NC May-Jun 2022
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
NETWORKcomputing<br />
I N F O R M A T I O N A N D C O M M U N I C A T I O N S – N E T W O R K E D www.networkcomputing.co.uk<br />
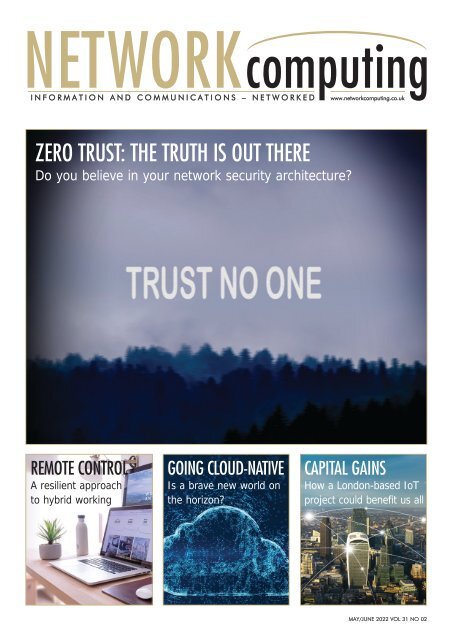
ZERO TRUST: THE TRUTH IS OUT THERE<br />
Do you believe in your network security architecture?<br />
REMOTE CONTROL<br />
A resilient approach<br />
to hybrid working<br />
GOING CLOUD-NATIVE<br />
Is a brave new world on<br />
the horizon?<br />
CAPITAL GAINS<br />
How a London-based IoT<br />
project could benefit us all<br />
MAY/JUNE <strong>2022</strong> VOL 31 NO 02
COMMENT<br />
COMMENT<br />
TRUST ISSUES<br />
Working from home kept so many of us safe during the Covid-19 pandemic - but<br />
can the same be said for our networks? With the pandemic receding and hybrid<br />
working here to stay it's starting to feel like the network perimeter is now a thing of<br />
the past. We have embraced the flexibility of remote working but with that comes an even<br />
greater need to ensure that employees aren't the weak link when it comes to keeping the<br />
network secure. "Even before the pandemic, the safeguarding of corporate networks was a<br />
high priority for IT teams," writes Rodolphe Harand at YesWeHack in his article on hybrid<br />
working in this issue. "Now, with the rise of hybrid working, IT team concerns have only<br />
amplified as more employees are using unsecured public Wi-Fi networks in places such as<br />
coffee shops, hotels and libraries."<br />
If so many of us are now moving away from legacy networks, both literally and metaphorically,<br />
then the onus of security has to come with us. "The truth is that legacy security solutions<br />
cannot support a zero trust network," according to Matthew Margetts at Smarter<br />
Technologies in his article on Zero Trust. "In the legacy model, security measures are reliant<br />
on a closed perimeter security model that assumes that all users and applications are coming<br />
from the same network location and entry points. This approach is no longer sufficient,<br />
which is why Zero Trust security is becoming the preferred network security architecture."<br />
With a Zero Trust security architecture we are all treated as outsiders to the network,<br />
regardless of our location. "Everyone now sees that the real need is not for users to access<br />
networks, but rather just to access the applications as though they are all cloud accessible.<br />
That's the Zero Trust-based future for us all," according to Kevin Peterson, Senior<br />
Cybersecurity Strategist at Xalient. "Most enterprises realise that it is time to enhance remote<br />
access strategies and eliminate sole reliance on perimeter-based protection, with employees<br />
instead connecting from a Zero Trust standpoint. However, most organisations will find that<br />
their Zero Trust journey is not an overnight accomplishment - particularly if they have legacy<br />
systems or mindsets that don't transition well to this model."<br />
For Paul German at Certes Networks a High Assurance SD-WAN framework is the ideal<br />
way to facilitate Zero Trust: "There are no constraints on network redesign; no barriers to the<br />
types of data or applications that can be migrated to the cloud, which ensures both operational<br />
agility and a consistent data security posture that can evolve throughout the Digital<br />
Transformation journey, from on premise, through hybrid, to the cloud." It's a move that Paul<br />
urges the UK Government to make in this issue. Can we trust them to do the right thing?<br />
REVIEWS:<br />
Dave Mitchell<br />
DEPUTY EDITOR: Mark Lyward<br />
(netcomputing@btc.co.uk)<br />
PRODUCTION: Abby Penn<br />
(abby.penn@btc.co.uk)<br />
DESIGN: Ian Collis<br />
(ian.collis@btc.co.uk<br />
SALES:<br />
David Bonner<br />
(david.bonner@btc.co.uk)<br />
Julie Cornish<br />
(julie.cornish@btc.co.uk)<br />
SUBSCRIPTIONS: Christina Willis<br />
(christina.willis@btc.co.uk)<br />
PUBLISHER: John Jageurs<br />
(john.jageurs@btc.co.uk)<br />
Published by Barrow & Thompkins<br />
Connexion Ltd (BTC)<br />
35 Station Square,<br />
Petts Wood, Kent, BR5 1LZ<br />
Tel: +44 (0)1689 616 000<br />
Fax: +44 (0)1689 82 66 22<br />
SUBSCRIPTIONS:<br />
UK £35/year, £60/two years,<br />
£80/three years;<br />
Europe:<br />
£48/year, £85/two years £127/three years;<br />
ROW:<br />
£62/year, £115/two years, £168/three years;<br />
Subscribers get SPECIAL OFFERS — see subscriptions<br />
advertisement; Single copies of<br />
Network Computing can be bought for £8;<br />
(including postage & packing).<br />
© <strong>2022</strong> Barrow & Thompkins<br />
Connexion Ltd.<br />
All rights reserved.<br />
No part of the magazine may be<br />
reproduced without prior consent, in<br />
writing, from the publisher.<br />
GET FUTURE COPIES FREE<br />
BY REGISTERING ONLINE AT<br />
WWW.NETWORKCOMPUTING.CO.UK/REGISTER<br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 03
CONTENTS<br />
CONTENTS<br />
M A Y / J U N E 2 0 2 2<br />
IoT IN THE PUBLIC SECTOR...19<br />
Tim Kidd at Hitachi Solutions shares his<br />
experience of working on a leading London<br />
IoT project, and Nick Sacke at Comms365<br />
explains how IoT can help overcome the<br />
challenges now facing local authorities<br />
ZERO TOLERA<strong>NC</strong>E...............12<br />
Our Zero Trust feature looks at how<br />
enterprises can no longer assume they have<br />
full control over closed networks, and<br />
explains why a Zero Trust architecture is the<br />
ideal way to mitigate a network breach<br />
COMMENT.....................................3<br />
Trust issues<br />
INDUSTRY NEWS.............................6<br />
The latest networking news<br />
ARTICLES<br />
BRIDGING THE TECHNOLOGY<br />
SKILLS GAP.......................................8<br />
By Ciara Campbell at Tenable<br />
THE TRUTH IS OUT THERE................12<br />
By Matthew Margetts at Smarter Technologies<br />
ZERO TRUST ARCHITECTURE: FIVE<br />
REASONS YOU NEED IT...................14<br />
By Adrian Taylor at A10 Networks<br />
IMPLEMENTING IOT TO ADDRESS<br />
COUNTY COU<strong>NC</strong>IL CHALLENGES...20<br />
By Nick Sacke at Comms365<br />
THE FUTURE OF CLOUD-NATIVE....22<br />
By Erez Yalon at Checkmarx<br />
GOVERNMENT CLOUD<br />
ON-RAMPING................................24<br />
By Paul German at Certes Networks<br />
THE DATA CENTRE IN <strong>2022</strong><br />
AND BEYOND.......................32<br />
The times they are a-changin’ for the data<br />
centre, according to Peter Miller at ETB<br />
Technologies<br />
GOING CLOUD-NATIVE.......22<br />
Our cloud feature this issue explains how<br />
to best ensure that your cloud-native<br />
solutions are secure and explores how to<br />
unleash your untapped data potential with<br />
a modern cloud strategy<br />
A RESILIENT APPROACH TO<br />
HYBRID WORKING..............34<br />
Hybrid working presents a number of<br />
security challenges for IT teams.<br />
Rodolphe Harand at YesWeHack looks at<br />
how to address them<br />
LEVERAGING THE DATA DELUGE...26<br />
By Laura Malins at Matillion<br />
STRENGTHENING THE UK’S<br />
CYBER RESILIE<strong>NC</strong>E..........................28<br />
By Mike Foster at VIPRE<br />
CASE STUDIES<br />
A SEAWORTHY SOLUTION..............16<br />
How Seajacks migrated its business-critical<br />
infrastructure with ServerChoice<br />
LEADING BETTER LIVES WITH IoT....19<br />
Tim Kidd at Hitachi Solutions shares his<br />
experience of working on a leading Internet of<br />
Things project in London<br />
PRODUCT REVIEW<br />
TREND NETWORKS LANTEK IV-S............9<br />
EXAGRID X COMMVAULT EX84.......10<br />
CLOUDCALL....................................17<br />
PERLE IOLAN SCG.............................18<br />
PROGRESS WHATSUP GOLD <strong>2022</strong>......27<br />
FLUKE NETWORKS FIBERLERT.........31<br />
04 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
INDUSTRY NEWS<br />
NEWSNEWS<br />
NEWS NEWS<br />
NEWS NEWS NEWS NEWS<br />
NEWS NEWS<br />
New Fluke HQ has the customer experience at heart<br />
Fluke has launched its new European Headquarters in<br />
Eindhoven, Netherlands, which includes a 400sqm<br />
customer experience centre. For the first time, customers will<br />
not only be able to see Fluke's range of world-class tools, but<br />
experience using them in a variety of real-world applications.<br />
The individual environments in which each of Fluke's tools are<br />
used have been reimagined in the heart of the building. From<br />
miniaturised electrical substations to small scale factories, a<br />
scene has been set for each.<br />
"The best way to offer training is to do so in a hands-on<br />
environment such as this. If customers are unable to attend in<br />
person, we can make demonstration videos to show the best of<br />
our equipments," said Fluke Strategic support and training<br />
manager, Eric van Riet. "It's working, our customers love it."<br />
The environments include a small factory set up, an Industrial<br />
Island complete with a motor driven pump pushing water in a<br />
closed-loop system, a traditional data centre, as well as a<br />
window into networking of the future with communications<br />
cabling channelled through our ceiling tile infrastructure. There<br />
is also a miniaturised high-voltage substation complete with<br />
intricate 3D printed scale models and a tesla coil to simulate<br />
partial discharge.<br />
Hybrid working shifts priorities for IT teams<br />
ManageEngine has unveiled the results of its new survey,<br />
"The State of ITSM Two Years Into the COVID-19<br />
Pandemic", following up on a similar survey conducted in<br />
2020 to understand the challenges the pandemic has caused<br />
for IT service teams. The latest findings indicate that<br />
organisations are now grappling with a new set of problems<br />
that were not previously deemed the top priorities.<br />
With three-fifths of the workforce now working in a hybrid<br />
mode, managing IT assets (46%) and communication and<br />
collaboration (41%) have emerged as the biggest challenges.<br />
Both jumped to the top spots, registering a positive difference<br />
of 11% and 7%, respectively, when compared to the 2020<br />
figures. The most significant shift in reported challenges was a<br />
drop from 36% to 22% for securing company and client data<br />
in a distributed network. This change is likely the result of the<br />
proactive efforts of IT teams to ensure remote working risks<br />
were minimised.<br />
"ITSM teams played a critical role in ensuring that business<br />
operations continued during the pandemic, from overseeing<br />
BYOD policies and the provision of mobile assets to<br />
implementing self-service features and chatbots, investing<br />
more in business continuity planning and offering IT service<br />
delivery and support," commented Kumaravel Ramakrishnan,<br />
evangelist at ManageEngine.<br />
A hardened approach to endpoint security<br />
VIPRE has introduced Vulnerability and Patch Management<br />
(Endpoint Hardening) to its Endpoint Security Cloud service.<br />
These two features work together to give IT admins and<br />
Managed Service Providers (MSPs) increased visibility into<br />
network and device vulnerabilities, and enables them to apply<br />
patches right from the intuitive management portal.<br />
With the addition of vulnerability and patch management<br />
VIPRE’s enhanced Endpoint Security Cloud give increased<br />
visibility to the risks posed by third-party applications within an<br />
organisation, while prioritising the weaknesses to address. It then<br />
delivers embedded patch management to close discovered<br />
vulnerabilities automatically while restricting other potential<br />
attacks with intrusion prevention, DNS Protection, and URL<br />
blockers. It also offers multi-layered protection, against file,<br />
application, and network layer attacks. Through powerful<br />
technologies such as signature-based detection, heuristic<br />
analysis, and behavioural analysis, VIPRE Endpoint Security<br />
Cloud proactively spots vulnerabilities, including zero-day threats.<br />
Changes ahead for Cyber Certified Professional scheme<br />
Responsibility for running the cyber security industry's Cyber<br />
Certified Professional scheme has transferred from the<br />
National Cyber Security Centre (<strong>NC</strong>SC) to the UK Cyber Security<br />
Council. As part of its oversight role, the Council will be<br />
reviewing the Cyber Certified Professional (CCP) scheme and<br />
launching a six-month pilot to inform new chartered standards.<br />
06 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
INDUSTRY NEWS<br />
The Council, which has been formed to act as the voice of<br />
the cyber security industry and has a key focus on creating<br />
aligned standards and qualifications for the sector, will now<br />
conduct a six-month review of the CCP scheme. As part of the<br />
review, the Council will be running a pilot scheme of new<br />
chartered standards for the industry. The Ministry of Defence,<br />
<strong>NC</strong>SC and Department for Work and Pensions will be<br />
participatingialong with existing qualification providers BCS,<br />
APMG and CIISec.<br />
KnowBe4 wins UK's Best Workplaces recognition<br />
KnowBe4 has been recognised as one of the 290 UK's Best<br />
Workplaces (<strong>2022</strong>) by Great Place to Work, the global<br />
authority on workplace culture. "We are so proud to be<br />
recognised as one of the UK's Best Workplaces this year," said<br />
Stu Sjouwerman, CEO, KnowBe4. "Company culture is<br />
something we strive to perfect every day by creating an<br />
environment where open communication, transparency and<br />
positive attitudes are valued."<br />
To determine the <strong>2022</strong> UK's Best Workplaces list, Great Place to<br />
Work performed rigorous evaluate hundreds of employee survey<br />
responses alongside Culture Audit submissions from leaders at<br />
each company. They then used these data insights to benchmark<br />
the effectiveness of companies' employee value propositions<br />
against the culture their employees actually experience. "This was<br />
the best onboarding experience ever! From the recruiting/interview<br />
process to onboarding and training, I felt so supported and<br />
welcomed. The company culture is amazing and they really do like<br />
to have fun. I love the transparency and the overall opportunities<br />
to continue to learn," said a KnowBe4 employee.<br />
Progressing Managed File Transfers with MOVEit <strong>2022</strong><br />
Progress has released its secure, automated Managed File<br />
Transfer software, Progress MOVEit <strong>2022</strong>, which can be<br />
deployed both on premise and in the cloud. Progress MOVEit<br />
is used by thousands of organisations worldwide and enables<br />
users to manage, view, secure and control all file transfer<br />
activity. The new release includes an add-in for Microsoft<br />
Outlook and advanced security and usability features.<br />
"With MOVEit <strong>2022</strong>, users can manage all of their sensitive<br />
data transfers between partners, customers, users and systems<br />
from a single pane of glass, giving them complete visibility and<br />
control over where data goes and ensuring the highest levels<br />
of security," said John Ainsworth, EVP Enterprise Application<br />
Experience Products, Progress.<br />
Talend Data Fabric enhancements boost data health<br />
Data integration and management vendor Talend, based in<br />
Maidenhead, has updated its namesake data fabric all-inone<br />
data management solution. By understanding data health<br />
by dataset groups, these new features, which are set to be<br />
available from <strong>Jun</strong>e, will help businesses analyse combined<br />
data quality metrics to evaluate data trust at macro and micro<br />
levels, across networks - including all datasets, customisable<br />
