Cyber Security and IoT
Explaining why IoT (Internet of Things) devices must be secure by design. Published by CENSIS, the Innovation Centre for sensing, imaging and IoT. censis.org.uk
Explaining why IoT (Internet of Things) devices must be secure by design. Published by CENSIS, the Innovation Centre for sensing, imaging and IoT.
censis.org.uk
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Malware<br />
Malware is software designed to<br />
infiltrate <strong>and</strong> damage, control or<br />
disable electronics systems, including<br />
<strong>IoT</strong> devices. This can come in many<br />
forms including viruses, worms,<br />
trojans, ransomware, rootkit, spyware,<br />
adware <strong>and</strong> keyloggers. Malware can<br />
be used to form collectives of ‘bots’<br />
(Botnets) for performing automated<br />
malicious attacks (see sub-section<br />
below). According to cyber security<br />
solutions company McAfee, in the<br />
last year there has been a rise of<br />
203% in <strong>IoT</strong> malware in the form of<br />
‘cryptominers’ that hijack devices<br />
for mining cryptocurrency which<br />
is currently seen as a more lucrative<br />
business than ransomware.<br />
In December 2015, a regional<br />
electricity distribution company in<br />
Ukraine was attacked. The SCADA<br />
system controlling, <strong>and</strong> monitoring<br />
power distribution was targeted,<br />
enabling the attacker to switch off<br />
several substations. To obtain initial<br />
access to the company systems,<br />
malware was delivered by email. Two<br />
additional power companies were<br />
also attacked resulting in 225,000<br />
customers losing power for several<br />
hours.<br />
DDoS<br />
Distributed Denial-of-<br />
Service (DDoS)<br />
DDoS involves an attacker gaining<br />
access into a large number of<br />
distributed <strong>IoT</strong> devices. When access<br />
has been obtained, the attacker gains<br />
control of the devices (usually by<br />
installing malware), turning each of<br />
the devices into what is called a ‘Bot’<br />
or Zombie. The attacker can then<br />
instruct a group of ‘Bots’ to act as a<br />
‘Botnet’ to send requests to target<br />
internet addresses, such as cloud<br />
service providers. The significant<br />
amount of internet traffic generated<br />
reduces the capacity or prevents<br />
the target from servicing other valid<br />
users. This can also stop each of<br />
the <strong>IoT</strong> ‘Bot’ devices functioning as<br />
originally intended.<br />
An example of this is the 2016 Mirai<br />
Botnet. Several high-profile attacks<br />
happened that year, including an attack<br />
on Dyn, an internet infrastructure<br />
company. The attack prevented users<br />
from accessing social media accounts<br />
<strong>and</strong> other popular websites in the US<br />
<strong>and</strong> Europe. Mirai was one of the first<br />
pieces of software to enable largescale<br />
DDoS attacks. Mirai scans internet<br />
addresses to find devices, e.g., digital<br />
video recorders <strong>and</strong> CCTV cameras,<br />
with unsafe, easy to guess, default<br />
usernames <strong>and</strong> passwords; then it logsin<br />
<strong>and</strong> configures the devices to send<br />
data to an online target. With enough of<br />
these devices or ‘bots’ sending data, the<br />
online target is overloaded with requests<br />
from ‘bots’ <strong>and</strong> is unable to accept<br />
requests from legitimate users. More<br />
than 100,000 devices were thought<br />
to have been targeted, taken over, <strong>and</strong><br />
used in this attack.<br />
Man-in-middle attacks<br />
This describes where someone<br />
intercepts communications between<br />
<strong>IoT</strong> devices <strong>and</strong>/or other Internetconnected<br />
systems. The attacker<br />
poses as the original sender of the<br />
data. This allows eavesdropping <strong>and</strong><br />
the ability to send data to <strong>and</strong> receive<br />
data from the <strong>IoT</strong> devices undetected,<br />
enabling manipulation of the <strong>IoT</strong><br />
devices <strong>and</strong> connected systems.<br />
Cloud system <strong>and</strong> data<br />
centre attacks<br />
Cloud system <strong>and</strong> data centre attacks<br />
can be performed in several ways<br />
by targeting parts of the system<br />
architecture. This may include<br />
attacking the web server function<br />
used to provide <strong>IoT</strong> dashboards<br />
(displaying data from the <strong>IoT</strong> devices<br />
or providing centralised control of <strong>IoT</strong><br />
devices), or attacking the database<br />
systems used to store gathered <strong>IoT</strong><br />
data. As many <strong>IoT</strong> devices rely on a<br />
cloud system to function correctly,<br />
as part of the overall <strong>IoT</strong> solution, this<br />
may render the <strong>IoT</strong> incapacitated or<br />
severely limit the ability for the <strong>IoT</strong><br />
devices to function.<br />
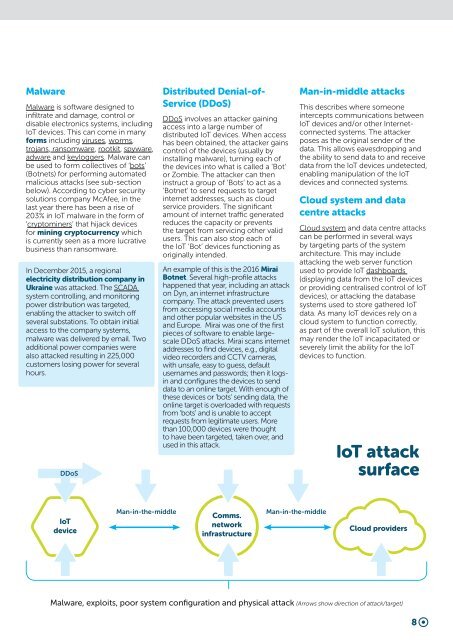
<strong>IoT</strong> attack<br />
surface<br />
<strong>IoT</strong><br />
device<br />
Man-in-the-middle<br />
Comms.<br />
network<br />
infrastructure<br />
Man-in-the-middle<br />
Cloud providers<br />
Malware, exploits, poor system configuration <strong>and</strong> physical attack (Arrows show direction of attack/target)<br />
8