UNIVERSITY OF KERALA - Marian Engineering College
UNIVERSITY OF KERALA - Marian Engineering College
UNIVERSITY OF KERALA - Marian Engineering College
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
B.Tech Comp. Sc. & Engg., University of Kerala 77<br />
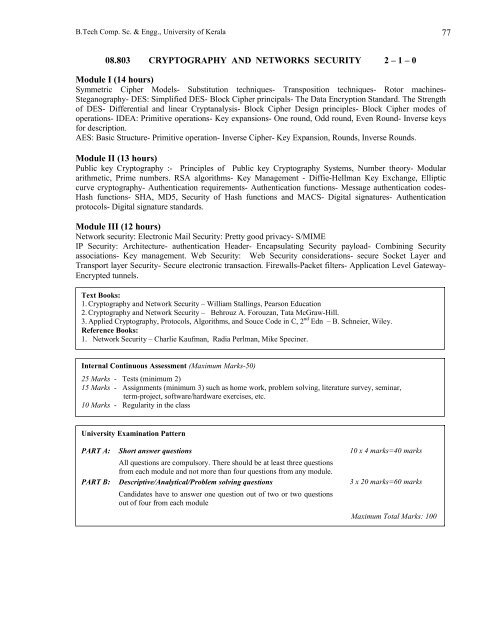
08.803 CRYPTOGRAPHY AND NETWORKS SECURITY 2 – 1 – 0<br />
Module I (14 hours)<br />
Symmetric Cipher Models- Substitution techniques- Transposition techniques- Rotor machines-<br />
Steganography- DES: Simplified DES- Block Cipher principals- The Data Encryption Standard. The Strength<br />
of DES- Differential and linear Cryptanalysis- Block Cipher Design principles- Block Cipher modes of<br />
operations- IDEA: Primitive operations- Key expansions- One round, Odd round, Even Round- Inverse keys<br />
for description.<br />
AES: Basic Structure- Primitive operation- Inverse Cipher- Key Expansion, Rounds, Inverse Rounds.<br />
Module II (13 hours)<br />
Public key Cryptography :- Principles of Public key Cryptography Systems, Number theory- Modular<br />
arithmetic, Prime numbers. RSA algorithms- Key Management - Diffie-Hellman Key Exchange, Elliptic<br />
curve cryptography- Authentication requirements- Authentication functions- Message authentication codes-<br />
Hash functions- SHA, MD5, Security of Hash functions and MACS- Digital signatures- Authentication<br />
protocols- Digital signature standards.<br />
Module III (12 hours)<br />
Network security: Electronic Mail Security: Pretty good privacy- S/MIME<br />
IP Security: Architecture- authentication Header- Encapsulating Security payload- Combining Security<br />
associations- Key management. Web Security: Web Security considerations- secure Socket Layer and<br />
Transport layer Security- Secure electronic transaction. Firewalls-Packet filters- Application Level Gateway-<br />
Encrypted tunnels.<br />
Text Books:<br />
1. Cryptography and Network Security – William Stallings, Pearson Education<br />
2. Cryptography and Network Security – Behrouz A. Forouzan, Tata McGraw-Hill.<br />
3. Applied Cryptography, Protocols, Algorithms, and Souce Code in C, 2 nd Edn – B. Schneier, Wiley.<br />
Reference Books:<br />
1. Network Security – Charlie Kaufman, Radia Perlman, Mike Speciner.<br />
Internal Continuous Assessment (Maximum Marks-50)<br />
25 Marks - Tests (minimum 2)<br />
15 Marks - Assignments (minimum 3) such as home work, problem solving, literature survey, seminar,<br />
term-project, software/hardware exercises, etc.<br />
10 Marks - Regularity in the class<br />
University Examination Pattern<br />
PART A: Short answer questions 10 x 4 marks=40 marks<br />
All questions are compulsory. There should be at least three questions<br />
from each module and not more than four questions from any module.<br />
PART B: Descriptive/Analytical/Problem solving questions 3 x 20 marks=60 marks<br />
Candidates have to answer one question out of two or two questions<br />
out of four from each module<br />
Maximum Total Marks: 100