groups of datasets or individual datasets.<br />
Talend Trust Score, which was introduced by Talend in 2020,<br />
helps businesses assess the quality of their datasets. The 2021<br />
iteration added the ability to measure trust of data shred by<br />
APIs. With the new update Talend Trust Score can now provide<br />
a micro- or macro-level quality visualisation into datasets.<br />
Users can also see the impact of data interventions and detect<br />
how data quality has changed over time. In addition to Talend<br />
Trust Score updates the new update accelerates productivity<br />
with collaborative workflows that can serve as a conduit<br />
between users at different technical levels.<br />
Intel-based accelerators for new Supermicro solutions<br />
S<br />
uper Micro Computer, Inc. has launched a range of new<br />
systems that include two new Intel-based accelerators for<br />
demanding cloud gaming, media delivery, AI and ML<br />
workloads, enabling customers to deploy the latest<br />
acceleration technology from Intel and Intel Habana. The<br />
Habana LabsGaudi2 (above) excels at a range of workloads<br />
that include vision applications such as image classification,<br />
object detection, Natural Language Processing (NLP) models,<br />
and recommendation systems. The new AI Training server will<br />
be the first commercial implementation with the new Habana<br />
Gaudi2 (HL-225) in an 8U chassis. This server will accelerate<br />
AI training to new performance levels combined with dual 3rd<br />
Gen Intel Xeon Scalable processors and up to 8TB DRAM.<br />
NEWS NEWSNEWS<br />
NEWS<br />
NEWS NEWS NEWS NEWS NEWS<br />
NEWS<br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 07
OPINION: IT SKILLS<br />
BRIDGING THE TECHNOLOGY SKILLS GAP<br />
DOES DIVERSITY IN CYBSECURITY ACTUALLY MATTER? CIARA CAMPBELL, SENIOR SECURITY<br />
ENGINEER, TENABLE GIVES US HER TAKE<br />
The technology skills gap, particularly<br />
in cybersecurity, has been a<br />
recurring challenge for years. Harvey<br />
Nash Group suggests that there has been<br />
a shortfall of 10,000 people a year in the<br />
UK's cybersecurity talent pool. According<br />
to Microsoft, there are 2.5 million unfilled<br />
cybersecurity jobs worldwide. Can<br />
anything be done to overcome this<br />
shortfall?<br />
In short, yes. During the pandemic,<br />
technology became increasingly<br />
incorporated into our daily lives. The way<br />
we work has moved from physical offices<br />
to hybrid work environments and<br />
organisations just need to think a little<br />
more creatively about what they offer to<br />
their workforce.<br />
Companies should broaden their thinking<br />
when it comes to finding the right talent.<br />
Embrace running intern or graduate<br />
programs, and how best to support<br />
women and/or men returning to the<br />
workforce who might have taken time out<br />
for family or health reasons. Offer training<br />
and mentor programs that support new<br />
hires and existing employees to keep<br />
everyone at the top of their game. I myself<br />
started my career through intern and<br />
graduate programs.<br />
Security can be about prevention and<br />
detection but it doesn't just come down to<br />
those two aspects. There are many layers<br />
to security, which is what makes it such a<br />
fun industry to work in. Of course, it's not<br />
all a bed of roses. Sometimes, keeping up<br />
with all the technical knowledge can be<br />
hard and it's so vast. But that also presents<br />
an opportunity.<br />
POWERED BY DIVERSITY<br />
No matter if it's working in IT, cybersecurity,<br />
or any industry, it's really important for teams<br />
to have different inputs and ways of thinking.<br />
By having diversity, different ideas and<br />
perspectives are brought to the table that<br />
can lead to the creation of amazing<br />
innovation. It empowers us all to achieve<br />
greater creativity, to think outside the box,<br />
and drive alternative viewpoints that enables<br />
us to grow both individually and as a team.<br />
Diversity also makes the workplace far more<br />
enjoyable and a more interesting<br />
environment to work in. It makes a very<br />
boring work environment when everyone is<br />
the same - you need the diversity for different<br />
perspectives and opinions.<br />
When it comes to cyber talent, flexibility in<br />
location and adaptability to schedule<br />
changes is almost a requirement. Businesses<br />
that have embraced a remote working<br />
environment have been able to successfully<br />
widen their candidate pool considerably and<br />
found it advantageous in the battle for talent.<br />
When you break it down, a business is<br />
nothing more than a group of people, often<br />
organised by a common set of values and<br />
interests that carry forward a shared business<br />
mission. Even the smallest community (our<br />
friends, our families) are diverse by nature:<br />
the most obvious one being diversity of<br />
gender. That said, there will still be<br />
differences in opinions and contributions that<br />
each member brings to the table. For<br />
companies, and cybersecurity specifically, if<br />
everyone on the team thinks the same way,<br />
you've already lost the race with attackers.<br />
Only through increased inclusion and<br />
diversity-of race, gender, perspective and<br />
thought can we achieve greater creativity<br />
and innovation, think outside the box, and<br />
outmanoeuvre our adversaries.<br />
It's also important to recognise that no<br />
candidate is perfect, in terms of experience<br />
and expertise. One solution is for companies<br />
to hire people with less experience, or even an<br />
intern program, and spend time and money to<br />
train and upskill recruits. It's not just about new<br />
hires, but employers investing in their people<br />
through certifications and training that<br />
nurtures career longevity and retention.<br />
Thinking long term, the underrepresentation<br />
of diverse backgrounds in<br />
cybersecurity is linked to the broader<br />
problem of a lower rate enrolling in science,<br />
technology, engineering and mathematics<br />
(STEM) fields. Diversity breeds diversity. We<br />
need to foster relationships and show the<br />
next generation of the cyber workforce there<br />
are people like them in the industry. It sends<br />
a message that "you can do it too." <strong>NC</strong><br />
08 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
PRODUCT REVIEW<br />
TREND Networks<br />
LanTEK IV-S<br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
TREND Networks has an excellent<br />
reputation in the network cable<br />
certification world and its LanTEK IV-S<br />
takes this to the next level. Building on the<br />
successes of its well-respected LanTEK IV<br />
model, the IV-S boasts a faster v3.0 operating<br />
system, a dual-core CPU, double the system<br />
RAM and room to store up to 5,000 test<br />
results - twice that of its predecessor.<br />
This extra horsepower makes its mark as the<br />
IV-S can run a full certification test on Cat6A<br />
cabling in only 7 seconds, making it one of<br />
the fastest in the world. It also incorporates<br />
valuable future-proofing as it can certify<br />
Cat8.1 and Cat8.2 links up to 3,000MHz.<br />
The kit we tested includes LanTEK IV-S<br />
3000MHz display and IV-S remote handsets<br />
supplied in a rugged transport case. It also<br />
includes two power adapters, shoulder straps,<br />
Cat8 channel adapters and TREND's Cat8<br />
RJ45 VisiLINQ permanent link adapters.<br />
Installers working in noisy data centres will<br />
approve of the VisiLINQ adapters as these<br />
provide clear visual cues for link status and test<br />
results. Their integral LEDs turn blue to confirm<br />
a connection between the handsets, yellow for<br />
a marginal test pass and red for a test failure,<br />
while pressing on their collar activates a white<br />
torch mode - handy when working in the dingy<br />
depths of a rack cabinet. The adapters also<br />
incorporate field-replaceable RJ45 tips rated<br />
for at least 2,000 insertions.<br />
The handset's LCD touchscreen makes light<br />
work of configuration and with the aid of its<br />
quick start wizard, we easily created our first<br />
certification job. After providing a meaningful<br />
name, we added identifiers such as the<br />
building, floor, room and rack cabinet and<br />
assigned a sequence of tests.<br />
For each test, you select standards from the<br />
extensive list, choose link and cable types and<br />
pick a cable brand, which can be generic or<br />
manufacturer-specific (there's a big choice).<br />
We performed a range of certification tests on<br />
the lab's Cat6A cabling infrastructure and<br />
were mightily impressed with the levels of<br />
information presented. And yes, all full cable<br />
tests were completed in precisely 7 seconds.<br />
Tapping on a completed test in the screen<br />
brings up all the results which can be scrolled<br />
through and selected for more detail. Cable<br />
lengths are revealed, the wiremap screen<br />
shows connection issues along with the<br />
distance to detected faults, and you can use<br />
the live wiremap view to check consistency<br />
prior to running a full test.<br />
Below this onscreen are the results of all the<br />
certification tests you elected to run - there<br />
are far too many to list here but rest assured<br />
the LanTEK IV-S supports all the important<br />
ones. Tapping on each result brings up<br />
graphs or tables of the measurements and<br />
you can view all or selected cable pairs<br />
where appropriate, and swap between the<br />
main display and remote handsets.<br />
Integration with TREND's AnyWARE cloud<br />
portal allows project managers to work<br />
remotely with their field engineers and create<br />
pre-defined certification tests for direct<br />
download to the handset. It worked perfectly<br />
for us as after connecting our handset to the<br />
lab's wireless network - we synced it with our<br />
cloud account, pulled down jobs and<br />
uploaded test results.<br />
Choose a set of tests and the portal creates<br />
professional certification reports for<br />
presentation to customers. Another smart<br />
feature is that the handset runs the<br />
TeamViewer server component and we had<br />
no problems setting up sessions and<br />
controlling it remotely.<br />
The powerful LanTEK IV-S makes cable<br />
certification a breeze as it combines a<br />
wealth of standards-based tests with extreme<br />
ease of use. Performance is on the money,<br />
integration with AnyWARE accelerates<br />
project management and TREND's Sapphire<br />
Care Plans will significantly reduce the total<br />
cost of ownership. <strong>NC</strong><br />
Product: LanTEK IV-S<br />
Supplier: TREND Networks<br />
Web site: www.trend-networks.com<br />
Tel: +44 (0)1925 428 380<br />
Price: Model R163009 from £10,110<br />
exc VAT<br />
WWW.NETWORKCOMPUTING.CO.UK MAY/JUNE 09<br />
NETWORKcomputing<br />
@<strong>NC</strong>MagAndAwards
PRODUCT REVIEW<br />
ExaGrid x<br />
Commvault =<br />
Enhanced Storage<br />
Economics<br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
ExaGrid stands tall in the enterprise data<br />
backup and disaster recovery market as<br />
its Tiered Backup Storage family of EX<br />
appliances deliver a unique data protection<br />
solution with a sharp focus on performance<br />
and reduced storage costs. Even more<br />
compelling is ExaGrid's data deduplication<br />
technology, as its patented Landing Zone with<br />
Adaptive Deduplication solves the performance<br />
challenges inherent in traditional inline data<br />
reduction techniques. That's not to say that<br />
ExaGrid wants to replace your existing data<br />
protection solution. Far from it, as its Tiered<br />
Backup Storage solution works hand in glove<br />
with over 25 leading enterprise backup<br />
applications where it can enhance their<br />
capabilities immensely.<br />
Commvault fans will approve of this approach<br />
as they can retain their existing data protection<br />
infrastructure and integrate ExaGrid into it to<br />
provide the backend storage. More importantly,<br />
they can continue to enjoy the clear benefits of<br />
Commvault's deduplication engine and allow<br />
ExaGrid to deduplicate backup data further on<br />
its target storage, with combined reduction<br />
ratios improved up to an impressive 20:1.<br />
These numbers are very compelling, as<br />
combining ExaGrid and Commvault into one<br />
backup strategy will reduce its storage footprint<br />
by as much as 300%. Extrapolate this over a<br />
number of years and it's clear that substantial<br />
savings can be made.<br />
A key feature of ExaGrid's appliances is their<br />
Landing Zone, where data from the Commvault<br />
backup application is written directly to a disk<br />
cache. As backups complete, the data in the<br />
Landing Zone is 'tiered' and written to a separate<br />
long-term retention repository where it is<br />
compressed and deduplicated.<br />
This has no impact on performance, and as<br />
copies of the most recent backups are retained<br />
in the Landing Zone, restore operations are<br />
much faster as data doesn't need rehydration<br />
and decompression. Data security and<br />
protection against ransomware attacks are<br />
further enhanced as while the Landing Zone is<br />
network facing, the repository has a tiered air<br />
gap between the network-facing Landing Zone<br />
and the non-network-facing retention repository<br />
which is only visible to ExaGrid. From the<br />
Commvault administrator's perspective, there is<br />
very little they need to change as ExaGrid<br />
storage is presented as CIFS/NFS shares, so all<br />
they need do is declare them to Commvault<br />
storage policies as backup destinations. They<br />
can leave the Commvault MediaAgent inline<br />
deduplication and data integrity validation<br />
services enabled as well.<br />
Keeping Commvault's deduplication in play<br />
brings extra rewards by reducing space<br />
requirements for the ExaGrid Landing Zone, as<br />
it is already receiving deduplicated data.<br />
Conversely, disabling Commvault's<br />
deduplication and only using ExaGrid's services<br />
means the MediaAgents can be installed on less<br />
powerful host systems.<br />
This solution clearly works very well and<br />
demonstrates significant storage savings. For<br />
testing, ExaGrid used a 15.5TB dataset<br />
comprising system data, SQL Server databases<br />
and multiple VMware VMs. ExaGrid's mighty<br />
EX84 appliance was called up to provide the<br />
backend storage plus an 84TB landing zone<br />
which was presented to Commvault as a<br />
CIFS/SMB network share. A 15-day simulation<br />
comprising multiple full and incremental<br />
backups generated a total of over 123TB of<br />
backup data. On completion, Commvault's<br />
own deduplication had only sent 27TB to the<br />
EX84, resulting in an initial 4.5:1 reduction<br />
ratio. ExaGrid's adaptive deduplication<br />
subsequently squashed this down further to only<br />
8.7TB resulting in an impressive overall<br />
reduction ratio of 14:1.<br />
Enterprises looking for new ways to energise<br />
their data protection strategies and reduce<br />
ongoing storage costs will find this ExaGrid and<br />
Commvault team provides an innovative<br />
solution. ExaGrid's scale-out architecture<br />
delivers huge, cost-effective backup capacities,<br />
its smart Landing Zone provides a boost in<br />
performance, and combining its Adaptive<br />
Deduplication with Commvault's own highly<br />
efficient data reduction technologies offers<br />
industry-leading storage savings. <strong>NC</strong><br />
Product: EX84<br />
Supplier: ExaGrid<br />
Web site: www.exagrid.com<br />
Tel: +44 (0) 1189 497 051<br />
10 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
