- Page 2 and 3:
Table of Contents | Index Core Pyth
- Page 4 and 5:
The Complete Developer's Guide to P
- Page 6 and 7:
Table of Contents | Index Copyright
- Page 8 and 9:
Section 6.2. Strings Section 6.3. S
- Page 10 and 11:
Section 11.5. Formal Arguments Sect
- Page 12 and 13:
Section 19.4. Brief Tour of Other G
- Page 14 and 15:
Copyright Many of the designations
- Page 16 and 17:
Praise for Core Python Programming
- Page 18 and 19:
Prentice Hall Core Series Core J2EE
- Page 20 and 21:
Another set of first edition reader
- Page 22 and 23:
We will continue to update the book
- Page 24 and 25:
Dictionaries are Python's mapping o
- Page 26 and 27:
and you will find it fun! We first
- Page 28 and 29:
Acknowledgments Acknowledgments for
- Page 30 and 31:
Christian Tismer (creator of Stackl
- Page 32 and 33:
Chapter 1. Welcome to Python! Chapt
- Page 34 and 35:
1.2. Origins Work on Python began i
- Page 36 and 37:
which you can build an application,
- Page 38 and 39:
often provides an extended distract
- Page 40 and 41:
Build It Yourself For most other pl
- Page 42 and 43:
Windows/DOS To add Python to your s
- Page 44 and 45:
It is also possible in Unix to auto
- Page 46 and 47:
MacOS X is very Unix-like (based on
- Page 48 and 49:
Figure 1-5. Starting IDLE in Window
- Page 50 and 51:
1.6. Python Documentation Python do
- Page 52 and 53:
orrow features from languages such
- Page 54 and 55:
1.8. Other Implementations The "sta
- Page 56 and 57:
1.9. Exercises 1-1. Python Installa
- Page 58 and 59:
abs(4) 4 >>> abs(-4) 4 We will intr
- Page 60 and 61:
%s means to substitute a string whi
- Page 62 and 63:
It's very tempting for beginners to
- Page 64 and 65:
2.4. Operators The standard mathema
- Page 66 and 67:
2.5. Variables and Assignment Rules
- Page 68 and 69:
All numeric types are covered in Ch
- Page 70 and 71:
2.8. Lists and Tuples Lists and tup
- Page 72 and 73:
2.10. Code Blocks Use Indentation C
- Page 74 and 75:
2.12. while Loop The standard while
- Page 76 and 77:
Using the string format operator al
- Page 78 and 79:
2.14. List Comprehensions These are
- Page 80 and 81:
case you would have to revert back
- Page 82 and 83:
2.17. Functions Like many other lan
- Page 84 and 85:
2.18. Classes Classes are a core pa
- Page 87 and 88:
2.19. Modules A module is a logical
- Page 89 and 90:
2.20. Useful Functions In this chap
- Page 91 and 92:
2-4. User Input with raw_input(). a
- Page 93 and 94:
put in your own as you write your c
- Page 95 and 96:
Chapter 3. Python Basics Chapter To
- Page 97 and 98:
3.1.3. Multiple Statement Groups as
- Page 99 and 100:
3.2. Variable Assignment This secti
- Page 101:
Another way of assigning multiple v
- Page 104 and 105:
[a] access keyword obsoleted as of
- Page 106 and 107:
three PEPs: 7 (Style Guide for C Co
- Page 108 and 109:
3. Module imports Import all the mo
- Page 110 and 111:
Tests in the main body are an easy
- Page 112 and 113:
As responsible programmers, we are
- Page 114 and 115:
● It is explicitly removed from a
- Page 116 and 117:
Lines 13 The Unix startup line is f
- Page 118 and 119:
1 #!/usr/bin/env python 2 3 'readTe
- Page 120 and 121:
3.7. Related Modules/Developer Tool
- Page 122 and 123:
3-10. Exceptions. Replace the call
- Page 124 and 125:
4.1. Python Objects Python uses the
- Page 126 and 127:
4.3. Other Built-in Types ● Type
- Page 128 and 129:
4.4. Internal Types ● Code ● Fr
- Page 130 and 131:
