Forensic Analysis Using FTK
Forensic Analysis Using FTK
Forensic Analysis Using FTK
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
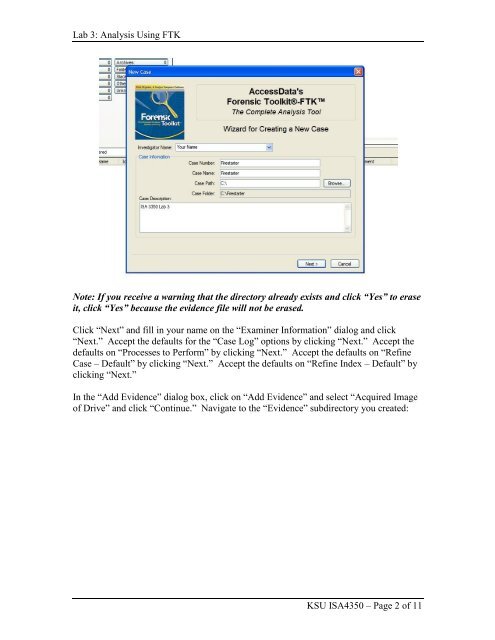
Lab 3: <strong>Analysis</strong> <strong>Using</strong> <strong>FTK</strong><br />
Note: If you receive a warning that the directory already exists and click “Yes” to erase<br />
it, click “Yes” because the evidence file will not be erased.<br />
Click “Next” and fill in your name on the “Examiner Information” dialog and click<br />
“Next.” Accept the defaults for the “Case Log” options by clicking “Next.” Accept the<br />
defaults on “Processes to Perform” by clicking “Next.” Accept the defaults on “Refine<br />
Case – Default” by clicking “Next.” Accept the defaults on “Refine Index – Default” by<br />
clicking “Next.”<br />
In the “Add Evidence” dialog box, click on “Add Evidence” and select “Acquired Image<br />
of Drive” and click “Continue.” Navigate to the “Evidence” subdirectory you created:<br />
KSU ISA4350 – Page 2 of 11