PLEASE VOTE NOW<br />
Many thanks to everyone who made nominations for the Awards this year. As our search for<br />
the Champions of <strong>2022</strong> continues we ask for your help again.<br />
Please vote now at:<br />
WWW.NETWORKCOMPUTINGAWARDS.CO.UK<br />
The Awards ceremony - 23rd <strong>Jun</strong>e - Leonardo City Hotel,<br />
8-14 Coopers Row, London EC3N 2BQ<br />
Be there to experience the drama as the results are revealed and the trophies are presented. A<br />
drinks reception, dinner and entertainment will also be provided at this special event.<br />
IS YOUR COMPANY A CONTENDER FOR AN AWARD? If you haven't booked your tickets<br />
yet, now would be a good time. Contact dave.bonner@btc.co.uk<br />
The Awards are sponsored by
FEATURE: ZERO TRUST<br />
ZERO TRUST: THE TRUTH IS OUT THERE<br />
THE CONNECTED WORLD IS A CHANGED WORLD, AND ENTERPRISES CAN NO LONGER ASSUME THEY<br />
HAVE FULL CONTROL OVER CLOSED NETWORKS, ACCORDING TO MATTHEW MARGETTS, DIRECTOR OF<br />
SALES AND MARKETING AT SMARTER TECHNOLOGIES<br />
The COVID-19 pandemic further<br />
accelerated the new normal, which shifted<br />
a large proportion of the workforce to<br />
remote working and forced businesses to<br />
increase their use of cloud platforms to support<br />
a variety of devices and networks.<br />
Unfortunately, criminals can take advantage of<br />
this upheaval and attempt to increase network<br />
infiltrations for nefarious gains.<br />
The truth is that legacy security solutions<br />
cannot support a Zero Trust network. In the<br />
legacy model, security measures are reliant on<br />
a closed perimeter security model that assumes<br />
that all users and applications are coming from<br />
the same network location and entry points.<br />
This approach is no longer sufficient, which is<br />
why Zero Trust security is becoming the<br />
preferred network security architecture.<br />
WHAT IS ZERO TRUST SECURITY?<br />
Zero Trust architecture is an approach to IT<br />
system design where inherent trust in the<br />
network is removed. The network is assumed<br />
to be hostile, and each request is verified<br />
based on an access policy. Regardless of the<br />
device, network and user activity, Zero Trust<br />
architecture is built on access management<br />
checks at every level.<br />
The National Cyber Security Centre (<strong>NC</strong>SC)<br />
says: "In a Zero Trust architecture, inherent trust<br />
is removed from the network. Just because<br />
you're connected to a network doesn't mean<br />
you should be able to access everything on that<br />
network. This is commonly seen in breaches;<br />
an attacker gains a foothold in a network and<br />
is able to move laterally because everything on<br />
the network is trusted. In a Zero Trust<br />
architecture, the network is treated as hostile."<br />
The key concepts of Zero Trust are:<br />
The network is hostile and should be<br />
treated as compromised<br />
Inherent trust is removed from the network<br />
Every request to access data or a service<br />
should be authenticated and authorised<br />
against an access policy<br />
Gain confidence dynamically by<br />
continuously evaluating the trustworthiness<br />
of connections<br />
THE 8 DESIGN PRI<strong>NC</strong>IPLES OF A ZERO<br />
TRUST NETWORK<br />
The <strong>NC</strong>SC has introduced eight Zero Trust<br />
architecture design principles that are paving<br />
the way for future networks for the government.<br />
These eight principles are intended to help the<br />
public sector and large organisations to<br />
implement a Zero Trust network architecture in<br />
an enterprise environment.<br />
1. Know your architecture, including users,<br />
devices, services and data<br />
2. Know your user, service and device<br />
identities<br />
3. Assess user behaviour, service and device<br />
health<br />
4. Use policies to authorise requests<br />
5. Authenticate and authorise everywhere<br />
6. Focus your monitoring on users, devices<br />
and services<br />
7. Don't trust any network, including your own<br />
8. Choose services that have been designed<br />
for Zero Trust.<br />
Let's take a closer look at the eight<br />
principles' objectives:<br />
1. Know your architecture, including users,<br />
devices, services and data<br />
To get the benefits from Zero Trust, you need to<br />
have a clear understanding about each<br />
component of your architecture so that you<br />
can identify:<br />
Where your key resources are<br />
The main risks to your architecture<br />
How to avoid integrating legacy services<br />
that do not support Zero Trust<br />
2. Know your user, service and device identities<br />
An identity can represent a:<br />
User (human)<br />
Service (Software Process)<br />
Device<br />
Each identity should be uniquely identifiable<br />
in a Zero Trust architecture. This is the most<br />
12 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATURE: ZERO TRUST<br />
important factor in deciding whether or not<br />
something or someone should be allowed<br />
access to data or services.<br />
3. Assess your user behaviour, devices and<br />
services health<br />
The most important indicators when looking to<br />
establish confidence in the security of your<br />
systems are:<br />
User behaviour<br />
Service health<br />
Device health<br />
Zero Trust policy engines need to be able to<br />
measure user behaviour, device health and<br />
service health.<br />
4. Use policies to authorise requests<br />
The power of a Zero Trust architecture lies in<br />
the defined access policies. Each request for<br />
services or data should be authorised against a<br />
specific security policy. These policies also help<br />
to facilitate safer sharing of data or services<br />
with partner organisations or guest users. The<br />
key characteristics of a policy engine in a Zero<br />
Trust architecture are:<br />
Uses multiple signals<br />
Provides a secure and flexible access<br />
control mechanism<br />
Adapts to the resources being requested<br />
5. Authenticate & authorise everywhere<br />
Any authentication and authorisation activities<br />
should consider multiple signals, such as:<br />
Device health<br />
Device location<br />
User identity<br />
Status to evaluate the risk associated with<br />
the request.<br />
Because the network is assumed to be<br />
hostile, a Zero Trust architecture ensures that<br />
all connections that access your organisation's<br />
data or services are authenticated and<br />
authorised.<br />
6. Focus your monitoring on users, devices<br />
and services<br />
In a Zero Trust architecture, monitoring should<br />
always link back to the policies you have set<br />
with regards to gaining assurance. A Zero Trust<br />
monitoring strategy focuses on individual users,<br />
user behaviour, devices and services to help<br />
organisations establish their health.<br />
7. Don't trust any network, including your own<br />
In a Zero Trust architecture, traditional user<br />
protections such as phishing protection and<br />
malicious website filtering may be<br />
implemented differently and may require<br />
different solutions. A key principle of Zero<br />
Trust is to remove inherent trust from any<br />
network between a device and a service -<br />
including the local network. Any<br />
communication over a network to access data<br />
or services should use a secure transport<br />
protocol to ensure that the traffic is protected<br />
in transit and is less susceptible to threats.<br />
8. Choose services designed for Zero Trust<br />
Not all services support Zero Trust, which<br />
means that they may require additional<br />
resources to integrate Zero Trust architecture.<br />
This causes an increased support overhead, so<br />
it's advisable to consider alternative services<br />
and products that have been designed with<br />
Zero Trust architecture in mind. Products with<br />
Zero Trust capabilities allow for easier<br />
integration and simpler interoperability.<br />
ADOPTING ZERO TRUST PRI<strong>NC</strong>IPLES IN<br />
YOUR ORGANISATIONS<br />
If you are new to Zero Trust or if you're<br />
unsure whether it is the right network<br />
architecture for your needs, it's a good idea<br />
to engage with a digital transformation<br />
partner to help you design and review a<br />
Zero Trust architecture that meets your<br />
organisation's specific requirements. <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 13
FEATURE: ZERO TRUST<br />
ZERO TRUST ARCHITECTURE: 5 REASONS YOU NEED IT<br />
ADRIAN TAYLOR AT A10 NETWORKS EXPLAINS WHY A ZERO TRUST ARCHITECTURE IS THE IDEAL WAY TO<br />
MITIGATE A BREACH IN YOUR NETWORK<br />
There's a relatable metaphor that best<br />
describes how network security<br />
architectures have evolved. People<br />
living in small towns usually know all their<br />
neighbours, so hardly anyone locks their<br />
doors. But for people living in bigger towns,<br />
it's much harder to know who their<br />
neighbours are, so everyone starts locking<br />
their doors. People not only lock their<br />
doors, they also install security systems, put<br />
bars on their windows, and might even get<br />
a guard dog.<br />
In other words, when you have limited risk,<br />
your network security architecture can be<br />
simple but as the risks become greater -<br />
when certainty in your security decreases -<br />
then you need to rethink how to keep your<br />
property safe. As a consequence, security<br />
becomes more complicated.<br />
In the late '80s through the early '90s,<br />
network security was simple; once an entity (a<br />
person, a machine, a process) was inside<br />
your network and authenticated with your<br />
security service it was assumed that entity was<br />
trustworthy. Of course, this couldn't last for<br />
long. As networks started to become more<br />
central to business operations and the need<br />
arose for external connections for business<br />
partners, network complexity increased<br />
exponentially. By the late '90s, these networks<br />
began connecting to the internet, and by the<br />
2000s, hundreds of service providers<br />
complicated networks further by offering<br />
software-as-a-service (SaaS).<br />
THE END OF SIMPLE NETWORK<br />
SECURITY<br />
By 2010, the network no longer had a single,<br />
unbroken network perimeter. It had become<br />
"porous" to support mobile and remote<br />
workers, as well as business partners and new<br />
third-party services. "One and done"<br />
authentication of entities requesting access<br />
became inadequate. You could no longer<br />
assume that anyone on your network,<br />
including your staff, could be trusted.<br />
14 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATURE: ZERO TRUST<br />
A BETTER NETWORK SECURITY<br />
ARCHITECTURE<br />
In 2010, John Kindervag, an analyst at<br />
Forrester Research, wrote a paper that<br />
popularised the idea of the Zero Trust<br />
architecture. Over the next few years, as<br />
enterprise computing embraced cloud<br />
computing and the problems with perimeter<br />
security became more pressing, the concept<br />
of the Zero Trust architecture gained<br />
traction. The fundamental concept of the<br />
Zero Trust architecture is simple: Never trust,<br />
always verify.<br />
HOW TO BUILD A ZERO TRUST<br />
ARCHITECTURE<br />
Zero Trust network architectures have four<br />
main requirements:<br />
The use of micro-perimeters and microsegments<br />
to restrict traffic flow and limit<br />
user privileges and access as much as<br />
possible. Micro-perimeters take the<br />
concept of a secured network perimeter<br />
that defines what is inside of the network<br />
and what is outside and applies similar<br />
access controls to smaller groupings of<br />
network entities, sometimes even to a<br />
single device. Micro-segmentation creates<br />
zones within data centres and cloud<br />
environments to isolate workloads and<br />
secure them individually<br />
Effective incident detection and response<br />
using comprehensive analytics and<br />
automation<br />
Integrated multi-vendor network solutions<br />
to ensure seamless compliance and<br />
unified cybersecurity<br />
Comprehensive and centralised visibility<br />
into all entities and workflows including<br />
users, devices, data, the network itself,<br />
and workflows. Including visibility into all<br />
encrypted communications.<br />
To reiterate, the Zero Trust security<br />
architectures are based on not trusting<br />
anyone or anything on your network. Every<br />
access attempt by any entity, even if known,<br />
must be validated at multiple points to make<br />
sure no unauthorised entity moves into or<br />
within the network without being detected.<br />
Making a Zero Trust network work requires<br />
in-depth traffic inspection and analytics.<br />
Central to this is the use of SSL inspection<br />
solutions that decrypt and analyse encrypted<br />
network traffic (sometimes called "break and<br />
inspect") to ensure policy compliance and<br />
maintain privacy standards.<br />
By monitoring encrypted traffic to detect<br />
suspicious network communications and<br />
malware payloads as well as attempts to<br />
exfiltrate controlled data, for example, credit<br />
card and social security numbers, SSL<br />
inspection makes it possible for the Zero Trust<br />
model to protect networks from both internal<br />
and external threats.<br />
WHY YOU NEED TO MIGRATE TO A<br />
ZERO TRUST SECURITY ARCHITECTURE<br />
Here are the five crucial reasons to move to a<br />
Zero Trust network:<br />
The complexity of your network - the<br />
number of users, where they work, the<br />
devices they use, the number of<br />
workloads, your use of SaaS, a hybrid<br />
cloud environment, and so on - is just<br />
going to increase. A Zero Trust network<br />
reduces the complexity of securing your<br />
assets and isolating problems<br />
As the complexity of your network is<br />
increasing rapidly, the attack surface of<br />
the network has also expanded. To<br />
reduce vulnerability and regain<br />
control, you must establish microperimeters<br />
and micro-segments<br />
Third-party services such as<br />
SaaS and PaaS can't be<br />
trusted: it takes one breach<br />
to compromise your<br />
network. Creating<br />
robust microperimeters<br />
around<br />
these services is an<br />
absolute must<br />
The internet is,<br />
essentially, an unsecured network, and<br />
cyberattacks from amateurs, organised<br />
crime, and hostile state actors are<br />
increasing rapidly. In addition, the costs of<br />
mitigating a breach or a ransomware<br />
attack have increased enormously. The<br />
financial risks have become profound and<br />
will drastically change IT budgets<br />
Insider threats have also increased rapidly.<br />
A mix of employees working from home<br />
and from branch offices and<br />
simultaneously providing access externally<br />
requires robust and well-structured<br />
security controls.<br />
If you've started down the path to a Zero<br />
Trust network, are you moving fast enough?<br />
Does the C-suite understand the issues, and<br />
will it fund a strategy that might be all that<br />
stands between business success and<br />
irreversible failure? If you've not yet started to<br />
plan and implement a Zero Trust architecture,<br />
there's no time like the present. <strong>NC</strong><br />
Adrian Taylor,<br />
A10 Networks<br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 15
CASE STUDY<br />
A SEAWORTHY DATA CENTRE SOLUTION<br />
HOW SEAJACKS MIGRATED ITS BUSINESS-CRITICAL INFRASTRUCTURE AFTER ITS I<strong>NC</strong>UMBENT DATA<br />
CENTRE ENTERED ADMINISTRATION<br />
Seajacks' fleet of the world's most advanced<br />
self-propelled jack-up vessels provide safe<br />
and efficient offshore oil, gas and wind<br />
solutions across the globe. Seajacks has<br />
completed over 500 wind turbine installations<br />
