You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
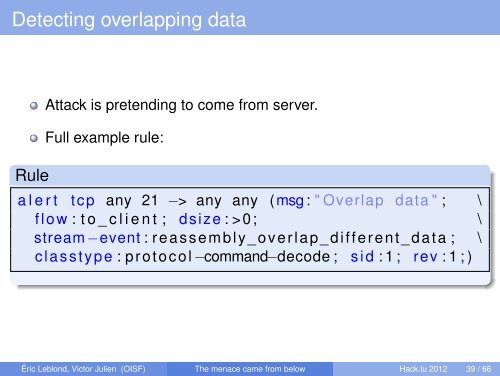
Detecting overlapping data<br />
Rule<br />
Attack is pretending to come <strong>from</strong> server.<br />
Full example rule:<br />
a l e r t tcp any 21 −> any any (msg : " Overlap data " ; \<br />
flow : t o _ c l i e n t ; dsize : >0; \<br />
stream −event : reassembly_overlap_different_data ; \<br />
classtype : protocol −command−decode ; s i d : 1 ; rev : 1 ; )<br />
Éric Leblond, Victor Julien (OISF) <strong>The</strong> <strong>menace</strong> <strong>came</strong> <strong>from</strong> <strong>below</strong> <strong>Hack</strong>.<strong>lu</strong> 2012 39 / 66