Download - Olivetti UK
Download - Olivetti UK
Download - Olivetti UK
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Authentication<br />
Action Specifying the authentication<br />
LE 05 Command Center<br />
Recommendations When generally a person-specific authentication is wanted for the device.<br />
Pre-conditions • Administrative access to the Command Center<br />
• Local user accounts (see page 94) or network accounts via AD S (Active<br />
Di Directory t SServices) i ) must tb be available. il bl<br />
Notes As very detailed knowledge of networks is required for this, it is recommended that<br />
the<br />
network administrator is present for the setup.<br />
(See “Authentication models”)<br />
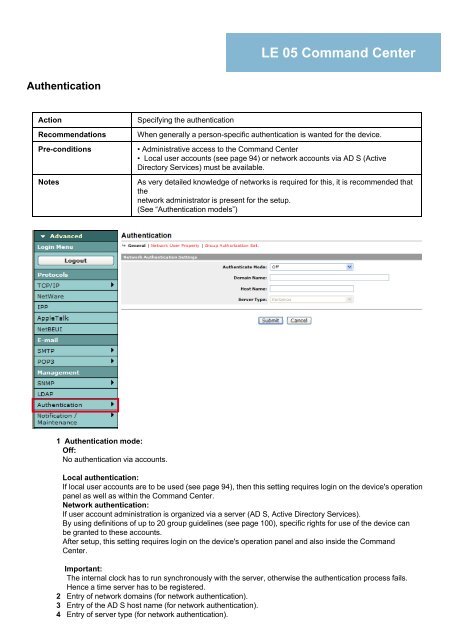
1 Authentication mode:<br />
Off:<br />
No authentication via accounts.<br />
Local authentication:<br />
If local user accounts are to be used (see page 94), then this setting requires login on the device's operation<br />
panel as well as within the Command Center.<br />
Network authentication:<br />
If user account administration is organized via a server (AD S, Active Directory Services).<br />
By using definitions of up to 20 group guidelines (see page 100), specific rights for use of the device can<br />
be granted to these accounts.<br />
After setup, this setting requires login on the device's operation panel and also inside the Command<br />
Center Center.<br />
Important:<br />
The internal clock has to run synchronously with the server, otherwise the authentication process fails.<br />
Hence a time server has to be registered.<br />
2 Entry of network domains (for network authentication).<br />
3 Entry of the AD S host name (for network authentication).<br />
4 Entry of server type (for network authentication).