and has brought a new dimension to the<br />
construction, maintenance and<br />
decommissioning of off-shore platforms.<br />
SEAJACKS' CHALLENGES:<br />
With its incumbent data centre provider<br />
unexpectedly entering administration, Seajacks<br />
had extremely limited time to identify a new<br />
supplier and migrate its business-critical<br />
infrastructure that supports its global fleet of offshore<br />
vessels.<br />
The challenge for Seajacks was to research,<br />
shortlist, select and onboard with a data centre<br />
operator that could work flexibly to<br />
accommodate varied requirements. The short<br />
3-month timeframe and hard deadline meant<br />
the new provider would also have to offer<br />
thorough support at every step of the way. In<br />
addition to securely hosting its primary<br />
operations in a rock-solid data centre, Seajacks<br />
needed commercially critical connectivity links<br />
between its UK HQ in Norfolk and all satellite<br />
offices and vessels.<br />
THE SERVERCHOICE EXPERIE<strong>NC</strong>E<br />
ServerChoice was able to react quickly and<br />
work flexibly to meet all of Seajacks' technical<br />
and operational needs, keeping well within the<br />
tight deadline. Seajacks IT Co-Ordinator,<br />
Daniel Bird, outlines his ServerChoice<br />
experience.<br />
Accessibility: "We needed somewhere with<br />
good road connections and a low riskprofile<br />
that we could pop-out to on a Friday<br />
afternoon. ServerChoice provided a toptier,<br />
secure data centre in just the right<br />
location."<br />
Tailored Cost-Package: "In the first<br />
instance, we explored a number of<br />
different configuration options with<br />
ServerChoice. They helpfully quoted all<br />
these across 3 to 5 years to provide us<br />
with a range of price options."<br />
Responsive Service: "Adam has been our<br />
contact from our initial sales call. He's been<br />
there from the site tour through to<br />
onboarding, and it's him we contact on the<br />
rare occasions we have a question."<br />
THE SERVERCHOICE SOLUTION<br />
Smarter thinking<br />
ServerChoice offered space in its awardwinning<br />
Harlow Data Centre, just north of<br />
London, in the UK's largest and most innovative<br />
data centre campus. Its location puts it within<br />
easy reach, but crucially provides a much lower<br />
risk profile than London-based facilities, which<br />
was a vital consideration for Seajacks' missioncritical<br />
global operations.<br />
The resilience, efficiency and security of<br />
Harlow Data Centre is immediately apparent<br />
from a tour of the state-of-the-art site. Built to a<br />
minimum of Tier 3 Standards throughout, the<br />
data centre uses 100% renewable energy and<br />
features advanced security, including threefactor<br />
authentication and biometric access<br />
controls. The facility is provisioned with highdensity<br />
racks, is OCP-Ready, and is truly carrierneutral,<br />
with low-latency fibre routes directly<br />
connecting to major tier1 provider and strategic<br />
PoPs across Europe.<br />
"The facility is better than Tier 4 in many<br />
regards, and the high level of security exceeded<br />
our expectations," says Daniel Bird.<br />
A trusted partner<br />
The original Internet requirement was for 200<br />
Mbps, but after listening to Seajacks'<br />
challenges, ServerChoice upgraded the<br />
connection to 1 Gbps. This provided a highperformance,<br />
future-proof and cost-effective<br />
connection that also lowered future upgrade<br />
costs. ServerChoice also offered FlexMove®, its<br />
free relocation service.<br />
ServerChoice was on-hand to offer support<br />
and guidance through every stage of the<br />
process, from Seajacks' initial sales enquiry call<br />
right through to go-live, to ensure that Seajacks<br />
were up and running smoothly and successfully.<br />
And with ServerChoice's proven 100% uptime<br />
track record, there's been little need for<br />
Seajacks to test the on-site 24/7 support.<br />
Bird adds, "It sits in the background and ticks<br />
along nicely. It's a great service and I know we<br />
can rely on it." <strong>NC</strong><br />
16 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
PRODUCT REVIEW<br />
CloudCall - The CRM<br />
Centric<br />
Communications<br />
Platform<br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
As businesses move their phone system<br />
into the cloud, it makes perfect sense to<br />
integrate it with their customer<br />
relationship management (CRM) solution.<br />
Aligning a cloud phone system with a CRM<br />
can improve communications, provide<br />
accurate customer and prospect interaction<br />
and data tracking which allows for streamlined<br />
sales processes.<br />
The intelligent phone system from CloudCall<br />
stands out from its competitors as it is<br />
designed to help integrate seamlessly with all<br />
major CRM vendors. The list is extensive and<br />
includes the likes of, but not limited to,<br />
Salesforce, Bullhorn, Microsoft Dynamics 365,<br />
Vincere, Access, Tracker and Zoho.<br />
At its foundation, CloudCall provides cloudhosted<br />
business VoIP solutions and employs inhouse<br />
developers to work with partner teams<br />
for all CRM integrations. This allows<br />
businesses to use CloudCall to maintain a<br />
single source of information and provide an<br />
accurate viewpoint of what is happening in the<br />
business relating to customer activities.<br />
The CloudCall Click-2-dial feature is a<br />
perfect example as it allows staff to instantly<br />
initiate calls directly from a CRM record.<br />
Furthermore, when a call is made from the<br />
CRM, CloudCall automatically logs all call<br />
details and opens a note file linked to the<br />
recipient, making sure all your call data is<br />
automatically synced into one central source.<br />
An SMS can be sent directly from a CRM<br />
record and its list of contacts used to swiftly<br />
broadcast SMS to multiple recipients. The<br />
CloudCall Chrome extension allows mobile<br />
SMS to be sent directly, simply by hovering the<br />
mouse pointer on a web page that contains a<br />
phone number.<br />
The embedded Power Dialler feature reduces<br />
the manual effort required when making<br />
multiple calls to customers and candidates.<br />
Using lists built from your CRM or uploaded to<br />
the dialer, it will call the contacts in sequence<br />
and can be used to prioritise calls so you can<br />
reach out to the most promising prospects first.<br />
It can also be combined with CloudCall's<br />
voicemail drop, where users can set up to five<br />
pre-recorded messages making sure you leave<br />
the correct information with each recipient.<br />
Inbound calls and SMS are handled just as<br />
efficiently by CloudCall's Screen Pops. These<br />
present a pop-up window feature allowing the<br />
user to open the associated CRM record<br />
instantly without having to waste valuable time<br />
searching for it.<br />
Call recording features are equally<br />
impressive as CloudCall saves all the CRM<br />
contact activity history, so they can be easily<br />
accessed for download or playback<br />
purposes. If a verbal consent prior to call<br />
recording is a business requirement,<br />
CloudCall will capture and store these details<br />
while a user is on the phone.<br />
The extensive call handling features of<br />
CloudCall offer valuable monitoring and<br />
training aids to help managers. These<br />
include the CloudCall web portal which can<br />
monitor all calls being made, listen to them<br />
in real-time and use features such as the<br />
whisper function to provide guidance and<br />
training, the barge function in times of need<br />
if required, and can even turn it into a<br />
conference call to help you connect teams.<br />
The portal provides a central<br />
administrative point where you can create<br />
custom activity dashboards to present<br />
advanced real-time analytics. It can<br />
manage your organisation's call profiles<br />
while access to all activities and<br />
communications reports, detailed call<br />
logs, notes and recordings are never more<br />
than a few clicks away.<br />
CloudCall solves the challenges faced by<br />
businesses that have invested heavily in<br />
cloud phone services and CRM. With<br />
support for all key CRM providers,<br />
CloudCall removes all the manual effort<br />
required by administrators to keep these<br />
two core systems constantly updated and<br />
aligned to deliver a measurable boost to<br />
productivity and business growth. <strong>NC</strong><br />
Product: CloudCall<br />
Supplier: CloudCall<br />
Web site: www.cloudcall.com<br />
Tel: +44 (0)203 854 4000<br />
WWW.NETWORKCOMPUTING.CO.UK MAY/JUNE 17<br />
NETWORKcomputing<br />
@<strong>NC</strong>MagAndAwards
PRODUCT REVIEW<br />
Perle IOLAN SCG<br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
Managing data centres and large<br />
distributed networks demands remote<br />
access to critical infrastructure<br />
devices as issues can be quickly resolved<br />
before they become disasters. This avoids<br />
tedious and expensive site visits, but if the<br />
network at the remote site fails, support staff<br />
will lose access to these devices.<br />
Perle Systems has the ideal solution as its<br />
IOLAN remote console servers provide highly<br />
redundant OOB (out-of-band) management<br />
access to critical network devices. They look to<br />
have every eventuality covered as along with<br />
dual, redundant Gigabit copper and fibre<br />
ports for WAN access, they can fall back to a<br />
wireless network, an integral V.92 modem or a<br />
high-speed 4G LTE cellular network.<br />
The IOLAN SCG on review is highly<br />
versatile as its modular design allows up to<br />
three 16-port serial interface cards to be<br />
installed for a total of 50 management ports.<br />
The RJ45 modules support softwareselectable<br />
RS232, RS422 and RS485 modes<br />
and can be mixed with USB versions.<br />
Teaming the latter up with the two USB ports<br />
at the front allows Perle to claim an industryleading<br />
USB serial port density.<br />
The appliance provides full IPv4/IPv6 routing<br />
capabilities plus support for RIP, OSPF, and<br />
BGP protocols for easy integration into data<br />
centres including VRRPv3 for network<br />
redundancy support. Zero-touch provisioning<br />
ensures a swift initial deployment while<br />
RESTFul API and VPN support allows it to work<br />
closely with customer's third-party<br />
management systems.<br />
Deployment is simple and the appliance's<br />
web console dashboard shows plenty of detail<br />
on the system while a list of all interfaces<br />
below reveals their link status along with<br />
inbound and outbound traffic. Interface high<br />
availability and failover are handled by health<br />
profiles which use Ping and traceroute tests to<br />
determine their availability. If the primary<br />
WAN connection goes down, you can elect to<br />
automatically swap to another available WAN<br />
connection or assign priorities to them for<br />
load sharing.<br />
Each RJ45 serial interface offers a wide<br />
range of services with the Console<br />
Management profile used to create a serial<br />
port for Telnet or SSH access. Other profiles<br />
include Trueport virtual COM ports, TCP and<br />
UDP sockets, virtual modem and Modbus<br />
gateway emulation while the USB ports can<br />
use Console Management, Trueport and TCP<br />
socket service profiles.<br />
Access security is excellent as along with an<br />
integral firewall, you can enable 2FA on<br />
selected user accounts and apply a range of<br />
AAA (authentication, authorisation,<br />
accounting) services using Radius, TACACS+<br />
or LDAP. When creating user accounts, you<br />
can set them as operators so they can't<br />
manage the appliance and decide which ports<br />
they are allowed to access.<br />
Operators have two options for accessing<br />
serial port devices as they can use their<br />
personal web console to view the ports they<br />
are permitted to see, choose one from the<br />
Monitor and Stats screen and click on the<br />
Easyport button to load an SSH session in a<br />
new browser. The other alternative is to use a<br />
client such as PuTTY to SSH to the appliance<br />
using the port number assigned to the serial<br />
port they want to connect to, login in with<br />
their IOLAN username and then supply the<br />
device credentials.<br />
It's very simple to use and we had no<br />
problems connecting the RJ45 console ports<br />
of our lab switches to the appliance with<br />
standard Cat6 network cables. Using either<br />
method, we could quickly set up SSH sessions<br />
and access their CLIs.<br />
Perle's IOLAN SCG is the perfect solution<br />
for support staff that need always-on remote<br />
OOB access to their core network devices.<br />
The appliance is easy to manage, its<br />
modular design makes it very flexible and its<br />
tough security measures allow access to be<br />
strictly controlled. <strong>NC</strong><br />
Product: IOLAN SCG<br />
Supplier: Perle<br />
Web site: www.perle.com<br />
Sales: +44 1280 825 540<br />
18 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATURE: PUBLIC SECTOR IoT<br />
IoT: THE KEY TO HELPING PEOPLE LIVE BETTER AND HEALTHIER LIVES<br />
TIM KIDD, HEAD OF UK PUBLIC SECTOR AT HITACHI SOLUTIONS, SHARES HIS EXPERIE<strong>NC</strong>E OF<br />
WORKING ON A LEADING INTERNET OF THINGS PROJECT IN LONDON<br />
As technology advances, a huge volume<br />
of data is being produced that can<br />
help public sector decision makers<br />
make the right choices for society's<br />
happiness, health, and prosperity. The<br />
problem is making the information easily<br />
understood and readily available.<br />
THE INNOVATE PROJECT<br />
The InnOvaTe project is a collection of 40<br />
yearlong trials across five London boroughs<br />
that uses sensors to gather information about<br />
a range of social issues. The work, organised<br />
by the South London Partnership (SLP), has<br />
been gathering data on a range of issues,<br />
from air pollution to social care, to help<br />
improve society. The results aren't just<br />
theoretical. IoT sensors installed in homes of<br />
vulnerable people to monitor movements<br />
were able to alert carers when a resident,<br />
Maureen, fell at home. Ambulance staff who<br />
attended the scene credited the quick<br />
response with saving her life.<br />
The InnOvaTe trial has clearly been a huge<br />
success for the five boroughs involved. The<br />
volume of data provided, and individual stories<br />
like Maureen's prove it. However, the question<br />
remains how we convert huge amounts of data<br />
into easily understood and readily available<br />
information so that decision makers in the<br />
public sector can use it effectively.<br />
MAKING DATA READILY AVAILABLE<br />
AND EASILY UNDERSTOOD<br />
Following a comprehensive procurement<br />
process, the SLP team selected Hitachi<br />
Solutions and our partners at Microsoft to take<br />
on the challenge of making the information<br />
gathered by the InnOvaTe project readily<br />
available and easily accessible. It is no small<br />
task given the volume of invaluable data<br />
collected. We are also keenly aware that our<br />
work is directly linked to achieving better<br />
outcomes for society; keeping residents safe,<br />
improving quality of life, making urban areas<br />
cleaner, ensuring transport infrastructure keeps<br />
moving and expediting the move to other<br />
greener travel modes.<br />
Our solution has been to use Microsoft's<br />
Azure cloud platform to create a single unified<br />
platform that draws in all the data being<br />
collected for the different sensors. The system<br />
creates visualisations and dashboards to help<br />
the maximum number of people access,<br />
