Enterprise (ESX)<br />
Server STIG<br />
Keyboard, Video, and Mouse<br />
(KVM) Switch Checklist<br />
Instant Messaging Checklist<br />
Macintosh STIG<br />
.NET Framework Checklist<br />
Network STIG<br />
OS/390 MVS Logical Partition<br />
STIG<br />
OS/390 STIG<br />
Personal Computer<br />
Communications Client STIG<br />
Sharing Peripherals Across the<br />
Network (SPAN) STIG<br />
Secure Remote Computing<br />
STIG<br />
Tandem STIG<br />
Unisys STIG<br />
ESM STIG provides security configuration guidance for software products designed to deliver<br />
enterprise-class system management functions. While the boundaries of the ESM discipline are<br />
such that there is no authoritative definition of an ESM product, Section 2, Enterprise System<br />
Management Overview, provides a generic description of the elements characteristic of most ESM<br />
products. Section 3, Enterprise System Management Security, provides general guidance for ESM<br />
products. Specific commercial products are addressed in appendices.<br />
ESX Server STIG contains a set of principles and guidelines that serve as the basis for establish<br />
VMware ESX Server environments within DoD.<br />
KVM switches are used to connect a single keyboard, video monitor, and mouse to multiple IS,<br />
saving space and equipment. They are commonly found in testing laboratories, in server rooms,<br />
and with the advent of small inexpensive switches, on desktops to reduce clutter. A/B switches are<br />
used by a single peripheral between multiple IS or multiple peripheral devices on a single interface.<br />
Switch(es) will refer to both KVM and A/B switches unless otherwise noted.<br />
The instant messaging checklist should be used for enterprise instant messaging systems to collect<br />
the data and analysis methodology which will aid the tester with further details in performing the<br />
instant messaging checks.<br />
Macintosh STIG provides the technical security policies and a requirement for deploying a secure<br />
IS running Macintosh OS X in a DoD Network environment.<br />
The .NET Framework checklist targets conditions that weaken the integrity of security, contribute to<br />
inefficient security operations and administration. Additionally, the checklist ensures the site has<br />
properly installed and implemented the .NET environment and that it is being managed in a way<br />
that is secure, efficient, and effective.<br />
Network STIG has been developed to enhance the confidentiality, integrity, and availability of<br />
sensitive DoD Automated IA. Each site network/communications infrastructure must provide<br />
secure, available, and reliable data for all customers. This document is designed to supplement<br />
the security guidance provided by DoD-specific requirements and will assist sites in meeting the<br />
minimum requirements, standards, controls, and options required for secure network operations.<br />
The intent of this STIG is to include security considerations at the network level needed to provide<br />
an acceptable level of risk for information transmitted throughout an enclave.<br />
OS/390 MVS Logical Partition STIG defines the technical criteria necessary to implement MAC II<br />
Sensitive functionality within DISA non-classified multiple partitions and classified partitions. This<br />
document does not define policy, but it documents the procedures and parameters necessary to<br />
implement policy.<br />
OS/390 STIG for most mainframe IA deployed throughout DoD use the IBM OS/390 or z/OS<br />
operating system. Controls within OS/390 and z/OS have been developed and documented in IBM<br />
references to ensure operating system integrity is maintained. This document is in the process of<br />
transitioning from OS/390 to z/OS. Any and all references to OS/390 will apply to both OS/390 and<br />
z/OS.<br />
The intent of this STIG is to provide security and implementation considerations that will result in an<br />
acceptable level of risk for information located in/on or near the PC/workstation; the information<br />
being communicated and the protection of the critical systems that enable and carry the<br />
communications.<br />
SPAN STIG provides the technical security policies, requirements, and implementation details for<br />
applying security concepts to COTS hardware peripheral devices. For this STIG, peripheral will<br />
mean, “any device that allows communication between a system and itself, but is not directly<br />
operated by the system.” However, this document does not deal with devices found wholly within<br />
the main cabinet of the computer or, with the exception of A/B switches, those devices connected<br />
via legacy parallel and serial interfaces.<br />
Secure Remote Computing STIG provides the technical security policies and requirements for<br />
providing a secure remote access environment to users in DoD components. This document<br />
discusses both the remote user environment and the network site architecture that supports the<br />
remote user. Since information can be stored, processed, or transmitted from a number of<br />
locations, IA Systems Management and Information Security must encompass the total<br />
environment.<br />
Tandem STIG includes security considerations needed to provide an acceptable level of risk for the<br />
information that resides on the Tandem systems. The requirements set forth in this document will<br />
assist in securing the Tandem NonStop Kernel OS for each site. The Tandem OS includes the<br />
Tandem NonStop SQL DB MS, and the Tandem file MS Enscribe.<br />
Unisys STIG will define the minimum requirements, standards, controls, options, and procedures<br />
that have to be in place for the Unisys Executive and standard system software to meet MAC II<br />
sensitive compliance as described in the DoDI 8500.2. Individual sites may implement additional<br />
security measures as deemed necessary.<br />
B-3