Defending Human Rights: A Resource Book for Human
Defending Human Rights: A Resource Book for Human
Defending Human Rights: A Resource Book for Human
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
that limitations prevail, and those limitations on<br />
security are the same as those on the human<br />
rights work: scarce resources, few personnel,<br />
improvisation, a high level of pressure and<br />
repression, etc.<br />
Security strategies and work space: A<br />
consent/dissuasion triangle<br />
All security strategies can be summarized in one<br />
sentence: to keep the work space open. For that<br />
we need to seek, as a minimum, consent (of<br />
government, of armed actors and civil society) and<br />
ideally acceptance (a further step).<br />
Speaking strictly in terms of security, the defenders´<br />
work space requires certain consent by the parties<br />
in conflict, especially the armed ones, and ideally a<br />
request from some part of the sectors affected by<br />
the conflict. This consent can be explicit (a <strong>for</strong>mal<br />
permit from the authorities) or implicit, and will<br />
be more solid if an armed actor perceives some<br />
than one armed benefits actor. from the defenders´ work, or lower if he<br />
perceives costs. In this case, the consent will be<br />
given by the political costs carried by an attack on<br />
The level of risk of an NGO is in accordance with the<br />
received threats and vulnerability to those threats,<br />
he perceives costs. In this case, the consent will be given by the political as can costs be seen carried in the by following equation 5 :<br />
n the defenders. All this is especially relevant when defenders are working in a scenario<br />
Risk = threats x vulnerability<br />
pace can be represented as a triangle which relates the continuum consent-acceptance<br />
the defenders. All this is especially relevant when<br />
tinuum deterrence-persuasion:<br />
defenders are working in a scenario with more than<br />
one armed actor.<br />
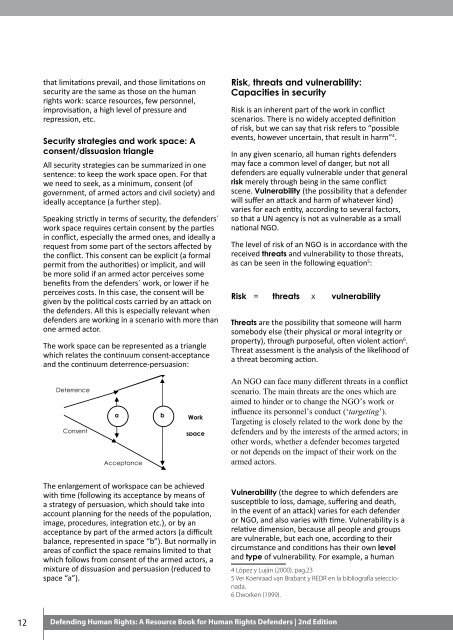
The work space can be represented as a triangle<br />
which relates the continuum consent-acceptance<br />
and the continuum deterrence-persuasion:<br />
Deterrence<br />
Consent<br />
Persuasion<br />
a<br />
Acceptance<br />
b<br />
Work<br />
space<br />
Risk, threats and vulnerability:<br />
Capacities in security<br />
Risk is an inherent part of the work in conflict<br />
scenarios. There is no widely accepted definition<br />
of risk, but we can say that risk refers to “possible<br />
events, however uncertain, that result in harm” 4 .<br />
In any given scenario, all human rights defenders<br />
may face a common level of danger, but not all<br />
defenders are equally vulnerable under that general<br />
risk merely through being in the same conflict<br />
scene. Vulnerability (the possibility that a defender<br />
will suffer an attack and harm of whatever kind)<br />
varies <strong>for</strong> each entity, according to several factors,<br />
so that a UN agency is not as vulnerable as a small<br />
national NGO.<br />
Threats are the possibility that someone will harm<br />
somebody else (their physical or moral integrity or<br />
property), through purposeful, often violent action 6 .<br />
Threat assessment is the analysis of the likelihood of<br />
a threat becoming action.<br />
An NGO can face many different threats in a conflict<br />
scenario. The main threats are the ones which are<br />
aimed to hinder or to change the NGO’s work or<br />
influence its personnel’s conduct (‘targeting’).<br />
Targeting is closely related to the work done by the<br />
defenders and by the interests of the armed actors; in<br />
other words, whether a defender becomes targeted<br />
or not depends on the impact of their work on the<br />
armed actors.<br />
The enlargement of workspace can be achieved<br />
with time (following its acceptance by means of Vulnerability (the degree to which defenders are<br />
a strategy of persuasion, which should take into susceptible to loss, damage, suffering and death,<br />
ment of workspace account can planning be achieved <strong>for</strong> the with needs time of the (following population, its acceptance in the by event means of an of a attack) varies <strong>for</strong> each defender<br />
persuasion, image, which should procedures, take into integration account etc.), planning or by <strong>for</strong> an the needs of<br />
or<br />
the<br />
NGO,<br />
population,<br />
and also varies with time. Vulnerability is a<br />
cedures, integration<br />
acceptance<br />
etc.),<br />
by<br />
or<br />
part<br />
by an<br />
of the<br />
acceptance<br />
armed actors<br />
by part<br />
(a<br />
of<br />
difficult relative dimension, because all people and groups<br />
the armed actors (a difficult<br />
balance, represented in space “b”). But normally in are vulnerable, but each one, according to their<br />
presented in areas space of "b"). conflict But normally the space in remains areas of limited conflict to the that space remains circumstance limited and to conditions has their own level<br />
follows from which consent follows of the from armed consent actors, of a the mixture armed of actors, dissuasion a and and persuasion type of vulnerability. For example, a human<br />
space "a"). mixture of dissuasion and persuasion (reduced to 4 López y Luján (2000), pag.23<br />
space “a”).<br />
5 Ver Koenraad van Brabant y REDR en la bibliografía seleccionada.<br />
6 Dworken (1999).<br />
12 <strong>Defending</strong> <strong>Human</strong> <strong>Rights</strong>: A <strong>Resource</strong> <strong>Book</strong> <strong>for</strong> <strong>Human</strong> <strong>Rights</strong> Defenders | 2nd Edition<br />
ats and vulnerability: Capacities in security