understand and ultimately use the data.<br />
KEEPING DATA SAFE<br />
Given the sensitivity of the data we are<br />
handling, the solution was designed with<br />
GDPR and data privacy in mind as a first<br />
principle, with data encryption at rest and in<br />
transit. Secure access is achieved through Role<br />
Based Access Controls meaning only named<br />
users are granted access to relevant aspects of<br />
the data that they have a need to use and are<br />
authorised to view. This access is tied to their<br />
Active Directory account. Azure has granular<br />
audit logs that can see who accesses what<br />
and when. Whilst Microsoft ultimately host the<br />
data within the Azure cloud, due to the multilayered<br />
security approach of their personnel,<br />
no one person can ever have direct access to<br />
the data making it a safe and secure<br />
integrated platform.<br />
SUPPORTING PUBLIC SECTOR<br />
DECISION MAKING WITH DATA<br />
Data, IoT and Smart solutions are rapidly<br />
becoming key components of local authority<br />
infrastructures, both in cities and rural areas.<br />
The ability to analyse real-time information to<br />
better understand our societies has huge<br />
potential to make lives happier, healthier, and<br />
more prosperous. In the future, we hope the<br />
technology will contribute to improving the<br />
lives of people and businesses up and down<br />
the UK and beyond.<br />
At its core, IoT is about connecting our<br />
physical environment to a digital world. There<br />
is still a lot of untapped potential in the IoT,<br />
but this partnership showcases the importance<br />
of working together to solve complex<br />
challenges with the best solutions for the<br />
benefit of all. <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE NETWORKcomputing 19
FEATURE: PUBLIC SECTOR IoT<br />
ROLLING OUT IoT TO ADDRESS COUNTY COU<strong>NC</strong>IL CHALLENGES<br />
NICK SACKE, HEAD OF IoT SOLUTIONS AT COMMS365 ADDRESSES SOME OF THE AREAS WHERE IOT<br />
SOLUTIONS CAN BE RAPIDLY ROLLED OUT, TO NOT JUST OVERCOME THE CHALLENGES LOCAL<br />
AUTHORITIES ARE FACING, BUT EXCEED THEM<br />
As the country emerges from the COVID-<br />
19 pandemic <strong>2022</strong> will be a year of<br />
recovery, and local authorities have a<br />
crucial role to play in leading this process.<br />
However, pressures continue to increase from<br />
the government to meet targets on climate<br />
change, improve health and social care and<br />
ensure that local infrastructure continues to<br />
meet increasing demand after the pandemic -<br />
all with restricted financial support. So how<br />
can technology help councils to address and<br />
meet these challenges?<br />
SUSTAINABILITY AND CLIMATE<br />
CHANGE<br />
It is well known that we are still producing<br />
masses of waste across the UK. With<br />
traditional and non-efficient processes still in<br />
place for collecting waste from public places<br />
and homes, it leaves councils and third-party<br />
contractors with a massive challenge. But by<br />
investing in IoT technology, current ineffective<br />
processes can be easily and dramatically<br />
improved - from creating an optimally efficient<br />
route to collect waste to reduce carbon<br />
emissions, to emptying the right bins, at the<br />
right time, to further improve green objectives.<br />
Sensor technology, for example, can not only<br />
indicate how full a bin is, but can also detect<br />
temperature and motion, to see if somebody<br />
has thrown something flammable in the<br />
container, as well as the bin tipping over or<br />
being misplaced. This information can then be<br />
used to build a data profile, which will in turn,<br />
provide a more efficient collections schedule,<br />
and also identify hotspot areas with potential<br />
problems including fly tipping.<br />
Also, technology is becoming more<br />
efficient at determining different types of<br />
waste, particularly within underground<br />
storage, that can be useful for recycling<br />
efforts. By deploying IoT solutions, sensors<br />
can check how much glass is in a specific<br />
container, by comparing the sonic 'signature'<br />
via intelligent algorithms for different types<br />
of waste materials.<br />
IoT can additionally help councils and thirdparty<br />
contractors plan in advance by knowing<br />
how much waste they will be collecting, by<br />
real-time monitoring of waste in the bin lorry<br />
itself, which can help the business to forecast<br />
cost and / or revenue. In turn, this has the<br />
potential to revolutionise payment models for<br />
contractors that are paid by weight.<br />
With heavy regulations coming into play<br />
around air quality, and as we as a society<br />
strive towards a greener future, there is a need<br />
for local authorities to be more proactive and<br />
involved in their citizens' health. By tracking<br />
environmental elements such as pollution<br />
levels, CO2 concentrations in offices and<br />
classrooms and chemical pollutants,<br />
environmental monitoring will become a big<br />
part of both our indoor and outdoor future.<br />
INTEGRATING HEALTHCARE SERVICES<br />
The IoT healthcare market is expected to reach<br />
$188.2 billion by 2025, driven by the<br />
pandemic and increasing focus on patientcentric<br />
services. It's clear that technology can<br />
transform industries, helping to reduce the<br />
burden on primary, acute and community care,<br />
as well as local councils. This was highlighted<br />
during the peak of the pandemic, with<br />
hospitals across the NHS implementing virtual<br />
clinics and remote monitoring technology to<br />
care for patients at home, while focusing on<br />
the ever-increasing COVID-19 cases.<br />
IoT technology enabled the use of health and<br />
care devices to collect valuable and real-time<br />
data to provide care to patients both in and out<br />
of hospital, while keeping them connected to<br />
health care professionals. The data collected<br />
helps to automate the mapping of activities into<br />
a profile around an individual, which can then<br />
be analysed and shared every day with the<br />
care organisation and local authority.<br />
Ongoing patient health and vital signs can be<br />
recorded from home, such as heart rates,<br />
blood pressure and temperature, meaning<br />
clinicians' time can be used elsewhere,<br />
enhancing the efficiency of existing processes.<br />
Specialists can be alerted when deterioration or<br />
health concerns are detected to allow for<br />
immediate intervention and deliver targeted<br />
care. Targeted intervention allows expansion of<br />
existing resources, and a rapid return on<br />
20 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATURE: PUBLIC SECTOR IoT<br />
investment in care-assistive technology. By<br />
flagging any issues earlier and preventing the<br />
escalation of problems while the individual is<br />
at home, the need for them to go to the<br />
hospital for check-ups or treatment is<br />
mitigated, in turn reducing pressure on the<br />
public purse.<br />
Technology can also be used to reduce<br />
inequality of or variation in care by<br />
identifying patients who may be at risk and<br />
have not seen their GP, or those who are in<br />
rural and remote areas, by providing access<br />
to interact with and monitor people in places<br />
that have been traditionally harder to reach.<br />
IoT technology has greatly improved<br />
accessibility and productivity in healthcare,<br />
while keeping patients safe and in the<br />
comfort of their own homes. This provides a<br />
mechanism to help the NHS with extending<br />
their care beyond the hospital, with another<br />
significant return on investment.<br />
LOCAL INFRASTRUCTURE<br />
With almost 50 shops closing a day on the<br />
high street during the first six months of<br />
2021, and UK shopper footfall dropping,<br />
local authorities are now looking for<br />
alternative initiatives to encourage people<br />
back to the high street. If shoppers are<br />
looking to travel to physical stores once<br />
more, the parking experience should be<br />
painless - or else they'll just return to the<br />
convenience of online shopping.<br />
It's estimated that motorists spend two<br />
months of their lifetime searching for a<br />
parking space. But what if this could be cut<br />
down with the use of technology? What if an<br />
individual's mobile device was to alert them in<br />
real-time where a parking space was? Better<br />
yet, what if this space could be reserved, or<br />
set up a subscription model to park monthly?<br />
It's all about data collection and a better,<br />
more informed use of this data. By<br />
incorporating electric charging and disabled<br />
bays, as well as the use of innovative<br />
technology, re-engineered and revitalised<br />
parking solutions will boost council revenue<br />
and provide more efficient and customerpleasing<br />
services, in turn, regenerating the<br />
high street shopping experience<br />
THE RISING COST OF LIVING, ENERGY<br />
AND FUEL POVERTY<br />
At the time of writing, inflation had just<br />
breached 5.5% and is on course to exceed<br />
7%, another record. The price of oil and gas<br />
are rising, producing knock-on effects in the<br />
cost of raw materials and transportation costs,<br />
energy to heat the home, shopping basket<br />
prices, and more. The current economic<br />
climate is creating a punishing set of<br />
circumstances for all, but especially the<br />
elderly, those on low incomes and families<br />
where one or other partner has lost their job<br />
during the pandemic. It has been reported in<br />
the media that in several cases the vulnerable<br />
are already making choices between heating<br />
or eating, which is of grave concern to all.<br />
Many of these vulnerable citizens live in local<br />
authority housing, so what can IoT technology<br />
do to assist?<br />
Specifically in the case of fuel poverty,<br />
monitoring temperature and environmental<br />
conditions in vulnerable households, together<br />
with energy consumption from the boiler will<br />
create a profile of energy use, highlighting<br />
which of the population require targeted<br />
interventions to assist with fuel bills and other<br />
assistance that the local authority has at its<br />
disposal. Smart radiator solutions can also be<br />
implemented to heat sections of the home that<br />
require it at different times of day, providing<br />
energy savings and improved living conditions.<br />
The IoT data collected could also profile and<br />
identify potential dwellings that have insulation,<br />
leaks, and other structural issues that affect the<br />
housing asset integrity and prioritise<br />
intervention. The business case for this type of<br />
technological intervention is already proven<br />
through current projects in the UK.<br />
CO<strong>NC</strong>LUSION<br />
IoT technology is advancing to meet ever more<br />
imposing challenges and requirements. We're<br />
not only seeing an uptake in interest and the<br />
use of these solutions, but the technology itself<br />
is becoming increasingly cost-effective,<br />
adaptable, and easier to deploy and maintain.<br />
The COVID-19 crisis has prompted a greater<br />
need and priority for local councils to be<br />
forward-thinking in how digital technology and<br />
data can help towns recover now and strive in<br />
the future. The value of IoT technology and the<br />
real-time data it collects is being recognised,<br />
and will help to inform better decision-making,<br />
introduce early interventions and reduce the<br />
cost of changing practices. But for this to work<br />
in practice, there is a significant need for a<br />
cultural shift in the relationship local<br />
governments have with technology.<br />
The technological solutions must be designed<br />
around the user, creating a better customer<br />
experience, while ensuring any potential<br />
barriers to adoption are removed. The guiding<br />
principle for deploying technology as an<br />
enabler of these more streamlined processes is<br />
simplicity and invisibility to the user, while<br />
collecting valuable data for insight. <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 21
FEATURE: CLOUD<br />
THE FUTURE OF CLOUD-NATIVE IN A BRAVE NEW WORLD<br />
HOW CAN ORGANISATIONS AND THEIR DEVELOPERS CREATING<br />
CLOUD NATIVE SOLUTIONS ENSURE THE HIGHEST LEVELS OF<br />
SECURITY? EREZ YALON, VP OF SECURITY RESEARCH, CHECKMARX<br />
SHARES HIS THOUGHTS<br />
Over the last couple of years, the<br />
global workforce has<br />
experienced a seismic digital<br />
shift, forcing many organisations to turn<br />
to the cloud to maintain business<br />
continuity. According to one report the<br />
growth in cloud services has been<br />
accelerating, with forecasts that the<br />
cloud market could eventually be worth<br />
$1 trillion.<br />
Part of this shift has been the evolution<br />
of cloud-native. A modern approach to<br />
building and running applications,<br />
cloud-native has gone from a<br />
marketing term to a highly<br />
desirable and useful architecture choice.<br />
Yielding benefits around the design,<br />
building, and deployment of applications,<br />
it's easy to see why it's become the default<br />
approach for many organisations.<br />
Although convenient, cloud-native<br />
applications have intricate and layered<br />
attack surfaces which are widely<br />
misunderstood and thus under-secured.<br />
As a result, they have introduced a new<br />
series of challenges for application<br />
security (AppSec), proving that it is now<br />
imperative for organisations to learn how<br />
to effectively secure their interconnected,<br />
cloud-based solutions.<br />
With investment in digital technologies<br />
underpinned by cloud solutions set to<br />
increase, how can organisations and their<br />
developers creating cloud native solutions<br />
ensure the highest levels of security?<br />
22 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATURE: CLOUD<br />
SECURING THE NEW HYBRID<br />
ECOSYSTEM<br />
We know that in today's modern software<br />
era, with the continued explosion of<br />
emerging technologies, digital<br />
transformation journeys, and the move to<br />
cloud-native, demands on developer teams<br />
to create secure code have increased.<br />
Here are three best practice steps to<br />
which developers should adhere to in<br />
order to effectively secure their<br />
interconnected, cloud-based solutions:<br />
1. Testing code from the first line: No<br />
portion of a code base is inherently<br />
secure, and every line needs to be<br />
inspected from the beginning of<br />
development to ensure vulnerabilities<br />
are found and addressed. It is also<br />
important to remember that, when<br />
new features and functionalities are<br />
added to the application, the<br />
introduced code blocks must be<br />
given the same time and attention as<br />
all other pieces in the bigger<br />
software puzzle.<br />
2. Ensuring each component is secure:<br />
It's vital to test everything, including<br />
third-party components and APIs, as<br />
it's common for vulnerabilities to lurk<br />
in their shadows. A 'trust and verify'<br />
approach is paramount - meaning<br />
organisations trust but make a<br />
concentrated effort to also verify and<br />
validate - third-party solutions and<br />
components before using them. As we<br />
continue to build applications from a<br />
diverse set of components, blindly<br />
trusting that third-party technologies<br />
are secure is a recipe for disaster.<br />
3. Test the infrastructure as code (IaC):<br />
With the transition to the cloud came<br />
new challenges for software<br />
developers, namely the abundance of<br />
IaC. This is evidenced by our survey,<br />
which found that one in six developers<br />