4.5. Standard Type Operators 4.5.1.
- Page 132 and 133:
Example 2: foo1 and foo2 reference
- Page 134 and 135:
4.5.3. Boolean In the above example
- Page 136 and 137:
4.6. Standard Type Built-in Functio
- Page 138 and 139:
str(2e10) '20000000000.0' >>> >>> s
- Page 140 and 141:
>>> type(foo) # assumes foo instant
- Page 142 and 143:
then we do not even need to check b
- Page 144 and 145:
4.7. Type Factory Functions Since P
- Page 146 and 147:
Another way of categorizing the sta
- Page 148:
Sequence types are those whose elem
- Page 151 and 152:
4.10. Exercises 4-1. Python Objects
- Page 153 and 154:
Chapter 5. Numbers Chapter Topics
- Page 155 and 156:
Okay, now that you have a good idea
- Page 157 and 158:
Core Style: Use uppercase "L" with
- Page 159 and 160:
5.3. Double Precision Floating Poin
- Page 161 and 162:
aComplex.real -8.333 >>> aComplex.i
- Page 163 and 164:
Automatic numeric coercion makes li
- Page 165 and 166:
True Division This is where divisio
- Page 167 and 168:
see that the unary operator binds m
- Page 169 and 170:
Bitwise Operator Function ~num (una
- Page 171 and 172:
In addition, because of the unifica
- Page 173 and 174:
divmod(10,2.5) (4.0, 0.0) >>> divmo
- Page 175 and 176:
floor(-1.2) -2.0 round(-1.2) -1.0 -
- Page 178 and 179:
5.7. Other Numeric Types 5.7.1. Boo
- Page 180 and 181:
cannot "be continued." If we were t
- Page 182 and 183:
uniform() Does almost the same thin
- Page 184 and 185:
5.9. Exercises The exercises in thi
- Page 186 and 187:
Why do we get 134L and not 1342 in
- Page 188 and 189:
Chapter 6. Sequences: Strings, List
- Page 190 and 191:
obj not in seq Tests if obj is not
- Page 192 and 193:
if not provided, or if None is used
- Page 194 and 195:
Extended Slicing with Stride Indice
- Page 196 and 197:
above. 6.1.3. Built-in Functions (B
- Page 198 and 199:
[a] New in Python 2.3. [b] key argu
- Page 200 and 201:
considered a substring. To access s
- Page 202 and 203:
6.3. Strings and Operators 6.3.1. S
- Page 204 and 205:
Notice how the omission of both ind
- Page 206 and 207:
numeric identifier strings that we
- Page 208 and 209:
method (see example below). There i
- Page 210 and 211:
6.4. String-Only Operators 6.4.1. F
- Page 212 and 213:
'6c' >>> >>> "%X" % 108 '6C' >>> >>
- Page 214 and 215:
>>> print s.substitute(lang='Python
- Page 216 and 217:
6.5. Built-in Functions 6.5.1. Stan
- Page 218 and 219:
isinstance() calls to verify type:
- Page 220 and 221:
string.isalpha() [a] , [b] [c] Retu
- Page 222 and 223:
>>> quest.endswith('color?') True >
- Page 224 and 225:
\t 011 9 0x09 HT Horizontal tab \n
- Page 226:
string was created when the operati
- Page 229 and 230:
convert the numeric value of the by
- Page 231 and 232:
Example 6.2. Simple Unicode String
- Page 233 and 234:
Mistake #2: Using the string module
- Page 236 and 237:
6.9. Related Modules Table 6.10 lis
- Page 238:
6.10. Summary of String Highlights
- Page 241 and 242:
How to Update Lists You can update
- Page 243 and 244:
str_list[2] 'over' >>> str_list[:2]
- Page 245:
Traceback (innermost last): File ""
- Page 248 and 249:
3. 4. 5. If elements are of the sam
- Page 250 and 251:
sum(a, 5) 20 >>> a = [6., 4., 5.] >
- Page 252 and 253:
[a] Removes and returns obj at give
- Page 254 and 255:
original list object is left as is,
- Page 256 and 257:
28 while True: 29 while True: 30 tr
- Page 258 and 259:
(Q)uit Enter choice: v You picked:
- Page 260 and 261:
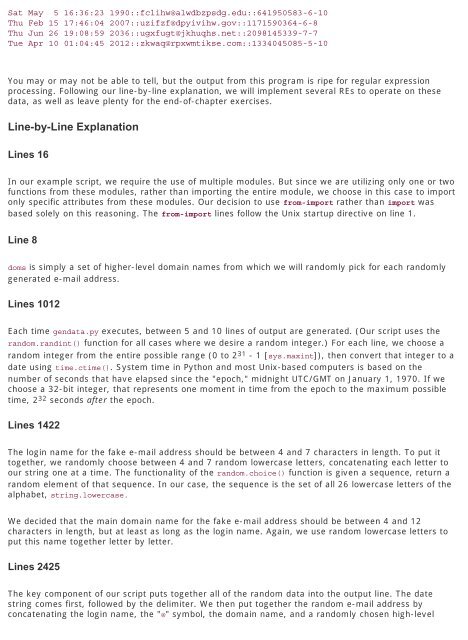
Line-by-Line Explanation Because of
- Page 262 and 263:
6.16. Tuples Tuples are another con
- Page 264 and 265:
6.17. Tuple Operators and Built-in
- Page 266 and 267:
6.18. Special Features of Tuples 6.
- Page 268 and 269:
(4, True, 5) >>> (4, 2) < (3, 5) #
- Page 270 and 271:
6.19. Related Modules Table 6.12 li
- Page 272 and 273:
[id(x) for x in hubby] [9919616, 11
- Page 274 and 275:
6.21. Summary of Sequences Sequence
- Page 276 and 277:
str() • • • strip() • swapc
- Page 278 and 279:
d. Take a string and append a backw
- Page 280 and 281:
6-12. Strings. a. b. c. Create a fu
- Page 282 and 283:
6-19. Multi-Column Output. Given an
- Page 284 and 285:
7.1. Mapping Type: Dictionaries Dic
- Page 286 and 287:
dict2 = {'name': 'earth', 'port': 8
- Page 288 and 289:
dict2['arch'] = 'sunos5' # add new
- Page 290 and 291:
Beginning with Python 2.2, programm
- Page 292 and 293:
size, their keys match, and so do t
- Page 294 and 295:
dict(zip(('x', 'y'), (1, 2))) {'y':
- Page 296 and 297:
7.4. Mapping Type Built-in Methods
- Page 298 and 299:
dict2= {'host':'earth', 'port':80}
- Page 300 and 301:
7.5. Dictionary Keys Dictionary val
- Page 302 and 303:
39 try: 40 choice = raw_input(promp
- Page 304 and 305:
7.6. Set Types In mathematics, a se
- Page 306 and 307:
... print i ... c e h o p s How to
- Page 308 and 309:
superset of the second set (is a su
- Page 310 and 311:
s &= set('shop') >>> s set(['h', 's
- Page 312 and 313:
7.9. Set Type Built-in Methods 7.9.
- Page 314 and 315:
7.10. Operator, Function/Method Sum
- Page 316 and 317:
7.11. Related Modules The sets modu
- Page 318 and 319:
7-5. userpw2.py. The following prob
- Page 320 and 321:
characters in srcstr that are beyon
- Page 322 and 323:
Chapter 8. Conditionals and Loops C
- Page 324 and 325:
8.2. else Statement Like other lang
- Page 326 and 327:
8.3. elif (aka else-if) Statement e
- Page 328:
8.4. Conditional Expressions (aka "
- Page 331 and 332:
One must use caution when using whi
- Page 333 and 334:
Iterating by Sequence Item >>> name
- Page 335 and 336:
ange(start, end, step=1) range() wi
- Page 337 and 338:
are "sequence-related" is that half
- Page 339 and 340:
8.8. continue Statement Core Note:
- Page 341 and 342:
8.10. else Statement ... Take Two I
- Page 343 and 344:
8.11. Iterators and the iter() Func
- Page 345 and 346:
Dictionaries Dictionaries and files
- Page 347 and 348:
8.12. List Comprehensions List comp
- Page 349 and 350:
and split each line up into words,
- Page 351 and 352:
of building up this long list, it w
- Page 353 and 354:
lines)? That way, we can use the ma
- Page 355 and 356:
8.15. Exercises 8-1. Conditionals.
- Page 357 and 358:
8-9. Fibonacci Numbers. The Fibonac
- Page 360 and 361:
Chapter 9. Files and Input/Output C
- Page 362 and 363:
9.2. File Built-in Functions [open(
- Page 364 and 365:
you see references to open(), you c
- Page 366 and 367:
Note that there is no "writeline()"
- Page 368 and 369:
We originally described how this pr
- Page 370 and 371:
f.seek(-12, 1) # move back 12 bytes
- Page 372 and 373:
9.4. File Built-in Attributes File
- Page 374 and 375:
9.6. Command-Line Arguments The sys
- Page 376 and 377:
9.7. File System Access to your fil
- Page 378 and 379:
Separation basename() Remove direct
- Page 380 and 381:
53 print '*** deleting test file' 5
- Page 382 and 383:
to confirm that the directory is in
- Page 384 and 385:
9.8. File Execution Whether we want
- Page 386 and 387:
other external extension modules th
- Page 388 and 389:
9.10. Related Modules There are ple
- Page 390 and 391:
Some other Python modules that gene
- Page 392 and 393:
9-10. Home Finances. Create a home
- Page 394 and 395:
9-15. Copying Files. Prompt for two
- Page 396 and 397:
9-24. File Transfer Between Archive
- Page 398 and 399:
10.1. What Are Exceptions? 10.1.1.
- Page 400 and 401:
10.2. Exceptions in Python As you w
- Page 402 and 403:
our case with the foo (non-)attribu
- Page 404 and 405:
As you can see, our code now runs s
- Page 406 and 407:
etval = None return retval Bear in
- Page 408 and 409:
except (Exc1[, Exc2[, ... ExcN]])[,
- Page 410 and 411:
except Exception, e: # handle real
- Page 412 and 413:
try: ... float(['float() does not',
- Page 414 and 415:
13 log = open('cardlog.txt', 'w') 1
- Page 416 and 417:
determine whether there were defect
- Page 418 and 419:
log.write('no txns this month\n') f
- Page 420 and 421:
10.4. Context Management 10.4.1. wi
- Page 422 and 423:
Now the with_suite executes. When e
- Page 424 and 425:
10.6. Raising Exceptions The interp
- Page 426 and 427:
aise string, args, tb Same as above
- Page 428 and 429:
try: assert 1 == 0, 'One does not e
- Page 430 and 431:
[d] Error in FloatingPointError flo
- Page 432 and 433:
[h] Unicode- UnicodeError related e
- Page 434 and 435:
10.9. *Creating Exceptions Although
- Page 436 and 437:
79 f.close() 80 81 for eachTest in
- Page 438 and 439:
the host's name and the port number
- Page 440 and 441:
10.10. Why Exceptions (Now)? There
- Page 442 and 443:
10.12. Exceptions and the sys Modul
- Page 444 and 445:
10.14. Exercises 10-1. Raising Exce
- Page 446 and 447:
10-9. Improving math.sqrt(). The ma
- Page 448 and 449:
11.1. What Are Functions? Functions
- Page 450 and 451:
Stated Number of Objects to Return
- Page 452 and 453:
Keyword arguments may also be used
- Page 454 and 455:
Line-by-Line Explanation Lines 14 O
- Page 456 and 457:
11.3. Creating Functions 11.3.1. de
- Page 458 and 459:
modules foo and bar, but can use th
- Page 460 and 461:
The main motivation behind decorato
- Page 462 and 463:
func = deco1(deco_arg)(deco2(func))
- Page 464 and 465:
11.4. Passing Functions The concept
- Page 466 and 467:
11.5. Formal Arguments A Python fun
- Page 468 and 469:
mandatory, whereas default argument
- Page 471 and 472:
11.6. Variable-Length Arguments The
- Page 473 and 474:
formal arg1: 1220 formal arg2: 740.
- Page 475 and 476:
We will leave a timeit() function a
- Page 477 and 478:
11.7. Functional Programming Python
- Page 479 and 480:
a(0,9) 9 >>> >>> b = lambda *z: z >
- Page 481 and 482:
In Figure 11-1, we observe our orig
- Page 483 and 484:
consisting of all the return values
- Page 485 and 486:
sequences together. This idiom was
- Page 487 and 488:
print 'the total is:', reduce((lamb
- Page 489 and 490:
some of those arguments, such as ma
- Page 491 and 492:
11.8. Variable Scope The scope of a
- Page 493 and 494:
print is_this_global def 11.8.3. Nu
- Page 495 and 496:
count2 = counter(100) >>> print cou
- Page 497 and 498:
For example, let us assume that fun
- Page 499 and 500:
name, e.g., post_logged() will log
- Page 501 and 502:
variable. Beginning in 2.1, the ent
- Page 503 and 504:
11.9. *Recursion A function is recu
- Page 505 and 506:
Now that we have our generator func
- Page 507 and 508:
count.next() 5 >>> count.next() 6 >
- Page 509 and 510:
11-3. Functions. In this exercise,
- Page 511 and 512:
11-14. *Recursion. We also looked a
- Page 513 and 514:
12.1. What Are Modules? A module al
- Page 515 and 516:
definitely vary as you go from syst
- Page 517 and 518:
Notice that each of the namespaces
- Page 519 and 520:
You will see just how useful they a
- Page 521 and 522:
It is possible to import specific m
- Page 523 and 524:
12.5. Features of Module Import 12.
- Page 525 and 526:
# impter.py # ############# import
- Page 527 and 528:
getting them "registered" (or rathe
- Page 529 and 530:
foo() We are going to ask for the d
- Page 531 and 532:
Furthermore, we can go down one mor
- Page 534 and 535:
12.8. Other Features of Modules 12.
- Page 536 and 537:
# overly massive handlers for the c
- Page 538 and 539:
12.9. Related Modules The following
- Page 540 and 541:
12-6. Extended Import. Create a new
- Page 542 and 543:
13.1. Introduction Before we get in
- Page 544 and 545:
class MyNewObjectType: 'define MyNe
- Page 546 and 547:
(We will add print statements to ou
- Page 548 and 549:
Each subclass must define its own c
- Page 550 and 551:
13.2. Object-Oriented Programming T
- Page 552 and 553:
interfacing with components of the
- Page 554 and 555:
derive; and class_suite consists of
- Page 556 and 557:
100 >>> C.foo = C.foo + 1 >>> print
- Page 558 and 559:
As you can tell, dir() returns a li
- Page 560 and 561:
ascertain the location of a class s
- Page 562 and 563:
In contrast for those of you using
- Page 564 and 565:
id(c1), id(c2), id(c3) # all refer
- Page 566 and 567:
13.6. Instance Attributes Instances
- Page 568 and 569:
wasWkEnd = HotelRoomCalc(119, 0.045
- Page 570 and 571:
The __dict__ attribute consists of
- Page 572 and 573:
However, we can only update the val
- Page 574 and 575:
As we have seen above, it is perilo
- Page 576 and 577:
override a parent method where you
- Page 578 and 579:
tcm = TestClassMethod() >>> TestCla
- Page 580 and 581:
13.10. Subclassing and Derivation C
- Page 582 and 583:
13.11. Inheritance Inheritance desc
- Page 584 and 585:
Now let us create the child class C
- Page 586 and 587:
class C(P): def __init__(self): sup
- Page 588 and 589:
def keys(self): return sorted(self.
- Page 590 and 591:
gc = GC() >>> gc.foo() # GC C1 P1 c
- Page 592 and 593:
class B(object): pass class C(objec
- Page 594 and 595:
isinstance(c2, C2) True >>> isinsta
- Page 596 and 597:
The super() function was added in 2
- Page 598 and 599:
13.13. Customizing Classes with Spe
- Page 600 and 601:
C.__*rshift__(self, obj) Right shif
- Page 602 and 603:
The Numeric Types set of special me
- Page 604 and 605:
We still have a few problems ... on
- Page 606 and 607:
The output is very nice, exactly wh
- Page 608 and 609:
1 #!/usr/bin/env python 2 3 class T
- Page 610 and 611:
from randseq import RandSeq >>> for
- Page 612 and 613:
Addition We define the addition ope
- Page 614 and 615:
[9 :: 'foofoofoo'] >>> b + e [3 ::
- Page 616 and 617:
which we raise in such cases. Lines
- Page 618 and 619:
13.15. *Delegation 13.15.1. Wrappin
- Page 620 and 621:
wrappedComplex.imag # imaginary att
- Page 622 and 623:
Creation time, modification time, a
- Page 624 and 625:
Wrapping a Specific Object with Enh
- Page 626 and 627:
13.16. Advanced Features of New-Sty
- Page 628 and 629:
preventing users from adding instan
- Page 630 and 631:
A descriptor is a class attribute,
- Page 632 and 633:
hide such a descriptor, just as you
- Page 634 and 635:
43 FileDescr.saved.remove(self.name
- Page 636 and 637:
If we try it out, we see that it sa
- Page 638 and 639:
def fget(self): return ~self.__x de
- Page 640 and 641:
print '*** Created class %r at: %s'
- Page 642 and 643:
44 __metaclass__ = ReqStrSugRepr 45
- Page 644 and 645:
... print '%s(%d, %d) = %d' % \ ...
- Page 646 and 647:
13.18. Exercises 13-1. Programming.
- Page 648 and 649:
cash.update(100000.4567) >>> cash 1
- Page 650 and 651:
13-9. Queue Class. A queue is a dat
- Page 652 and 653:
13-17. Subclassing Numeric Types. T
- Page 654 and 655:
Chapter 14. Execution Environment C
- Page 656 and 657:
Internally, BIFs are represented as
- Page 658 and 659:
__dict__ object. Later on in this c
- Page 660 and 661:
>>> c.foo # bound method object >>
- Page 662 and 663:
14.2. Code Objects Callables are a
- Page 664 and 665:
14.3.2. compile() compile() is a fu
- Page 666 and 667:
not a string representation of an i
- Page 668 and 669:
The above was performed with raw_in
- Page 670 and 671: -----------------------------------
- Page 672 and 673: A sequence was chosen; enter the se
- Page 674 and 675: them into real Python objects. Othe
- Page 676 and 677: import import2 And here are the con
- Page 678 and 679: $ python /usr/local/lib/python2x/CG
- Page 680 and 681: wait() Wait for child process to co
- Page 682 and 683: As you can see, popen() returns a f
- Page 684 and 685: 14.5.5. subprocess Module After Pyt
- Page 686 and 687: 14.6. Restricted Execution At one t
- Page 688 and 689: Calling sys.exit() causes the Pytho
- Page 690 and 691: 14.8. Miscellaneous Operating Syste
