Firewall - Kaspersky Lab
Firewall - Kaspersky Lab
Firewall - Kaspersky Lab
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Kaspersky</strong> Internet Security 2012<br />
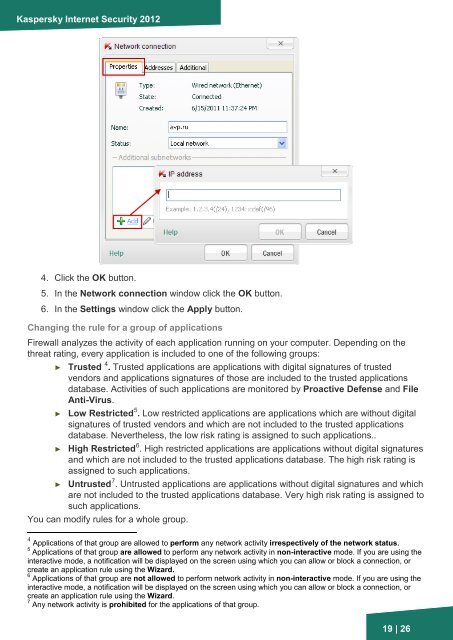
4. Click the OK button.<br />
5. In the Network connection window click the OK button.<br />
6. In the Settings window click the Apply button.<br />
Changing the rule for a group of applications<br />
<strong>Firewall</strong> analyzes the activity of each application running on your computer. Depending on the<br />
threat rating, every application is included to one of the following groups:<br />
► Trusted 4 . Trusted applications are applications with digital signatures of trusted<br />
vendors and applications signatures of those are included to the trusted applications<br />
database. Activities of such applications are monitored by Proactive Defense and File<br />
Anti-Virus.<br />
5<br />
► Low Restricted . Low restricted applications are applications which are without digital<br />
signatures of trusted vendors and which are not included to the trusted applications<br />
database. Nevertheless, the low risk rating is assigned to such applications..<br />
6<br />
► High Restricted . High restricted applications are applications without digital signatures<br />
and which are not included to the trusted applications database. The high risk rating is<br />
assigned to such applications.<br />
7<br />
► Untrusted . Untrusted applications are applications without digital signatures and which<br />
are not included to the trusted applications database. Very high risk rating is assigned to<br />
such applications.<br />
You can modify rules for a whole group.<br />
4 Applications of that group are allowed to perform any network activity irrespectively of the network status.<br />
5 Applications of that group are allowed to perform any network activity in non-interactive mode. If you are using the<br />
interactive mode, a notification will be displayed on the screen using which you can allow or block a connection, or<br />
create an application rule using the Wizard.<br />
6 Applications of that group are not allowed to perform network activity in non-interactive mode. If you are using the<br />
interactive mode, a notification will be displayed on the screen using which you can allow or block a connection, or<br />
create an application rule using the Wizard.<br />
7 Any network activity is prohibited for the applications of that group.<br />
19 | 26