aren't performing any security testing<br />
when building cloud-native<br />
applications, having a major impact<br />
on the security of their applications.<br />
Therefore, just as you take careful<br />
steps to testing and securing<br />
applications, the same must be done<br />
when it comes to IaC.<br />
COMMON PITFALLS WHICH<br />
HINDER PROGRESS<br />
Time and time again, we have seen<br />
examples of software full of exploitable<br />
vulnerabilities being released and<br />
subsequently abused by malicious actors.<br />
Moreover, new applications are being<br />
rushed to market every day, further<br />
expanding the attack surface at an<br />
unprecedented pace.<br />
There are a number of pitfalls which<br />
developers are falling for that are<br />
hindering their progress and allowing<br />
attackers easy access into their solutions.<br />
These include:<br />
1. Not embedding application security<br />
testing (AST) early enough in the<br />
application development process:<br />
AST solutions do not replace security<br />
awareness and common sense but<br />
they do deploy a safety net and<br />
enable security to become an<br />
inherent part of development;<br />
however, developers frequently<br />
implement security solutions after<br />
development is completed. This<br />
perspective needs to change as it is<br />
cheaper and easier to fix security<br />
vulnerabilities earlier in the lifecycle.<br />
2. Not understanding the nuances<br />
between traditional AppSec vs. cloudnative<br />
security: To properly secure<br />
cloud-native apps, these nuances must<br />
be understood. Generally, traditional<br />
AppSec is more contained; whereas<br />
with cloud-native, there are many<br />
more components and connections<br />
interacting and "speaking" to each<br />
other to make it all work. While this<br />
makes for more dynamic applications,<br />
it also creates an exponentially larger<br />
attack surface. Security teams and<br />
software developers are now tasked<br />
with learning to build applications in a<br />
completely new environment while<br />
evolving the way they test for security<br />
vulnerabilities.<br />
3. Dispersed security responsibilities: The<br />
ownership of security has changed<br />
hands too. With dispersed code and<br />
responsibility for digital transformation<br />
projects sitting across multiple teams,<br />
comes dispersed security<br />
responsibilities. Now, developers,<br />
DevOps, and IT teams need to take<br />
on this responsibility together. This<br />
shared ownership may be complex,<br />
but it's necessary given how easy it is<br />
for security to be an afterthought.<br />
LOOKING AHEAD<br />
Cloud-native is the future. Undoubtedly, it<br />
is a central part of software development<br />
in the brave new world in which we find<br />
ourselves living. However, with the<br />
additional challenges it brings and the<br />
pace at which it's being implemented,<br />
organisations must consider the security<br />
practices needed to ensure that<br />
developers see security as a vital step in<br />
software development, rather than an<br />
added layer of complexity.<br />
With greater awareness of the<br />
challenges the new hybrid ecosystem<br />
brings, and by adopting the<br />
aforementioned best practices to<br />
overcome these obstacles, organisations<br />
can ensure their teams are utilising the<br />
full benefits of cloud native, while<br />
significantly lowering the risk. <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 23
FEATURE: CLOUD<br />
GOVERNMENT CLOUD ON-RAMPING<br />
NOW'S THE TIME FOR UK GOVERNMENT DEPARTMENTS TO FULLY<br />
EMBRACE DIGITAL TRANSFORMATION ACCORDING TO PAUL<br />
GERMAN, CEO, CERTES NETWORKS<br />
The UK Treasury is becoming<br />
increasingly frustrated by the billions<br />
of pounds wasted by government<br />
departments on legacy technology and<br />
proprietary infrastructure. With Digital<br />
Transformation now imperative, there is<br />
little patience for the endemic delays in<br />
decision making that are adding untenable<br />
costs to a government that simply has no<br />
more resources.<br />
Why are departments still spending<br />
£millions every month on expensive<br />
proprietary connectivity when the tried, tested<br />
and proven Software Defined Wide Area<br />
Network (SD-WAN) alternative costs just a<br />
fraction? How can departments justify the<br />
use of outdated legacy systems that demand<br />
huge expenditure just to keep up and<br />
running when reliable, lower cost cloudbased<br />
alternatives are so accessible?<br />
With the High Assurance SD-WAN<br />
framework now generally available, there<br />
are no more excuses. Digital Transformation<br />
must progress, quickly, and while the risks<br />
used to outweigh the rewards the rewards<br />
now significantly outweigh the risks.<br />
WEAK EXCUSES<br />
Digital Transformation is now vital for<br />
government departments. After two years of<br />
pandemic delayed projects and facing<br />
unprecedented financial pressures, there is<br />
zero tolerance for excuses. Not only are<br />
legacy systems both unreliable and<br />
expensive, but the cloud offers many benefits<br />
in flexibility, agility and cost reduction. And<br />
yet, an estimated 80% of UK government<br />
departments are still failing to make the<br />
move, with their cloud strategies on hold.<br />
24 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATURE: CLOUD<br />
So what's going on? Many departments have<br />
clearly defined Digital Transformation<br />
roadmaps; cloud providers have been<br />
selected - often more than one to provide<br />
resilience and contingency - and application<br />
migration plans have been defined. The one<br />
remaining sticking point is data security - most<br />
notably, the safeguarding of data in transit<br />
between the on site systems and the cloud.<br />
With departments typically opting for a hybrid<br />
environment during the incremental Digital<br />
Transformation process, rather than a<br />
wholesale move to the cloud, it is clearly<br />
important to extend the data security posture<br />
between the current environment and the<br />
cloud. Furthermore, there is no argument that<br />
Government departments have stringent data<br />
security requirements - much of the data is<br />
highly sensitive. Compromising security due to<br />
the impact on network performance is, clearly,<br />
not a viable option - or for those organisations<br />
who have chosen that route, an extremely high<br />
risk alternative, particularly given increasingly<br />
concerning geopolitical circumstances.<br />
Claims that the use of low cost SD-WANs to<br />
provide the vital link to the cloud are inherently<br />
lacking in the security required to safeguard<br />
sensitive data, however, are out of date. Yes,<br />
SD-WANs use public infrastructure, but the<br />
Common Criteria accredited High Assurance<br />
SD-WAN framework that couples a High<br />
Assurance security overlay with market leading<br />
SD-WAN technologies, is proven and being<br />
used by governments and organisations<br />
across the world to safely accelerate Digital<br />
Transformation plans.<br />
SECURITY STAND-OFF<br />
The only beneficiaries of this endemic<br />
decision-making paralysis are technology<br />
vendors and service providers raking in<br />
£millions every month to support and<br />
maintain outdated, often inadequate,<br />
technology. Given the huge cost differential<br />
between legacy and cloud-based solutions,<br />
the biggest risk now facing UK government is<br />
that individuals tasked with achieving Digital<br />
Transformation and radically reducing IT<br />
spend will feel compelled to simply ignore<br />
data security issues.<br />
With a desire to achieve a stable, effective<br />
and scalable technology infrastructure, it is a<br />
hugely frustrating situation for IT and network<br />
teams - not to mention those with budgetary<br />
sign off. While the risks associated with failing<br />
to consider the security implications are<br />
profoundly serious, there is no more money:<br />
unless this stand-off is addressed, everyone<br />
involved stands to lose.<br />
Security must be at the heart of any Digital<br />
Transformation journey - and that requires a<br />
shift towards a Zero Trust mindset. It means<br />
stepping away from the concept of a trusted<br />
environment and a focus on securing the data<br />
irrespective of its location. This is where High<br />
Assurance SD-WAN frameworks change the<br />
game, using crypto-segmentation to protect<br />
and ensure the integrity of sensitive data -<br />
without any impact on network performance.<br />
ACCELERATING CHANGE<br />
With this Zero Trust approach, a High<br />
Assurance SD-WAN overlay makes the<br />
underlying network infrastructure irrelevant,<br />
whether it is public or private, trusted or<br />
untrusted. The data security team simply needs<br />
to define the policy and, with ownership of the<br />
cryptography keys, can be confident that data<br />
is protected at all times wherever it goes.<br />
The model is akin to the transfer of gold or<br />
cash between banks. Security at each bank is<br />
established and accepted - it is the movement<br />
between the banks that raises concerns. The<br />
use of a secured armoured vehicle is<br />
reinforced by locking the gold away in a<br />
secure environment using keys that only the<br />
bank - not the guards - have access to.<br />
Similarly with crypto-segmentation, even if the<br />
data is compromised in transit, the only<br />
people who have access to the keys are the<br />
owners of the data: no one else can do<br />
anything with that data. Irrespective of where<br />
that data is travelling, it is protected.<br />
For government departments the High<br />
Assurance approach to SD WAN enables the<br />
secure utilisation of low-cost SD-WAN<br />
connectivity, which is a huge financial<br />
incentive. Furthermore, there are no<br />
constraints on network redesign; no barriers to<br />
the types of data or applications that can be<br />
migrated to the cloud, which ensures both<br />
operational agility and a consistent data<br />
security posture that can evolve throughout the<br />
Digital Transformation journey, from on<br />
premise, through hybrid, to the cloud. This<br />
means Digital Transformation plans can be<br />
accelerated and departments can quickly<br />
realise economies of scale.<br />
CO<strong>NC</strong>LUSION<br />
Delaying Digital Transformation is creating<br />
unacceptable risk and incurring unacceptable<br />
costs. Every postponed decision compromises<br />
progress and leaves government departments<br />
at the mercy of vendors who are continuously<br />
inflating maintenance and support charges.<br />
The transformation away from legacy to<br />
current technology is an absolute must - a fact<br />
clearly recognised by government department<br />
heads who are having to explain, under fire,<br />
why they are continuing to spend Treasury<br />
money on outdated IT projects.<br />
Right now, most decision making committees<br />
are using the concept of data risk as an<br />
excuse for not progressing Digital<br />
Transformation. But any claim that plans<br />
cannot move forward due to regulatory<br />
compliance or internal controls are no longer<br />
true - that risk argument has been addressed<br />
and resolved.<br />
The benefits of Digital Transformation are<br />
indisputable, from systems stability to hugely<br />
significant cost savings: so just what is the<br />
excuse for continued mis-spend of public<br />
money and failure to follow well established<br />
routes to the cloud? <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 25
FEATURE: CLOUD<br />
LEVERAGING THE DATA DELUGE<br />
LAURA MALINS, DIRECTOR OF PRODUCT MANAGEMENT AT<br />
MATILLION, EXPLAINS HOW TO UNLEASH YOUR UNTAPPED<br />
DATA POTENTIAL WITH A MODERN CLOUD STRATEGY<br />
Only as recently as five years ago,<br />
mining data insights in sufficient time<br />
to deliver outcomes was almost<br />
unheard of. The arrival of cloud data analytics<br />
changed all that, with many business leaders<br />
now counting on data to inform real-time<br />
decisions and maintain relevance in the market.<br />
The evolution of modern data analytics means<br />
organisations now have the right ingredients to<br />
deliver meaningful improvements to businesses,<br />
but managing the complexity and volume of<br />
data they produce requires very specific tools.<br />
Right now those tools aren't up to the task.<br />
Our research suggests three quarters of UK<br />
data professionals believe outdated and<br />
inefficient data integration processes are<br />
wasting business resources and hampering<br />
productivity. Despite the boom in cloud<br />
investment, the reality is that most organisations<br />
are grappling with legacy tools and struggling<br />
to deliver meaningful insights as a result. In the<br />
context of an ongoing data talent war, if this<br />
failure to adapt technology offerings to meet<br />
the needs of the workforce persists, it could<br />
make the situation untenable.<br />
So, what is the solution? For businesses aiming<br />
to take advantage of the scale and performance<br />
benefits of the cloud, a modern cloud data<br />
stack has a pivotal part to play. Adopting this<br />
approach starts with considering the challenges<br />
that can present barriers to data engineers in<br />
their quest to deliver transformation:<br />
The "Three Vs" of data pools: As modern<br />
data evolves, it grows in volume, variety,<br />
and velocity. Assessing these metrics is key<br />
to understanding how big data can be<br />
measured, yet the complexity involved can<br />
often hinder data migration efforts.<br />
War for data talent: As demand for tech<br />
skills soars, organisations clearly recognise<br />
the value of big data to boost innovation<br />
and the bottom line. Having the talent to<br />
act on it is another conversation, however.<br />
Nearly half (46 per cent) of businesses have<br />
struggled to recruit for data roles over the<br />
last two years, according to the DCMS.<br />
Legacy data management: Outdated data<br />
tools and process could be costing<br />
organisations up to £32.5 million a year,<br />
according to McKinsey estimates. The<br />
subsequent cascading impacts of inefficient<br />
data maintenance can be felt companywide,<br />
ultimately making data<br />
democratisation more difficult to achieve.<br />
CLOUD DATA ANALYTICS<br />
A business' ability to overcome these issues<br />
depends on how effectively teams can implement<br />
a modern cloud data stack. Data teams, unable<br />
to realise the full power of cloud data analytics,<br />
tend to be restrained by manual integration and<br />
therefore deprived of time. Strategic and<br />
analytical work to prioritise their data needs<br />
however can help data engineers benefit from<br />
enhanced automation, and transform their raw<br />
data into analytics-ready data.<br />
The "Three Vs" of data can then be better<br />
managed if it is refined as quickly as possible<br />
once generated, opening up vast data sets to<br />
immediate business application. Streamlining the<br />
data integration process in this way empowers<br />
typically overloaded data teams to deliver critical<br />
insights much faster than previously.<br />
As business leaders try to tackle the data skills<br />
gap, they need to rethink how they can<br />
accommodate the needs and nurture the<br />
capabilities of the workforce. Deploying lowcode<br />
and no-code interfaces is another route<br />
to improving data democratisation from the<br />
bottom up. Typically with little knowledge of<br />
programming, business users need to quickly<br />
tap into key business insights with minimal effort<br />
to progress their analytics projects. Such an<br />