- Page 692 and 693: 14.9. Related Modules In Table 14.9
- Page 694 and 695: 14-9. Shells. Create a shell (opera
- Page 696 and 697: Chapter 15. Regular Expressions Cha
- Page 698 and 699: Python supports REs through the sta
- Page 700 and 701: 15.2. Special Symbols and Character
- Page 702 and 703: "\.". 15.2.3. Matching from the Beg
- Page 704 and 705: We will now introduce the most comm
- Page 706 and 707: \d+(\.\d*)? Strings representing si
- Page 708 and 709: match(pattern, string, flags=0) Att
- Page 710 and 711: m = re.match('foo', 'foo') # patter
- Page 712 and 713: 15.3.7. Matching Any Single Charact
- Page 714 and 715: ... >>> In the above code, we creat
- Page 716 and 717: Subgroup searches result in a more
- Page 718 and 719: saving the output to a whodata.txt
- Page 722 and 723: domain. After the final double-colo
- Page 724 and 725: patt = '\d+-\d+-\d+' >>> re.search(
- Page 726 and 727: 15.5. Exercises Regular Expressions
- Page 728 and 729: 15-19. Extract the complete timesta
- Page 730 and 731: 16.1. Introduction 16.1.1. What Is
- Page 732 and 733: The teller is, of course, the serve
- Page 734 and 735: 16.2. Sockets: Communication Endpoi
- Page 736 and 737: word "datagram." Because these sock
- Page 738 and 739: Method Description Server Socket Me
- Page 740 and 741: We do not implement this in our exa
- Page 742 and 743: it can immediately make a connectio
- Page 744 and 745: One way to create this "friendly" e
- Page 746 and 747: cs = socket() # create client socke
- Page 748 and 749: [a] Socket address families support
- Page 750 and 751: 16.4. *SocketServer Module SocketSe
- Page 752 and 753: Lines 1115 18 print 'waiting for co
- Page 754 and 755: $ And here is the server's: $ tsTse
- Page 756 and 757: This is a timestamp TCP server usin
- Page 758 and 759: calling the write() method of the t
- Page 761 and 762: 16.7. Exercises 16-1. Sockets. What
- Page 763 and 764: 3. Add logging capability to your n
- Page 765 and 766: 17.1. What Are Internet Clients? Be
- Page 767 and 768: 3. 4. Client logs in with username
- Page 769 and 770: pwd() Current working directory cwd
- Page 771 and 772:
31 f.quit() 32 return 33 print '***
- Page 773 and 774:
after-hours, using Python is a grea
- Page 775 and 776:
17.3.3. Python and NNTP Based on yo
- Page 777 and 778:
article (id) Also similar to body()
- Page 779 and 780:
16 except socket.gaierror, e: 17 pr
- Page 781 and 782:
deltas = [ x[1]-x[0] for x in parti
- Page 783 and 784:
17.4. Electronic Mail Electronic ma
- Page 785 and 786:
4. Make service request(s) Quit As
- Page 787 and 788:
data: (250, 'ok ; id=20051226235837
- Page 789 and 790:
... p.quit() Before we take a look
- Page 791 and 792:
any errors. Example 17.3. SMTP and
- Page 793 and 794:
17.5. Related Modules One of Python
- Page 795 and 796:
17.6. Exercises FTP 17-1. Simple FT
- Page 797 and 798:
E-MAIL 17-16. Threaded Newsreader.
- Page 799 and 800:
Miscellaneous c. d. e. - Is the mes
- Page 801 and 802:
Chapter 18. Multithreaded Programmi
- Page 804 and 805:
18.2. Threads and Processes 18.2.1.
- Page 806 and 807:
Those of you interested in the sour
- Page 808 and 809:
18.3.5. Python Threading Modules Py
- Page 810 and 811:
The same loops from onethr.py are e
- Page 812 and 813:
25 thread.start_new_thread(loop, 26
- Page 814 and 815:
18.5. tHReading Module We will now
- Page 816 and 817:
isDaemon() Return daemon flag of th
- Page 818 and 819:
In this example we pass in a callab
- Page 820 and 821:
19 print 'start loop', nloop, 'at:'
- Page 822 and 823:
16 def sum(x): 17 sleep(0.1) 18 if
- Page 824 and 825:
We use the Queue module to provide
- Page 826 and 827:
for random numbers!) Seriously, tho
- Page 828 and 829:
18.7. Exercises 18-1. Processes ver
- Page 830 and 831:
Chapter 19. GUI Programming Chapter
- Page 832 and 833:
distribution for specific instructi
- Page 834 and 835:
some applications use root rather t
- Page 836 and 837:
either from the Tkinter topics page
- Page 838 and 839:
Example 19.2. Button Widget Demo (t
- Page 840 and 841:
in the Label widget. The greater th
- Page 842 and 843:
PFAs fits perfectly into a situatio
- Page 844 and 845:
Lines 3033 These lines represent ou
- Page 846 and 847:
71 def doLS(self, ev=None): 72 erro
- Page 848 and 849:
Line-by-Line Explanation Lines 15 T
- Page 850 and 851:
The last pieces of code in listdir.
- Page 852 and 853:
Things are different once we start
- Page 854 and 855:
Our second example uses the Python
- Page 856 and 857:
Lines 537 Here we instantiate a Fra
- Page 858 and 859:
our primary widgets. This is exactl
- Page 860 and 861:
Qt/KDE-Related Modules PyQt Python
- Page 862 and 863:
19-9. Multithreaded Chat Applicatio
- Page 864 and 865:
20.1. Introduction This introductor
- Page 866 and 867:
As you can see from the figure, the
- Page 868 and 869:
net_loc can be broken down into sev
- Page 870 and 871:
urlunparse(urltup) Unparses a tuple
- Page 872 and 873:
urlretrieve(urlstr, localfile=None,
- Page 874 and 875:
87 if eachLink not in self.q: 88 se
- Page 876 and 877:
urllib Functions Description urlope
- Page 878 and 879:
(). This code was inspired by Mike
- Page 880 and 881:
parse the newly downloaded page and
- Page 882 and 883:
20.4. CGI: Helping Web Servers Proc
- Page 884 and 885:
Finally, as you can probably guess,
- Page 886 and 887:
This HTML file presents a form to t
- Page 888 and 889:
Example 20.4. Results Screen CGI co
- Page 890 and 891:
Both friends.html and friends1.py a
- Page 892 and 893:
The other reason for creating actio
- Page 894 and 895:
12 ERROR 13 %s 14 16 ''' 17 18 def
- Page 896 and 897:
link with all the existing informat
- Page 898 and 899:
Now the user is able to make change
- Page 900 and 901:
This script outputs Unicode strings
- Page 902 and 903:
When more than one checkbox is subm
- Page 904 and 905:
Figure 20-16. Submitting our advanc
- Page 906 and 907:
Figure 20-17. Results page generate
- Page 908 and 909:
This script has one main class that
- Page 910 and 911:
113 MAXBYTES = 1024 114 langlist =
- Page 912 and 913:
all the information and sends the f
- Page 914 and 915:
20.8. Web (HTTP) Servers Until now,
- Page 916 and 917:
33 main() This server subclasses Ba
- Page 918 and 919:
[b] Interface to the non-validating
- Page 920 and 921:
20.10. Exercises 20-1. urllib Modul
- Page 922 and 923:
20-19. Electronic Commerce Engine.
- Page 924 and 925:
Chapter 21. Database Programming Ch
- Page 926 and 927:
When you query a database, you can
- Page 928 and 929:
Python world. As a software enginee
- Page 930 and 931:
This string (not float) indicates t
- Page 932 and 933:
DatabaseError Database error DataEr
- Page 934 and 935:
callproc( func[, args]) Call a stor
- Page 936 and 937:
● http://python.org/topics/databa
- Page 938 and 939:
cur.execute("INSERT INTO users VALU
- Page 940 and 941:
'', None, '{pgsql=C*T*/pgsql}'] ['t
- Page 942 and 943:
23 24 if db == 'sqlite': 25 try: 26
- Page 944 and 945:
140 db = setup() 141 print '*** Con
- Page 946 and 947:
whereas Gadfly does not, so rows ha
- Page 948 and 949:
21.3. Object-Relational Managers (O
- Page 950 and 951:
54 def insert(self): 55 d = [dict(z
- Page 952 and 953:
44 def create(self): 45 Users = sel
- Page 954 and 955:
the rows from the database and pret
- Page 956 and 957:
The code works something like this:
- Page 958 and 959:
We hope that we have provided you w
- Page 960 and 961:
adodbapi http://adodbapi.sf.net Syb
- Page 962 and 963:
Chapter 22. Extending Python Chapte
- Page 964 and 965:
● Added/extra (non-Python) functi
- Page 966 and 967:
The following code represents our l
- Page 968 and 969:
usr/include/python2.x, where the "2
- Page 970 and 971:
} res = PyArg_ParseTuple(args, "i",
- Page 972 and 973:
PyArg_ParseTupleAndKeywords() with
- Page 974 and 975:
$ python setup.py build running bui
- Page 976 and 977:
1 #include 2 #include 3 #include
- Page 978 and 979:
after its reference count has decre
- Page 980 and 981:
22.3. Related Topics SWIG There is
- Page 982 and 983:
22.4. Exercises 22-1. Extending Pyt
- Page 984 and 985:
23.1. Web Services There are many W
- Page 986 and 987:
The field names are given in the or
- Page 988 and 989:
23.2. Programming Microsoft Office
- Page 990 and 991:
This script launches Excel and writ
- Page 992 and 993:
23.2.3. Microsoft Word The next dem
- Page 994 and 995:
Applying PowerPoint in an applicati
- Page 996 and 997:
This script launches Outlook, creat
- Page 998 and 999:
Then when you are trying to send a
- Page 1000 and 1001:
Lines 113 We import all of the attr
- Page 1002 and 1003:
23.3. Python and Java Programming w
- Page 1004 and 1005:
Example 23.8. Swing "Hello World" i
- Page 1006 and 1007:
23.4. Exercises Web Services 23-1.
- Page 1008 and 1009:
23-15. Excel Cell Formatting. In th
- Page 1010 and 1011:
23-21. Python and Jython. Find a Py
- Page 1012 and 1013:
Chapter 22 Chapter 23
- Page 1014 and 1015:
or print i, s[i] for i, x in enumer
- Page 1016 and 1017:
Chapter 4 1. Python objects All Pyt
- Page 1018 and 1019:
When i % 2 == 0, it's even (divisib
- Page 1020 and 1021:
Chapter 7 1. Dictionary methods dic
- Page 1022 and 1023:
Chapter 8 3. range() built-in funct
- Page 1024:
Chapter 10 1. Raising exceptions e)
- Page 1027 and 1028:
Chapter 12 2. Importing attributes
- Page 1029 and 1030:
Chapter 14 1. Callable objects Func
- Page 1031 and 1032:
9. Python floats [0-9]+(\.[0-9]*)?
- Page 1033 and 1034:
Chapter 17 20. Identifiers pass is
- Page 1035 and 1036:
Chapter 19 1. Client/server archite
- Page 1037 and 1038:
Chapter 21 1. Extending Python ●
- Page 1039 and 1040:
Chapter 23 3. Web services and the
- Page 1041 and 1042:
Python Keywords Table B.1 lists Pyt
- Page 1043 and 1044:
[a] Boolean comparisons return eith
- Page 1045 and 1046:
% Modulo/remainder • • • •
- Page 1047 and 1048:
isnumeric() • isspace() • istit
- Page 1049 and 1050:
String Format Operator Conversion S
- Page 1051 and 1052:
- Use left justification + Use a pl
- Page 1053 and 1054:
string.isdigit() [b] [c] Returns tr
- Page 1055 and 1056:
List Type Built-in Methods In Table
- Page 1057 and 1058:
[c] New in Python 2.3. [d] New in P
- Page 1059 and 1060:
s.copy() Copy operation: return (sh
- Page 1061 and 1062:
[d] Encoding that this file useswhe
- Page 1063 and 1064:
OverflowError Calculation exceeded
- Page 1065:
[i] Warning about FutureWarning con
- Page 1068 and 1069:
[a] Get attribute; getattr() built-
- Page 1070 and 1071:
__radd__, or __iadd__. [f] New in P
- Page 1072 and 1073:
= • • • • • • • •
- Page 1074 and 1075:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1076 and 1077:
| (pipe symbol) 2nd 3rd |= (pipe eq
- Page 1078 and 1079:
arguments class methods command-lin
- Page 1080 and 1081:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1082 and 1083:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1084 and 1085:
instance attributes vs. methods mod
- Page 1086 and 1087:
compound statements concatenation (
- Page 1088 and 1089:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1090 and 1091:
copy( ) creating 2nd dict( ) exact
- Page 1093 and 1094:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1095 and 1096:
sys module try statement with multi
- Page 1097 and 1098:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1099 and 1100:
float( ) built-in function 2nd floa
- Page 1101 and 1102:
eturn values standard type 2nd vari
- Page 1103 and 1104:
grouping 2nd groups( ) method GTK+
- Page 1105 and 1106:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1107 and 1108:
installing Python instance attribut
- Page 1109 and 1110:
through files iterators about any n
- Page 1111 and 1112:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1113 and 1114:
list( ) built-in function 2nd list(
- Page 1115 and 1116:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1117 and 1118:
for re module group(s) invoking 2nd
- Page 1119 and 1120:
modulus operator MRO [See method re
- Page 1121 and 1122:
and OOP classic classes vs. descrip
- Page 1123 and 1124:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1125 and 1126:
intersection update ( &= ) key-look
- Page 1127 and 1128:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1129 and 1130:
PyQt PyQtGPL Pyrex Python Enhanceme
- Page 1131 and 1132:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1133 and 1134:
tuple elements/tuples repetition li
- Page 1135 and 1136:
for statement used with keys for 2n
- Page 1137 and 1138:
about as original Internet protocol
- Page 1139 and 1140:
ules for suites static data static
- Page 1141 and 1142:
subtraction ( - ) operator suites 2
- Page 1143 and 1144:
definition of examples exiting glob
- Page 1145 and 1146:
categorizing standard function to c
- Page 1147:
Universal NEWLINE Support (UNS) 2nd
- Page 1150 and 1151:
Index [SYMBOL] [A] [B] [C] [D] [E]
- Page 1152 and 1153:
wxGlade wxPython 2nd 3rd wxWidgets
- Page 1154 and 1155:
Index [SYMBOL] [A] [B] [C] [D] [E]