approach makes data accessible and usable<br />
for the wider team and allows data engineers to<br />
reallocate time to taking advantage of what the<br />
cloud has to offer.<br />
To truly keep pace with the paradigms of the<br />
cloud and data needs of the enterprise though,<br />
a modern cloud data strategy, underpinned by<br />
a single cloud platform, merits consideration.<br />
For some time, legacy Extraction,<br />
Transformation, and Loading (ETL) processes<br />
for data have been rigid, time-consuming, and<br />
simply incapable of managing the new,<br />
unprecedented volume of data. Yet, modern<br />
ELT processes - taking place in the cloud - are<br />
much more agile and can help teams across<br />
organisations ingest data and make strategic<br />
decisions at speed.<br />
THE COLLECTIVE BENEFIT<br />
The evolution of the modern data fabric<br />
shows no sign of slowing down. Yet the<br />
increasing volume, complexity, and speed at<br />
which business's data footprints are growing<br />
means a shift towards a modern cloud data<br />
stack is imminent.<br />
An influx of unstructured data requires<br />
seamless management, automation, and<br />
analysis if organisations are to extract and<br />
operationalise insights. The workforce should<br />
be equipped with the processes to leverage<br />
data more easily and effectively if businesses<br />
are to improve productivity and allow the<br />
wider organisation to benefit from collective<br />
insight. <strong>NC</strong><br />
26 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
PRODUCT REVIEW<br />
Progress WhatsUp<br />
Gold <strong>2022</strong><br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
In the world of network monitoring, WhatsUp<br />
Gold (WUG) has a remarkable track record<br />
going back to the early 1990s. It's easy to<br />
see why as it has consistently offered an<br />
unbeatable range of monitoring tools ideally<br />
suited to SMBs and enterprises. Not content to<br />
rest on its laurels, Progress has implemented a<br />
vigorous development program and the latest<br />
WUG <strong>2022</strong> adds even more valuable features.<br />
Centre stage is support for the Progress<br />
Loadmaster and Flowmon appliances as WUG<br />
<strong>2022</strong> can discover and monitor them.<br />
Alerting gets a boost as it can now send<br />
notifications to Microsoft Teams groups and<br />
users. Access security is even tighter, as the<br />
WUG dashboards offer new customisation<br />
features for greater visibility and the log<br />
management service provides regulatory<br />
compliant archiving.<br />
Progress offers flexible licensing options with<br />
the Premium edition available on device-based<br />
yearly subscriptions or with a perpetual license.<br />
An alternative is points-based licensing where<br />
each device, regardless of hardware<br />
components, costs one point while NetFlow<br />
data sources or monitored applications cost<br />
ten points each.<br />
The Premium edition includes core features<br />
such as discovery, interactive mapping, alerting<br />
and reporting plus cloud, wireless network and<br />
storage monitoring. The optional add-on<br />
modules can be purchased separately while<br />
the Total Plus version includes them all, and<br />
smaller businesses will love the new free<br />
edition which includes a perpetual 20 points of<br />
monitoring goodness.<br />
Installation on a Windows Server 2019 host<br />
took 30 minutes and discovery is also swift. A<br />
wizard helped conjure up the first one and<br />
after we'd added all our credentials, it reported<br />
back in 10 minutes with a complete list of all<br />
our network devices. The WUG web console is<br />
a pleasure to use as it's simple to navigate with<br />
only four main options in its upper menu<br />
ribbon. We could easily create custom network<br />
discoveries, pull up network topology views,<br />
swap to a network map and create custom<br />
analysis dashboards.<br />
The Analyse tab provides deep insights into<br />
device status with the home dashboard<br />
presenting a real-time graphical network<br />
overview along with predefined tabs showing<br />
the top 10 busiest devices, actions, critical<br />
errors and storage status. You can add more<br />
tabs as required and increase the number of<br />
columns, making it easy to create your perfect<br />
NOC (network operations centre) views.<br />
We run the Progress VMware Flowmon<br />
Collector appliance in the lab for application<br />
security and anomaly detection, and after<br />
adding SNMP and REST API credentials,<br />
WUG discovered and correctly identified it<br />
by assigning a special Flowmon icon to it.<br />
The Analyse tab also has a new option for<br />
accessing dashboards and events for<br />
Flowmon appliances. We could view details<br />
such as total traffic, packets, responses and<br />
flows for areas such as users, QoS/ToS, mail,<br />
services and so on. The Home dashboards<br />
offer seven reports specifically for Flowmon<br />
data so you can quickly add these graphs to<br />
NOC views.<br />
WUG provides great alerting features and<br />
uses policies to link device state changes with<br />
a range of actions including running a<br />
program, restarting a service, sending emails<br />
and posting alerts. A Post to MS Teams is<br />
provided in the actions menu, and we had no<br />
problems adding our account using the Teams<br />
Incoming Webhook connector and<br />
customising the example JSON template to<br />
add specific details in the alert messages we<br />
wanted sent out.<br />
WhatsUp Gold <strong>2022</strong> offers a remarkable<br />
range of network monitoring tools and its<br />
smart dashboard is clearly capable of<br />
presenting a wealth of valuable information<br />
about your network. It's easy to deploy and<br />
use, the flexible licensing options make it very<br />
affordable and the seamless integration with<br />
LoadMaster and Flowmon appliances makes it<br />
even more appealing. <strong>NC</strong><br />
Product: WhatsUp Gold <strong>2022</strong><br />
Supplier: Progress Software Ltd<br />
Tel: +44 (0)1344 360444<br />
Web site: www.whatsupgold.com<br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 27
OPINION: CYBER RESILIE<strong>NC</strong>E<br />
STRENGTHENING THE UK'S CYBERSECURITY RESILIE<strong>NC</strong>E<br />
NEW LAWS ARE BEING PROPOSED BY THE UK GOVERNMENT TO DRIVE SECURITY STANDARDS IN<br />
OUTSOURCED IT SERVICES USED BY ALMOST ALL UK BUSINESSES<br />
The proposed laws come in the wake<br />
of recent high profile cyber attacks<br />
targeting SolarWinds and Microsoft<br />
Exchange Servers, which highlighted<br />
vulnerabilities in third-party products and<br />
services which can be exploited by<br />
cybercriminals. Mike Foster, Channel<br />
Manager, VIPRE explains how these laws<br />
will affect the channel market and help to<br />
strengthen the country's cyber resilience,<br />
with MSPs taking on a more important<br />
trusted advisor role than ever before.<br />
THE ROLE OF THE TRUSTED<br />
ADVISOR<br />
Since 2018, Network and Information<br />
Systems (NIS) Regulations have been in<br />
force to improve the cybersecurity of<br />
companies which provide essential<br />
services, such as water, energy, transport,<br />
healthcare and digital infrastructure. These<br />
regulations require such businesses to<br />
undertake risk assessments, put in place<br />
reasonable security measures to protect<br />
their network, and report any significant<br />
incidents whilst having plans in place to<br />
recover if an attack occurs. Those who fail<br />
to implement effective cybersecurity<br />
measures can be fined as much as £17<br />
million. However, the government now<br />
wants to widen the list of companies that<br />
comply with such measures to include<br />
Managed Service Providers (MSPs).<br />
With more businesses undergoing digital<br />
transformations and shifting to the cloud,<br />
which was accelerated over the pandemic<br />
as a means to survive, there has been an<br />
increase in dependence on MSPs to act as<br />
a business' trusted advisor to assist them<br />
on their digital journey. These IT partners<br />
are also crucial in boosting the growth of<br />
the country's £150.6 billion digital sector,<br />
and therefore play a monumental role in<br />
the economy.<br />
Outsourced IT<br />
services<br />
should<br />
create a<br />
solid<br />
cyber<br />
security strategy for the businesses who<br />
choose them. Security standards should<br />
therefore be high - especially to battle the<br />
ever-developing and innovative<br />
cybersecurity market, with new<br />
methodology and tactics constantly<br />
evolving from hackers. As highlighted in the<br />
Government's recent announcement: "Every<br />
UK organisation must take their cyber<br />
resilience seriously as we strive to grow,<br />
innovate and protect people<br />
online. Additionally,<br />
outsourced IT<br />
providers have<br />
the<br />
28 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION: CYBER RESILIE<strong>NC</strong>E<br />
knowledge, skills and solutions for<br />
businesses to benefit from and leverage to<br />
keep their data, networks and users safe.<br />
By partnering with an established MSP<br />
who can act as an external security partner<br />
to help businesses achieve cyber resilience,<br />
the pressure and responsibility of defending<br />
the business against cyber threats will lay<br />
with the expert. This creates a unique<br />
opportunity for MSPs to guide customers on<br />
their cybersecurity journey and ensure they<br />
are receiving relevant education and have<br />
the right technology and tools in place to<br />
protect their businesses. By identifying the<br />
gaps in their cyber needs, or allowing an<br />
MSP to make these judgments, a strong<br />
infrastructure can be built upon the<br />
business' existing setup.<br />
REPORTING I<strong>NC</strong>IDENTS AND<br />
DAMAGE LIMITATION<br />
Other published proposals include<br />
improving the way organisations report<br />
cybersecurity incidents and reforming<br />
legislation so that it is more flexible and<br />
can react to the speed of technological<br />
change. This is specifically timely due to the<br />
increase in ransomware attacks, particularly<br />
during the peak of COVID-19, which saw<br />
twice as many ransomware attacks occur -<br />
taking advantage of remote workers being<br />
away from the help of IT teams, and of the<br />
businesses that pay the ransom fee, such as<br />
in the Colonial Pipeline attack, where the<br />
cybercriminal group DarkSide were paid<br />
nearly $5m (£3.6m) in ransom.<br />
If a ransomware attack were to take<br />
place, it is important that the organisation<br />
works with local authorities to try to rectify<br />
the issue and follow their guidance. Often,<br />
many ransomware attacks go unreported -<br />
and this is where a lot of criminal power<br />
lies. Prevention is always better than cure,<br />
and damage limitation and containment<br />
are important right from the outset. Most<br />
organisations should have a detailed<br />
disaster recovery plan in place and if they<br />
don't, they should rectify this immediately.<br />
The key to every disaster recovery plan is<br />
backups. Once the breach has been<br />
contained, businesses can get back up and<br />
running quickly and relatively easily,<br />
allowing for maximum business continuity.<br />
As soon as the main threat has passed, it<br />
is recommended that all organisations<br />
conduct a full retrospective audit, ideally<br />
without blame or scapegoats, and share<br />
their findings and steps taken with the<br />
world. Full disclosure is helpful - not only<br />
for customer, client or patient reassurances,<br />
but also for other organisations to<br />
understand how they can prevent an attack<br />
of this type being successful again.<br />
EQUIPPING BUSINESSES ON THEIR<br />
CYBERSECURITY JOURNEY<br />
The UK Cyber Security Council, which<br />
regulates the cybersecurity profession, also<br />
needs powers to raise the bar and create a<br />
set of agreed qualifications and<br />
certifications so those working in<br />
cybersecurity can prove they are properly<br />
equipped to protect businesses online.<br />
With security breaches showing no signs<br />
of slowing down, MSPs must be constantly<br />
vigilant and develop cyber resilience<br />
approaches that go beyond deploying<br />
security solutions. This means having not<br />
only the market-leading technology<br />
available, but also the technical expertise<br />
to support business security plans and<br />
growth. MSPs must take a proactive role in<br />
understanding the current state of a<br />
customer's ability to protect against, prevent<br />
and respond to modern cyber threats<br />
when recommending the best<br />
approaches to true cyber resilience.<br />
Have they engaged in phishing<br />
penetration testing? Is sending an<br />
email to the wrong person an<br />
embarrassing mistake or a data<br />
breach? Are they using a<br />
layered and dedicated security approach or<br />
settling for security as part of a broader<br />
'cloud services' package? These are just<br />
some of the key questions MSPs should be<br />
asking when they look to fulfil their trusted<br />
advisor role.<br />
CO<strong>NC</strong>LUSION<br />
MSPs have privileged access to their<br />
client's networks and systems, potentially<br />
enabling attackers to attack a wide range<br />
of organisations through a single breach.<br />
This is why it's of the utmost importance<br />
for all outsourced IT providers to<br />
understand the role they play in keeping<br />
business data secure, while also educating<br />
their customers on how to become more<br />
cyber resilient. Combining MSP<br />
knowledge and expertise with<br />
government-backed credentials should<br />
surely be a winning formula for the IT<br />
security industry and enable MSPs to<br />
prove to their clients they have what it<br />
takes to keep their businesses secure. <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 29
EVENT ORGANISERS:<br />
Do you have something coming up that may<br />
interest readers of Network Computing?<br />
Contact dave.bonner@btc.co.uk<br />
FORTHCOMING EVENTS<br />
FORTHCOMING EVENTS<br />
<strong>2022</strong><br />
FORTHCOMING EVENTS<br />
21<br />
JUN<br />
23<br />
JUN<br />
12<br />
JUL<br />
CIO/CISO DACH SUMMIT<br />
Frankfurt Germany<br />
https://bit.ly/3tkTd96<br />
NETWORK COMPUTING<br />
AWARDS DINNER<br />
London<br />
www.networkcomputingawards.co.uk<br />
CIO/CISO IRELAND SUMMIT<br />
Dublin, Ireland<br />
https://bit.ly/3P0NdLE
PRODUCT REVIEW<br />
Fluke Networks<br />
FiberLert<br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
Fibre cabling is by far and away the<br />
predominant choice for connecting highperformance<br />
networks and is used for<br />
core networks and backbone connections by<br />
data centres, data communications providers,<br />
campus networks and much more.<br />
With fibre networks carrying so much<br />
critical data it is imperative that fibre cabling<br />
is kept in tip-top condition and that faults<br />
are identified quickly to avoid major<br />
downtime and loss of services. Often, the<br />
biggest problems facing network engineers<br />
are broken or sub-standard cabling, dirty<br />
cable connections, faulty transceivers and<br />
failed ports.<br />
The FiberLert from Fluke Networks is an<br />
elegantly simple and eminently safe testing<br />
solution that is designed to detect active fibre<br />
signals, allowing it to be used to troubleshoot<br />
switch and host ports, transceivers, cables and<br />
polarity. It detects active signals in singlemode<br />
and multimode fibre with an infrared<br />
range of 850nm to 1625nm and can be used<br />
for ports and patch cords, SM, MM, UPC and<br />
APC connections.<br />
It will appeal to network engineers that only<br />
have an occasional requirement to test fibre<br />
connections and don't want to make a big<br />
investment. The FiberLert is compact, easily<br />
portable, incredibly simple to use and with a<br />
price tag that's only a shade over £100, is<br />
exceedingly good value.<br />
This Sharpie-sized tool is constructed of<br />
sturdy impact resistant plastic and has a solid<br />
pocket clip. It's powered by two AAA batteries<br />
which are easily accessible by releasing and<br />
sliding the yellow cover backwards.<br />
The FiberLert is designed for one-hand use<br />
and has a single button on its upper surface<br />
where one quick press turns it on and a two<br />
second press mutes or enables its internal<br />
beeper. It'll conserve battery life if you forget<br />
to turn it off as after five minutes of no<br />
inactivity, it powers itself off.<br />
The business end has a single ceramic<br />
ferrule and its non-contact design reduces<br />
the likelihood of contamination or<br />
damage. To test a transceiver, you just hold<br />
it in front of its ports and it'll tell you if it<br />
detects a signal.<br />
Likewise with fibre cabling terminals, as the<br />
FiberLert's tethered protective cap has a<br />
ferrule adapter below where you place one<br />
end over the FiberLert's detector and plug the<br />
cable ferrule into the other side to ensure<br />
perfect alignment. The FiberLert really is a<br />
cinch to use as when turned on, its smart<br />
LightBeat feature flashes the single red LED in<br />
front of the button to confirm it is powered on<br />
and battery life is good.<br />
When it detects an infra-red light source<br />
from the device or cable under test, the<br />
LED turns solid red and the beeper sounds<br />
continuously. There's nothing to set up,<br />
read or interpret - there's either a signal or<br />
there isn't.<br />
We used it to test a range of lab equipment<br />
including our TP-Link TL-SX3016F core switch<br />
which provides sixteen SFP+ 10GbE ports.<br />
With transceivers inserted, we moved the<br />
FiberLert probe within a few millimetres of the<br />
ports on test and it immediately confirmed<br />
which one was presenting a signal.<br />
It proved invaluable to us as we'd recently<br />
been experiencing connectivity issues<br />
between one of our 10GbE-enabled servers<br />
and the switch. We confirmed that the server's<br />
transceiver was functional, used the<br />
FiberLert's ferrule adapter to verify a signal<br />
was passing through the cable and that<br />
polarity was correct, and then found that the<br />
transceiver in the switch was faulty - all in less<br />
than a minute.<br />
The Fluke Network FiberLert takes all the<br />
guesswork out of troubleshooting fibre<br />
activity, polarity and connectivity. It's very<br />
affordable and we found it so simple to use -<br />
right-thinking network engineers won't leave<br />
home without it. <strong>NC</strong><br />
Product: FiberLert<br />
Supplier: Fluke Networks<br />
Web site: www.flukenetworks.com<br />
Tel: +44 (0)207 942 0721<br />
Price: £101 exc VAT<br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 31
OPINION: DATA CENTRES<br />
THE DATA CENTRE IN <strong>2022</strong> AND BEYOND<br />
THE TIMES THEY ARE A-CHANGIN' FOR THE DATA CENTRE,<br />
ACCORDING TO PETER MILLER, SALES MANAGER AT ETB<br />
TECHNOLOGIES<br />
We live in an ever-changing, datahungry<br />
world - and IT and data<br />
centre managers need to ensure<br />
their set-up is fit for purpose, especially with<br />
the changing nature of work accelerated by<br />
the pandemic. These managers need to<br />
question whether their existing estates meet<br />
the businesses' needs both now and in<br />
preparation for any future challenges<br />
caused by external forces - be it regulatory<br />
or another unprecedented global crisis.<br />
One side-effect of the pandemic was a<br />
reallocation of budgets as businesses had<br />
to rethink their physical office and IT<br />
needs. According to data from Synergy<br />
Research Group, cloud spend in 2020<br />
"dwarfed" investment in on-premise<br />
solutions, growing by 35% to reach almost<br />
$130 billion versus just $90 billion for data<br />
centres. However, as offices reopen and<br />
the way we work changes once again, it is<br />
possible that budgets will again change<br />
and on-premise infrastructure will increase<br />
in <strong>2022</strong> in beyond.<br />
With no crystal ball at hand to see exactly<br />
what will change about business operating<br />
models, it seems like ensuring IT estates are<br />
fit for the future is a lost cause; however<br />
there are some things to consider that will<br />
help - whatever changes come our way.<br />
COMMIT TO A FULL REVIEW<br />
Reopening offices doesn't mean returning to<br />
the way things were in 2019. Many<br />
businesses will maintain a hybrid working<br />
model, so what worked before businesses<br />
went remote doesn't necessarily mean it will<br />
work as we return.<br />
A hybrid model means a high level of<br />
traffic as team members access and save<br />
files from multiple locations. IT managers<br />
must ensure their estate can cope with this,<br />
and consider where adaptations and<br />
improvements might be needed, specifically<br />
concerning storage capacity, networking<br />
capabilities, and connectivity and<br />
bandwidth. This is particularly important as<br />
we continue to see employees use online<br />
collaboration tools like Microsoft Teams to<br />
edit documents in real-time, as well as<br />
access internal servers.<br />
Part of this review should involve a<br />
consultation with the wider organisation to<br />
better understand the company's full IT<br />
usage. Reviewing the tools, processes and<br />
practices that occur at all levels will better<br />
inform the technical team of any<br />
enhancements that are needed within an<br />
organisation's data centre - and beyond.<br />
Only once this has been done can changes<br />
be made to strengthen the data centre and<br />
make it fit for purpose in the future.<br />
BUILDING IN FLEXIBILITY<br />
If the pandemic has taught us nothing else,<br />
it's that we need systems and processes in<br />
place that can be turned on and off when<br />
our technology and operations requirements<br />
change - potentially overnight. While this<br />
was most obvious in March 2020, no one<br />
could have envisaged then that it would be<br />
two years until we considered returning to<br />
the office again. As a result, we all know<br />
now that embedding flexibility within data<br />
centre architectures to scale up (or down)<br />
according to the current organisational<br />
needs is an absolute must.<br />
Achieving this requires planning: not just<br />
consideration of what's needed right now,<br />
32 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION: DATA CENTRES<br />
but also allowing flexibility for extra<br />
capacity down the line. That's not to say<br />
that IT managers should automatically<br />
spend their budget on the biggest capacity<br />
system - but they should be looking for an<br />
upgrade-friendly configuration. For<br />
example, half populating a server's<br />
memory slots with 32GB Dimms may be<br />
more prudent than completely filling them<br />
with 16GB Dimms.<br />
Another example would be purchasing a<br />
48-port switch over a 24-port switch. The<br />
former option provides the additional<br />
ports to use if required; the latter would<br />
require an additional switch. Taking all<br />
this into account will ensure the IT estate<br />
has the flexibility embedded from the<br />
outset to futureproof, which may also<br />
mean budgets are better managed.<br />
Consideration for data migration must<br />
also be top of mind for IT managers. Due<br />
process must be given while a migration is<br />
happening, with temporary solutions in<br />
place to limit downtime. This is where<br />
utilising refurbished enterprise IT<br />
equipment can help. Rather than<br />
following an "invest-to-upgrade" strategy,<br />
companies may choose to rent the<br />
equipment that's needed on a short-term<br />
basis until the migration is complete.<br />
There are several companies, including<br />
ETB, that can help organisations of all<br />
shapes and sizes source this stopgap,<br />
enabling them to continue operations<br />
until the migration is complete<br />
BYPASS SUPPLY ISSUES BY BUYING<br />
REFURB<br />
The refurb market can also help in<br />
addressing the current supply chain crisis.<br />
Delivery staff shortages combined with a<br />
global semiconductor shortage means<br />
some businesses are waiting up to 100<br />
days for brand new servers and<br />
networking equipment. For many business,<br />
IT requirements change far too quickly to<br />
accept waiting more than three months for<br />
a piece of kit.<br />
More and more organisations are<br />
considering alternative routes to get the<br />
equipment they need, with many seriously<br />
considering refurbished enterprise IT<br />
equipment for the first time. Gone are the<br />
days when refurbished equated to old and<br />
slow; indeed, even equipment that is just<br />
one generation older than its "brand new<br />
equivalent" can often be used for as long<br />
as its newer peer, with the added benefit<br />
of providing significant cost savings.<br />
Equally, the refurb market also presents a<br />
stronger opportunity for spare or<br />
replacement parts to be sourced in a short<br />
amount of time - sometimes seeing<br />
processing and shipping times cut by 10x<br />
than buying new.<br />
The opportunity to upgrade equipment is<br />
also greater when it comes to refurbished<br />
tech, as specs can be adapted to better<br />
suit the user. All this means that businesses<br />
can reinvest any savings in other areas of<br />
the IT estate or business to drive recovery<br />
or mitigate any impact from rising costs<br />
resulting from changes to inflation.<br />
Put simply, when it comes to the data<br />
centre this year and beyond, speed, flex<br />
and source of technology must be high on<br />
the agenda to make sure organisations<br />
have a data centre to meet their needs -<br />
both now and in the future. <strong>NC</strong><br />
WWW.NETWORKCOMPUTING.CO.UK @<strong>NC</strong>MagAndAwards<br />
MAY/JUNE <strong>2022</strong> NETWORKcomputing 33
OPINION: HYBRID WORKING<br />
A RESILIENT APPROACH TO HYBRID<br />
WORKING<br />
HYBRID WORKING PRESENTS A NUMBER OF SECURITY<br />
CHALLENGES FOR IT TEAMS. RODOLPHE HARAND, VP OF<br />
SALES AT YESWEHACK, LOOKS AT HOW TO ADDRESS THEM<br />
During the first lockdown, 60% of UK<br />
employees worked remotely. Now<br />
as offices reopen, many businesses<br />
find themselves continuing to support<br />
remote working while encouraging staff to<br />
come in a couple of days a week.<br />
With British workers favouring remote<br />
working according to a recent YouGov poll,<br />
rather than an all or nothing approach,<br />
companies are adopting a hybrid working<br />
approach. Although beneficial for<br />
employees, hybrid working is placing<br />
pressure onto business leaders to achieve a<br />
balance between providing staff with<br />
increased flexibility while also contending<br />
with a host of security issues arising from<br />
having a distributed workforce.<br />
PUBLIC NETWORK CHALLENGE<br />
Even before the pandemic, the<br />
safeguarding of corporate networks was<br />
a high priority for IT teams. Now, with the<br />
rise of hybrid working, IT team concerns<br />
have only amplified as more employees<br />
are using unsecured public Wi-Fi<br />
networks in places such as coffee shops,<br />
hotels and libraries.<br />
While this increased flexibility is great for<br />
employees, it raises a challenge for<br />
organisations as they have little visibility on<br />
the security standards of these networks.<br />
Knowing this, cybercriminals are setting up<br />
routers in public places. Once an<br />
unsuspecting employee connects to one of<br />
these routers, the cybercriminal has access<br />
to their communications and can infiltrate a<br />
business' corporate assets.<br />
Breaching a public network is a far easier<br />
task for hackers than intercepting a wellprotected<br />
company network. Think of it as a<br />
criminal having multiple doors to breach a<br />
premises, rather than one well-reinforced<br />
front door. The easiest solution to tackle this<br />
problem is mandating that employees use a<br />
Virtual Private Network (VPN). Using VPNs<br />
before signing onto a public network will<br />
encrypt the employee's internet traffic and<br />
flag any infractions on the corporate network.<br />
SOCIAL ENGINEERING ATTACKS<br />
INTENSIFY<br />
In 2021, online fraud increased by 85%<br />
according to a report by software company<br />
Arkose Lab. The pandemic has also resulted<br />
in a significant rise in social engineering<br />
attacks, the act of exploiting human<br />
interactions to trick individuals into sharing<br />
sensitive data. An example of this is phishing,<br />
where someone may receive an email<br />
supposedly from the IT team asking them to<br />
share their log-in details. Working remotely<br />
increases the likelihood of being susceptible<br />
to social engineering attacks as they rely<br />
heavily on human error and manipulation.<br />
Contributing to this is our increasing<br />
reliance on digital communications. For<br />
example, a new employee who is<br />
onboarded remotely is less likely to be able<br />
to identify legitimate correspondence<br />
coming from within the business and more<br />
prone to a cybercriminal's phishing email.<br />
For IT teams, while anti-spam filters are a<br />
good start, the key to success is enacting<br />
cybersecurity policies and standards of<br />
behaviour for all staff to follow, including<br />
those working from remote locations. Part<br />
of this means encouraging employees to<br />
question the source of emails, investigate<br />
irregularities and take the time to check<br />
with others on communications they are<br />
unsure about.<br />
ELIMINATING POOR CYBER<br />
SECURITY HYGIENE<br />
Another key factor businesses should<br />
consider is the behavioural difference<br />
between employees working from home<br />
and the office. Employees are more<br />
inclined to partake in risky online activity<br />
when working remotely as they don't have<br />
the eyes of the IT department directly on<br />
them. As a result, cybersecurity measures<br />
are more likely to be contravened.<br />
When it comes to cybersecurity, it is<br />
ultimately your employees who are first and<br />
foremost the strongest line of defence. It's<br />
for this reason that organisations must<br />
continuously invest in cyber awareness<br />
training while also providing tools that<br />
support secure remote working.<br />
No matter how advanced the<br />
deployment of your latest cybersecurity<br />
tools are, if the right training is not<br />
provided in the first place your defences<br />
are already compromised. As hybrid<br />
working becomes the new normal, IT<br />
security teams must rise to the challenge<br />
of preventing and combating the<br />
associated security implications as in the<br />
end, strong cyber resilience equates to<br />
strong business resilience. <strong>NC</strong><br />
34 NETWORKcomputing MAY/JUNE <strong>2022</strong> @<strong>NC</strong>MagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
SUPERMICRO<br />
Edge Building Blocks<br />
Accelerating Innovation at the Intelligent Edge with the Broadest Range of Systems<br />
for Any Environment, Featuring 3 rd Gen Intel® Xeon® Scalable processors<br />
Learn more at www.supermicro.com<br />
© Supermicro and Supermicro logo are trademarks of Super Micro Computer, Inc. in the U.S. and/or other countries.